Malcom (Malware Communication Analyzer) is a tool I have been using for quite some time now and, even though it is quite well documented in several sites, I thought convenient to dedicate an article because on its latest actualizations it has become more stable and consistent.
Its main objective is to analyze the network traffic connections in a graphic way while simultaneously crossing data with public or private malware feeds in order to identify malicious nodes (C&C servers, for example); how the malware tries to communicate with them and analyze possible behavior patterns, understand P2P networks or to observe DNS Fast-Flux type infrastructures.
As an example of its inner workings, I’ll use a Pcap from this “Malware Traffic Analysis” exercise, a website I recommend for those who want to practice with traffic analysis exercises.
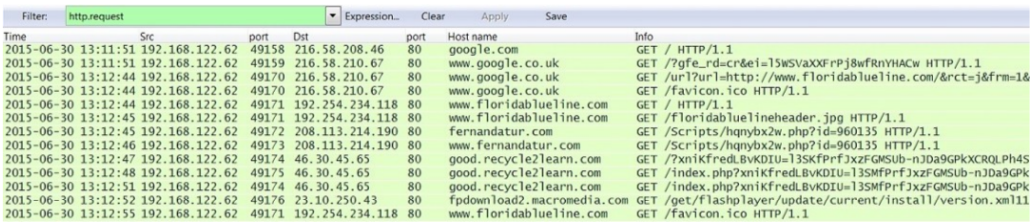
In this exercise Pcap, if we filter by http.request using Wireshark, we can see a sequence of all the http requests that the infected machine does and therefore we can identify the suspicious ones:
If we check this against the alerts that IDS provide, for example uploading the Pcap to Virustotal:
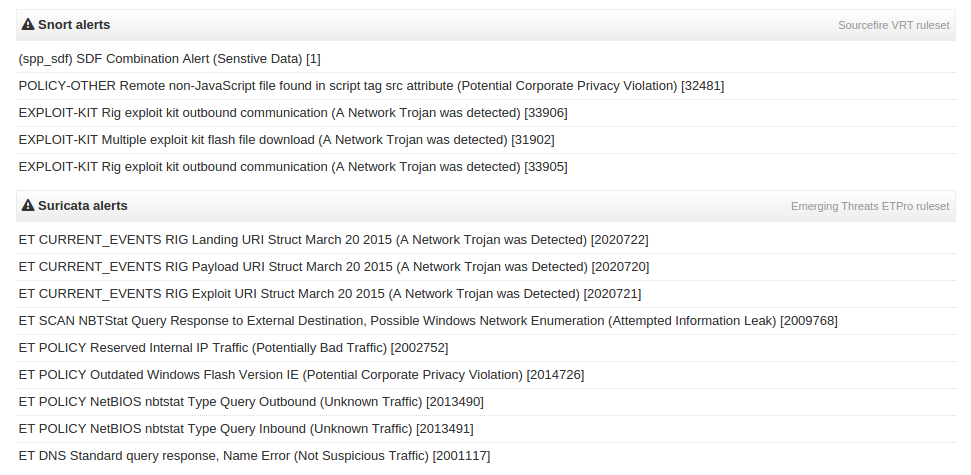
We can see that our infected IP, 192.168.122.62, raises an alarm when visiting the IP 192.254.234.118:80 of the type:
“POLICY-OTHER Remote non-JavaScript file found in script tag src attribute”
(Talos (Sourcefire VRT) signature)
