(Please note this post has been translated, so some strings may appear in Spanish, mainly services names)
In previous posts we have already talked about Dionaea (Spanish), a low-interaction honeypot that offers a variety of network services. The main problem we face when deploying a honeypot is how to customize its services to make them undetectable by scanning tools. The more an attacker takes to detect its interacting with a honeypot, the more likely we will be able analyze its methodology, capture exploits, binaries, etc.
We will install Dionaea and modify some of its services to avoid identification by the network scanner most popular: Nmap.
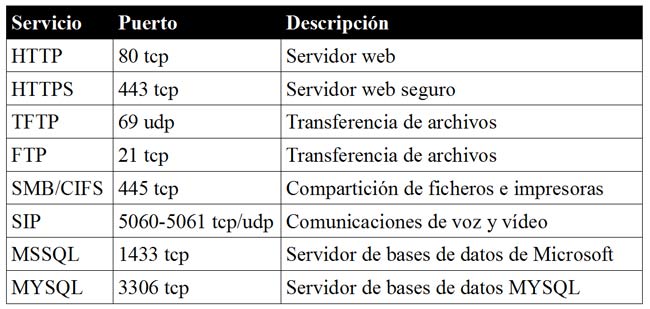
We can get Dionaea from its project page, with the steps for its installation. In our case we used Ubuntu 12.04 as the base operating system. Active services by default are:
Once installed, we launch a Nmap scanner to see what services are identified and associated with Dionaea, thanks to nmap fingerprinting ability:
# nmap -v -O -sV -sT -sU 192.168.100.10
In the summary of the scan output shown below we can see that some of the services are identified and associated with Dionaea. One of the first steps in a penetration test is the discovery of assets in a network and its services, so if an attacker with nmap scans the network, she will detect the existence of the honeypot and probably stop the attack. Therefore, we will not capture all the information we want.
Note: Nmap version used is 6.00. Other versions may modify the detectability depending on the fingerprint signatures.
PORT STATE SERVICE VERSION 21/tcp open ftp Dionaea honeypot ftpd 80/tcp open http ? 135/tcp open msrpc ? 443/tcp open ssl/https ? 445/tcp open microsoft-ds Dionaea honeypot smbd 1433/tcp open ms-sql-s Dionaea honeypot MS-SQL server 3306/tcp open mysql MySQL 5.0.54 5060/tcp open sip (SIP end point; Status: 200 OK) 5061/tcp open ssl/sip (SIP end point; Status: 200 OK) 69/udp open|filtered tftp 5060/udp open sip (SIP end point; Status: 200 OK)
To customize services to avoid detection by nmap, we must know how Nmap identifies them. When Nmap tries to find the product behind a service, it compare service response with the patterns included in the file nmap-service-probes (located in /usr/share/nmap/). In the URL http://nmap.org/book/vscan-technique.html we can see the process followed by Nmap to detect services. Therefore, if we can identify and modify Dionaea services based on these patterns, we can ensure that the service is not identified as Dionaea, or simulate any other product. For example, we can change an Apache server to an IIS or Tomcat.
We search for the Dionaea FTP Service in the file nmap-service-probes and we will find the following line:
match ftp m|^220 Welcome to the ftp service\r\n| p/Dionaea honeypot ftpd/
This line contains a characteristic welcome of Dionaea, which is shown to an FTP client when connecting to the service and also the product it is associated (Dionaea). Therefore, we need to modify this message so that nmap can not associate it with Dionaea. You need to edit /usr/lib/dionaea/python/dionaea/ftp.py to change that message.
This file, written in Python, is the Dionaea FTP server implementation. Each service implemented by the honeypot is divided into modules, what will ease us the customization of the services.
We can take advantage of the traces contained in nmap-service-probes and change the message to show a ProFTPD server. We change the initial message of Dionaea in ftp.py by a ProFTPD one :
self.reply(WELCOME_MSG, "Welcome to the ftp service") self.reply(WELCOME_MSG, "ProFTPD 1.2.8 Server")
The next service to modify is microsoft-ds (SMB/CIFS). In this case, if we look for the corresponding pattern in nmap-service-probes, we can see how it looks for a match in the response from the server during the connection establishment. This coincidence or pattern is:
\x00\x34\0W\0O\0R\0K\0G\0R\0O\0U\0P\0\0\0H\0O\0M\0E\0U\0S\0E\0R\0-\0.\0.\0.\0.\0.\0.
This corresponds to the fields that represent the domain name and the computer, ie, if the domain name is WORKGROUP and the computer name is HOMEUSER-XXXXXX, where X is any alphanumeric character, then the service is identified as a service of Dionaea.
