During this month of December we have observed from the malware laboratory of S2 Grupo various threats that we once again wanted to share with you. In this type of entries we will find known threats, seen in other sources or analyzed directly in our laboratory, but the goal of the post is to know what kind of threats have been active throughout this last month.
Here is a diagram with the information collected this month from the lab:
First of all, we would like to highlight the break that Locky has at least given us this month, with a tremendously reduced SPAM compared to the previous two months. This does not mean at all that it has disappeared, rather, many have been arriving at emails with texts of “subject:” such as the following:
“Bills”, “scanned copy”, “Scan”, “for printing”, “Tracking Sheet”, “Subscription Details”, “Attached document”, “Order Receipt”, “Amount Payable”, “Attached document”, “Booking confirmation”, “Parcel Certificate”, “a picture for you”, “Payment Confirmation”, “New(xxx)”, “Invoice number: xxxxx”, “Software License”
With compressed files containing Scripts and Office Documents with extensions: -doc, docm, xls, vbs, js, wsf, jse and downloading the DLL variant of this Ransomware.
Another case that we mentioned last month was the campaign supplanting ONO which tried to infect us with a Trojan known as Sharik. Those responsible for these misdeeds changed the content of the mail two more times in order to try to continue infecting trusted user machines, this time with somewhat generic and less elaborate phishings.
The first, was an email in perfect Spanish with the following content:
Payroll of November 2016 in pdf format is attached.
Save the file to a personal folder.
________________________________________________________________________This message is only for the person to whom it is addressed. It may contain confidential or legally protected information. There is no waiver of confidentiality or professional secrecy for any transmission that is defective or erroneous. If you have received this message in error, we ask that you delete it immediately as well as all your copies and notify the sender. Thank you.
This email attaches a file with the name: 20161130-9087309281001.pdf.exe. If the receiving user has the default configuration, Windows will hide the extension and the name will look like this: 20161130-9087309281001.pdf
In the second case, quite different, they send an email from a foreign girl, who proposes an alternative plan for some day in the short term, and for you to trust her, she attaches a file that takes you to download some videos so that you can get an idea of the plans that she often comes up with to meet interesting people like you.
The case is that she attaches a very simple HTML file that redirects you to the download of a compressed file containing an executable with the name: Phome_videos.exe or Iphone_Video.exe, this time they do not play with the double extension but they do put a rather strange icon, that seems to be that of a video file, and once again, coupled with the fact that the extensions are not seen in most of the machines, can be quite convincing.
In the end, in both cases the result is that the machine ends up infected by this malware that will create a second explorer.exe process running on our machine from which it will gather all the information and credentials that it can send later to the bad server.
Something different from what we have encountered this month was a malware known as TalentBot. It is a sample of quite an elaborate malware, among other things the detail that all the text strings used, which usually provide much information when performing a malware analysis, it stores them encrypted and after decrypting them and using them, it deletes them from memory, so that each one is available in memory for only a few moments.
If the most common infection route is an office document attached to an email, which downloads another malware known as LuminosityLink that acts as an intermediary between the dropper and this malware.
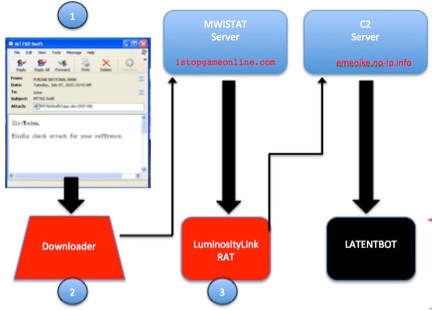
Another very interesting detail is that they have not bothered to develop functions of theft of certain data. Instead, it downloads its own version of Trojan Pony as if it were one of its modules, which is responsible for these tasks.
It is curious how those responsible for this malware, instead of developing their own methods of infection and data theft use other known programs that perform these actions in a very efficient way.
New threats have also appeared such as TeleBot, a malware developed in Python and converted to Windows executable with PyInstaller, uses as a communication protocol and service Command & Control (C2) the Telegram API, in this way, its communication goes encrypted by HTTPS and can be controlled from any device that a Telegram client can install through his or her ID.
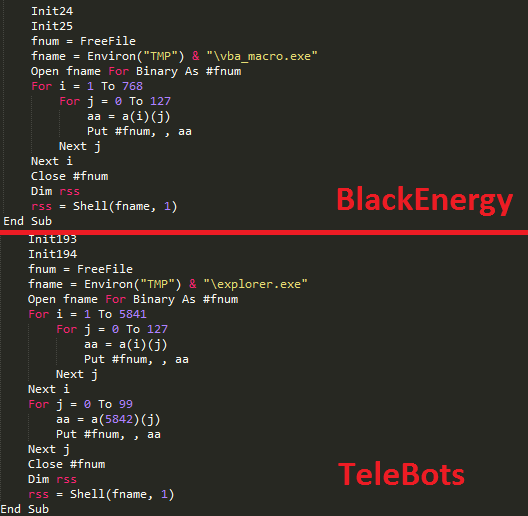
Its infection path does not particularly stand out because once again it is a document with macros, but the interesting detail is that the macro in question that is responsible for downloading and running the Bot closely matches that of the BlackEnergy group.
Finally we would like to review the recent activity of the two ExploitKits(EK) with more activity during the month, which have been RIG-E and its version “Premium” RIG-V, the group behind the infections through RIG- V have been installing the Ransomware Cerber that is already going for Version 5 and does not stop evolving.
Those responsible for the EK RIG-E, have been varying between different Trojans, some of them known as Chthonic and GootKit. This route of infection, although not very directed, is really effective, and the most effective way to avoid falling into it is to have the most updated software possible so that we prevent being affected by the various exploits they use.