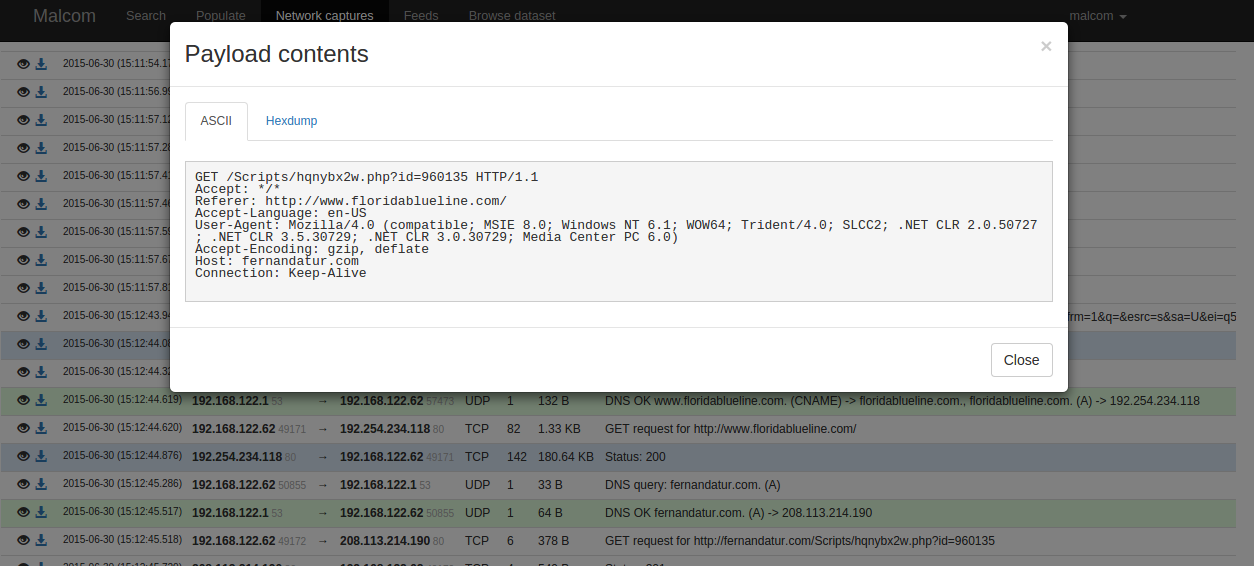
The specific site matches www.floridablueline.com, this site is compromised and contains a malicious URL (http://fernandatur.com/Scripts/ hqnybx2w.php?id=960135) to which the visitor will be automatically redirected in a user transparent way (“Script tag”) and will load an Exploit Kit that, if successful, will compromise the system.
In the next IDS alerts, we firstly see that there is a reference to the webpage that loads the Exploit Kit corresponding to the IP 46.30.45.65 and to the domain good.recycle2learn.com:
“ET CURRENT_EVENTS RIG Landing URI Struct March 20 2015”
(Firma de Emerging Threats)
Later we observe that out victim sends the Flash version it has installed in its IE browser:
“ET POLICY Outdated Windows Flash Version IE”
(Firma de Emerging Threats)
“EXPLOIT-KIT Rig exploit kit outbound communication”
(Firma de Talos (Sourcefire VRT))
and begins to download the corresponding Flash Exploit and a payload:
“ET CURRENT_EVENTS RIG Payload URI Struct March 20 2015”
(Firma de Emerging Threats)
“EXPLOIT-KIT Multiple exploit kit flash file download”
(Firma de Talos (Sourcefire VRT))
Summarizing, the victim user (192.168.122.62) visits a compromised Website (192.254.234.118:80 / www.floridablueline.com), that redirects to a URL (http://fernandatur.com/Scripts/hqnybx2w.php?id=960135) that loads an Exploit Kit (46.30.45.65 / good.recycle2learn.com) and compromises the user’s machine.