To camouflage the sharing and printer service in Windows, we just need to change the values of fields OemDomainName and ServerName in /usr/lib/dionaea/python/dionaea/smb/include/smbfields.py. Let’s change the following settings to avoid being identified:
OemDomainName: WORKGROUP → MIDOMINIO ServerName: HOMEUSER-3AF6FE → EQUIPO-TEST
The third identified service is the system based on Microsoft SQL Server database on port 1433. If we look for this service in the nmap pattern file, we see a string in hexadecimal:
match ms-sql-s m|^\x04\x01\x00\x2b\x00\x00\x00\x00\x00\x00\x1a\x00\x06\x01\x00\x20\x00 \x01\x02\x00\x21\x00\x01\x03\x00\x22\x00\x00\x04\x00\x22\x00\x01\xff\x08\x00\x02\x10 \x00\x00\x02\x00\x00| p/Dionaea honeypot MS-SQL server/
This string corresponds the honeypot response to a pre-login TDS package (Tabular Data Streams) in the process of connecting to the database service. If we do a packet capture with a sniffer and analyze the connections, we can see how this string is the field Token Type (in hexadecimal encoding) with the value 0x00.
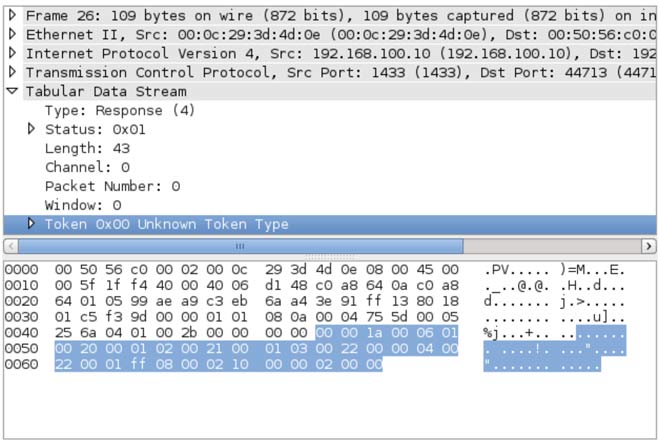
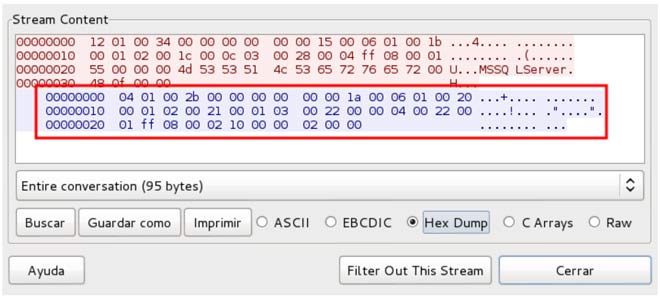
If we change the value 0x00 of the field Token Type, we will avoid nmap scan detection. This field is modified in the file /usr/lib/dionaea/python/dionaea/mssql/mssql.py. Let’s change the value to 0xAA, which corresponds to an error message, although we could set any other. A list of allowed values for this field can be found in FreeTDS .
r.VersionToken.TokenType = 0x00 → 0xAA
Finally, the HTTPS service is not identified in the scan, but we just need to go to the URL of the web server and check the certificate:
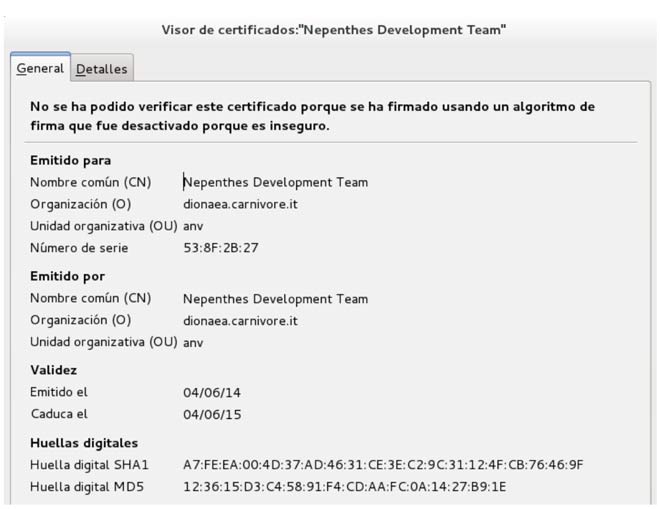
The certificate is issued by Nepenthes Development Team, the creators of the precursor of Dionaea honeypot (Nepenthes), besides showing the URL of Dionaea project. So we need to generate a certificate with some more “credibility” and replace the default one. Because the certificate is generated at compile time, we need to change the certificate information in the file /src/connection.c before compiling the honeypot.
After modifying the above data services, we perform another port scan to the honeypot:
PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.2.8 80/tcp open http ? 135/tcp open msrpc ? 443/tcp open ssl/https ? 445/tcp open microsoft-ds ? 1433/tcp open ms-sql-s ? 3306/tcp open mysql MySQL 5.0.54 5060/tcp open sip (SIP end point; Status: 200 OK) 5061/tcp open sip-tls ? 69/udp open|filtered tftp 5060/udp open sip (SIP end point; Status: 200 OK)
As we can see , the services described are no longer identified as Dionaea services, so we managed to avoid that a simple Nnmap scan detects our honeypot. If we really want to use the honeypot to detect non-automated attacks and fool an attacker, then we need to perform a more detailed customization of the honeypot services, in order to generate a much more realistic service environment.

First, it can’t seem to get a handle on its own numbers.
Easing into a stock position through multiple purchasesa common risk management techniquewill cost
you money if the stock goes straight up after your initial
purchase. t particularly interested in investing in that
company.