A few days ago, we had a new challenge where we should find out what techniques or tips were being used lastly to install malware. To get this information, we only had a compressed file that had been captured.
When we open the file attachment.rar we see that there are three images of Roman ruins: “0.jpeg”, “1.png” y “3.jpg”.
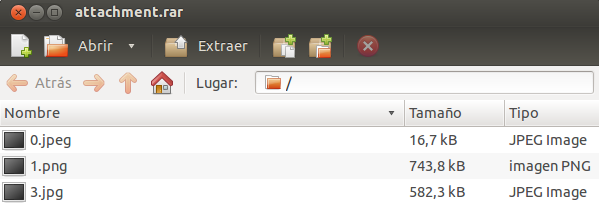
Paying attention on these pictures, the only strange thing we observe it is that there are some Roman numeral in the bottom right corner of two of the pictures (“II” y “IV”) and also that it seems there is one picture missing (number “2”), because after number “1” we only have number “3”.
Knowing that it is possible the lack of an image, we can analyse how a rar file is created and see that it is constructed by a main header and a new header (file header) for each of the files compressed, where the “0x74” value indicates that it is a file’s header, followed by the file’s name and the compressed file. But if we analyse our rar file, we see that this rule is not applied because we find “0x00” instead of “0x74”, causing the no detection of the compressed file.
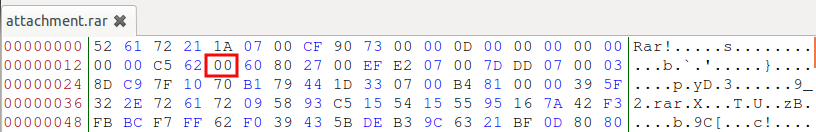
So, to be able to see the missing file, it will be enough replacing the “0x00” value for “0x74” in the file’s header.
If someone would not realise that one file was missing, knowing how a rar file is constructed will be enough to detect the file because the hidden file’s name “9_2.rar” could be seen relatively easy.
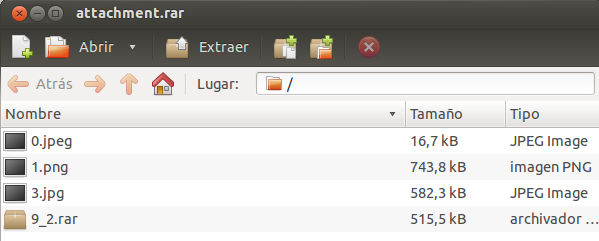
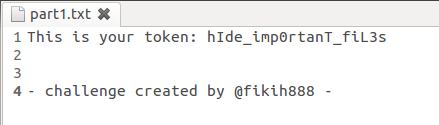
Once we have done it, we see that a new file named “9_2.rar” appears, which is a new rar file with a new image and a txt file that contains the token we needed to open the first validator (validator1.rar) and solve the first part of the challenge.
Once we have all the images, we see that they all reference to Rome and one of them is a Caesar picture. So it is very likely that it could be something encrypted with “Caesar cipher”.
If we analyse the EXIF data in the pictures, it looks like the data has been modified, considering that the real resolution of the image doesn’t match with the resolution in the EXIF data, that the date indicates all the pictures have been taken in June (month that has not arrived yet) and that them all have been taken at the same instant (although we see the are from different places and moments).
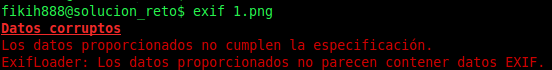
As a note, I would like to stand out that PNG images doesn’t support EXIF metadata, but they allow to add information as “key=value”, getting the “same” functionality. In this challenge, if we try to get EXIF metadata from the PNG image following the specification, it is possible to get an error as in the next capture:
But if we did this with a tool like exiv2 we would have no problem.
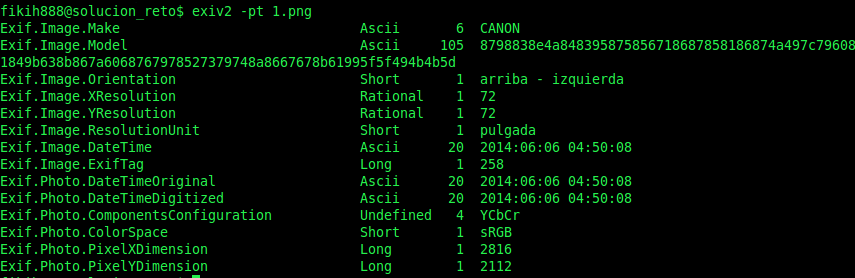
We decided to use a PNG image to show that it is also possible use metadata in it :)
Looking carefully about the camera data, we see something that looks to be hexadecimal, but when we convert it to ASCII, it has no sense. So maybe, it could be encrypted with “Caesar cipher” (using only hexadecimal characters).

Personally, I don’t know any Caesar cipher only for hexadecimal, so we have decided to create one.
Supposing that it is encrypted with Caesar, we only need to know the shift that is being used, and at this moment it is when the Roman numerals has sense. This numbers indicate the shift for each image (“2”, “3” and “4” for images “1.png”, “2” y “3.jpg” respectively). So decrypting each message and converting the result to ASCII, we can obtain the next:
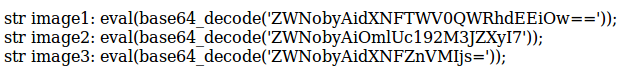
Once the messages are decrypted, we see they are php instructions with a part codified in base64, therefore executing these lines in php, we get the messages for each of the pictures.

Where ordering them according to the picture number, we get the token that opens the second validator (validator2.rar): “usEMetAdatA:iTs_v3rY_usEfuL”.
As extra information, I will say that the EXIF metadata had been used recently to install malware (see this post, only in Spanish) and for this reason I decided to use something similar in this challenge.
And with this we finish the solution for the challenge. Congratulations to those people who solved the challenge and those who did not, I hope you have had a great time trying it and had learned new techniques to hide information ;)
(Congrats to Kachakil, that again, solved easily the challenge)