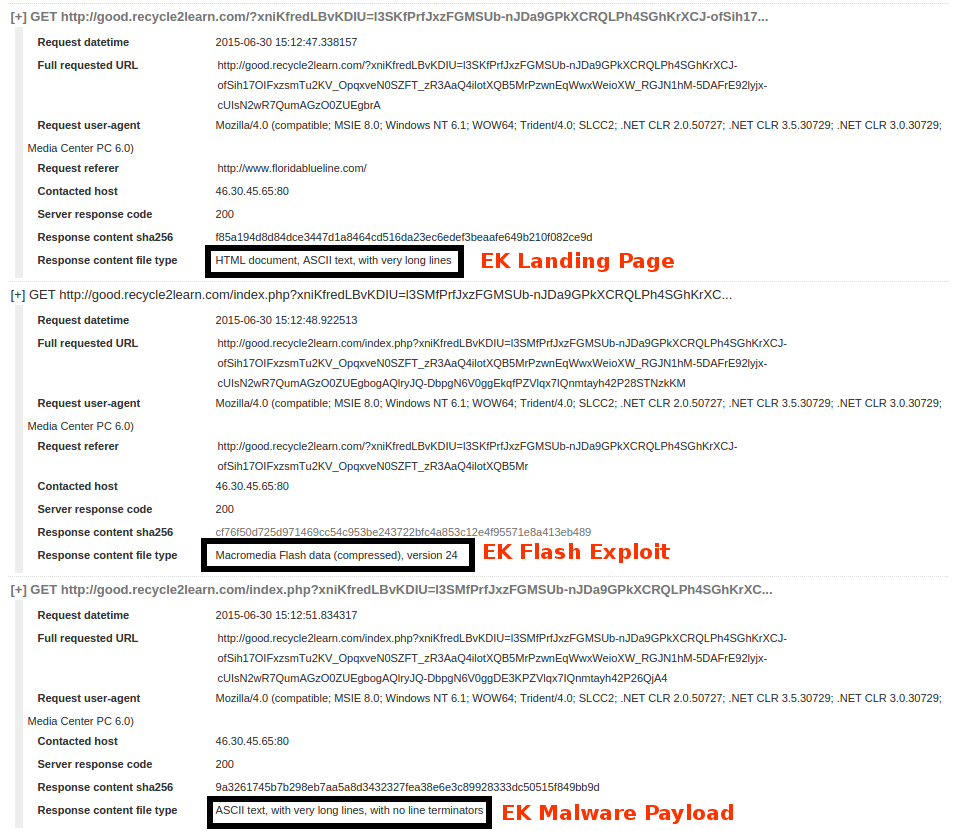
Looking through the http requests we can finally obtain the EK Landing Page, the Exploit and the payload we were talking about.
It is possible to identify the post-infection traffic from our compromised machine filtering in Wireshark by “!(tcp.port eq 80) and tcp.flags eq 0x0002”, traffic that will show us connections to 43.225.38.217 (443/tcp), 111.121.193.242 (443/tcp) and 37.55.107.202 (6998/tcp). Furthermore, filtering by UDP traffic we can find some unusual NetBIOS traffic towards an external IP 78.129.168.237 (137/udp). Again, we can use the IDS signatures (see the Suricata/Emerging threats ones from Virustotal) in order to contrast the information. (For example: ET SCAN NBTStat Query Response to External Destination, Possible Windows Network Enumeration (Attempted Information Leak), ET POLICY NetBIOS nbtstat Type Query Outbound (Unknown Traffic) [2013490]…etc).
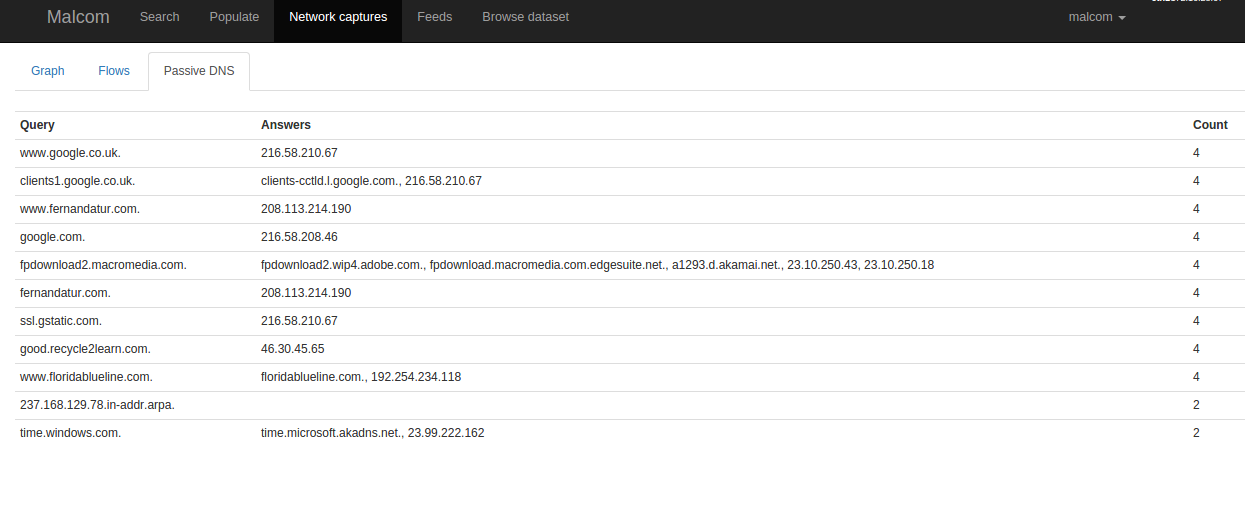
Coming back to Malcom, if we load our Pcap exercise through the “Network Captures” tab, we can see a graphic visualization mode (in the Graph tab), the package flux sequence that has place in the Pcap (in the Flows tab), and a last tab with Passive DNS data.
Graph: We can see a graph-shaped structure for all the established connections. With the Replay option we can even see the sequential animated form of all this connections exactly as we can see in this gif:
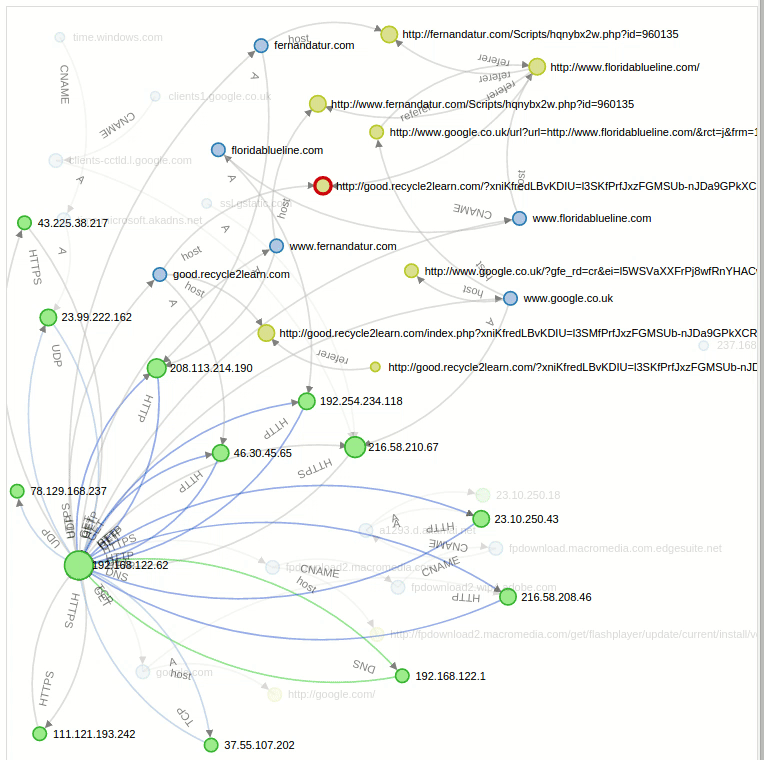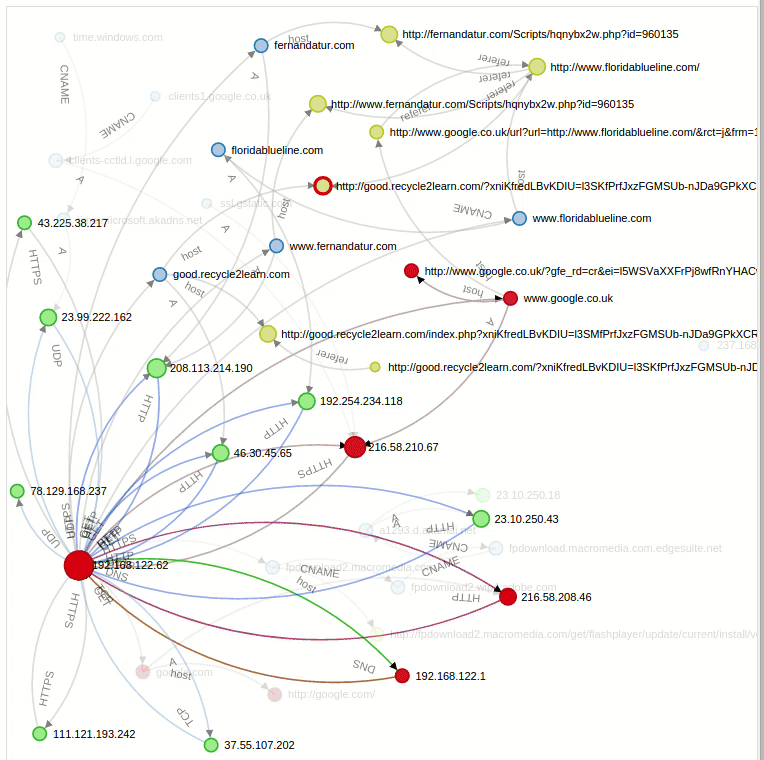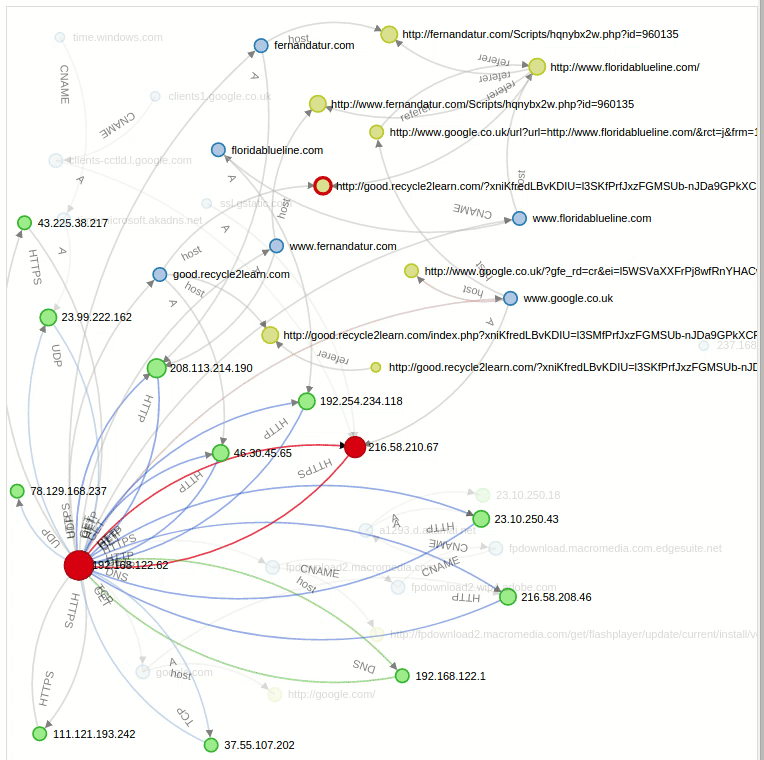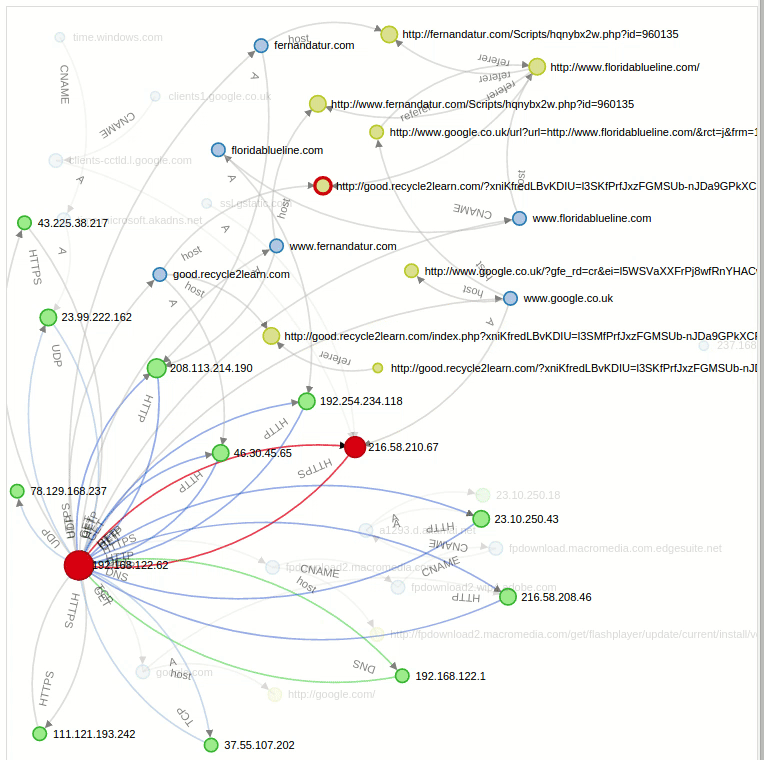
Another interesting side is that we can perform certain operations over this graph, like filtering by a specific domain in a way that it only shows us the direct connections concerning that specific query. If we search for the compromised site “floridablueline.com” we see all the direct connections with it:
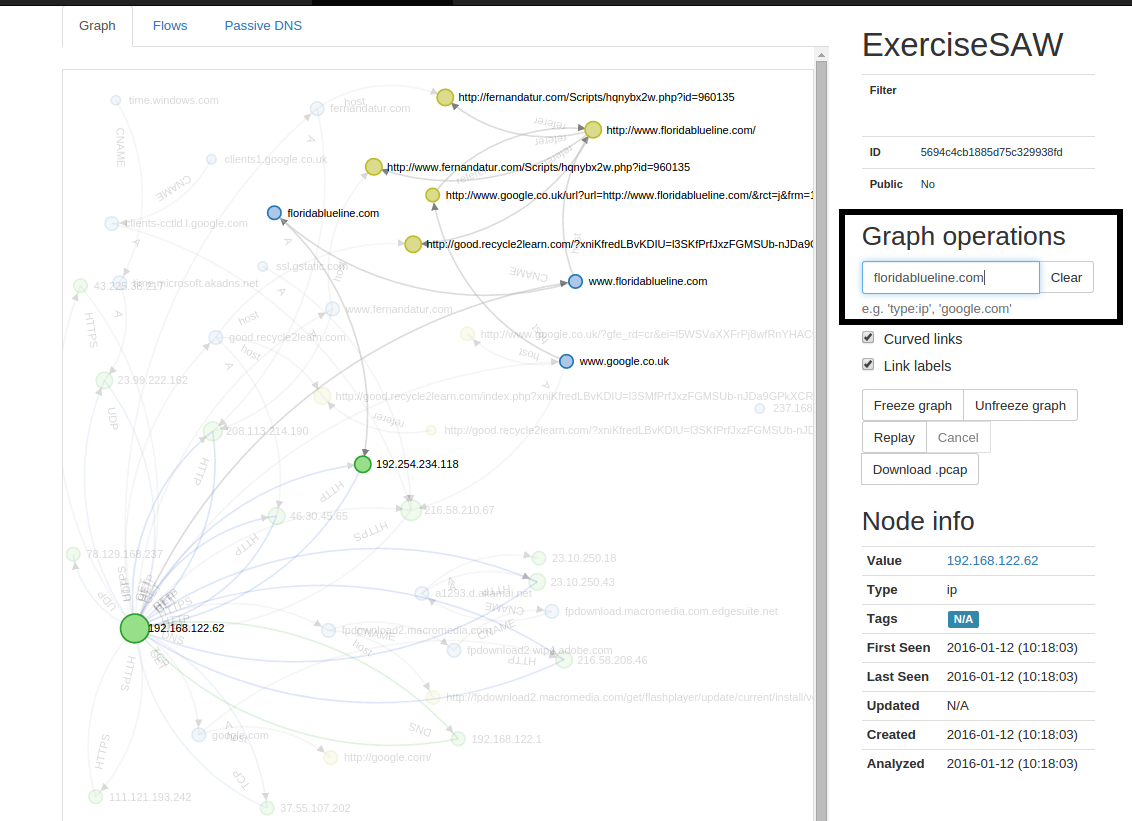
It is possible to find out extra information (see Node info) provided by the tags we have loaded in Malcom via the feeds or we can add them manually as well. For example, if we want to tag the domain that was serving the RIG-EK, we can do it in the “Populate” tab:
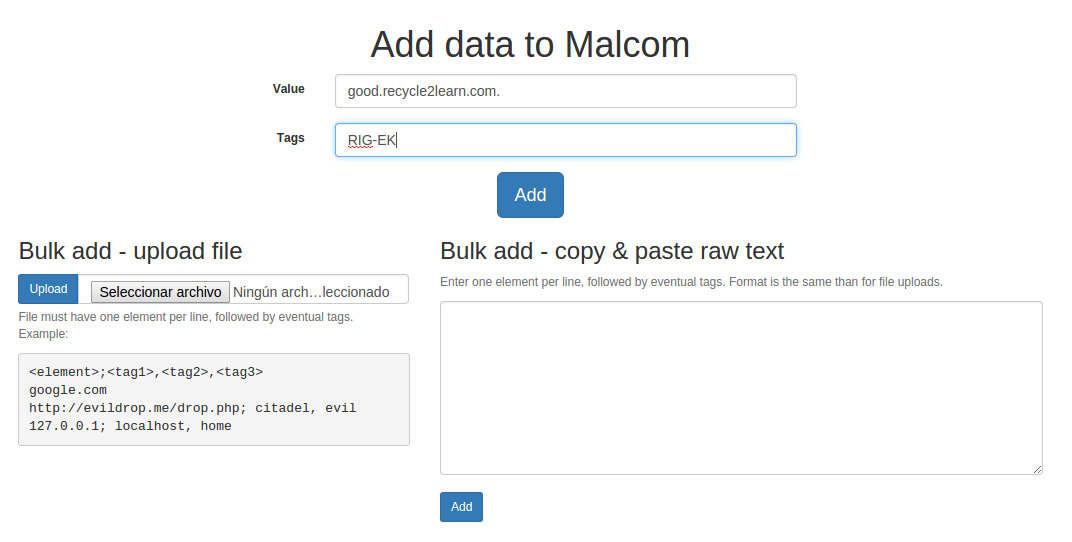
This way, if for example we search in Malcom for the tag “RIG-EK”, we will get together with all the IP/domains tagged as RIG-EK (that come from our public feeds or from our own feeds) also the domain we just introduced.
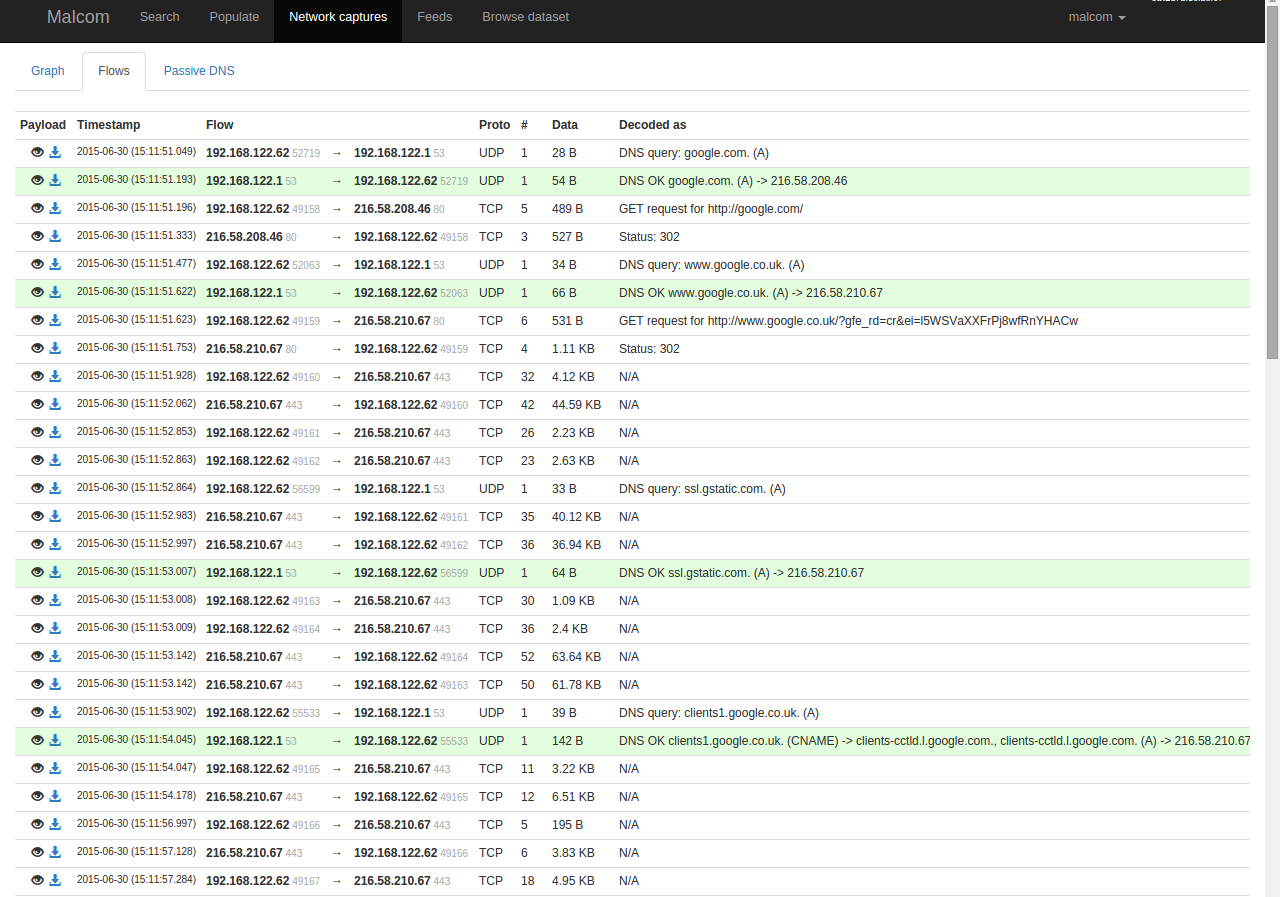
Flows: In this tab we are able to see the package flux in the sequential order they happened in the Pcap and their content.
Passive DNS: it shows up the DNS resolution of the requests that have been done so far.
As you can see, Malcom can be a very useful tool in order to dynamically visualize Pcaps and identify the malicious nodes that, with a good knowledge database and feeds, can help us to expedite our response timing at security incident resolution in addition of being a helpful tool for establishing behavior patterns in malware communication. I encourage you to check all the available documentation and to give the tool a try.
(Translated from Spanish by Víctor Fernández Escorihuela)
