One of the most important things when carrying out a phishing campaign [Obviously, always from legal terms Ed.] is to ensure that our mail gets to evade the anti-spam filters and thus be able to reach the victim’s inbox.
In this post we are not going to explain how Gophish, que ya hemos mencionado en algún post, we will simply explain a series of steps to follow to make our emails more reliable. It is worth adding that following these steps does not ensure 100% success, each mail manager has its own filtering rules.
We start from the basis that Gophish is already installed, so the next step would be to obtain a domain and make a series of changes in DNS administration.
First of all we are going to establish a new SPF registry that is in charge of identifying the mail servers that can send messages on behalf of our domain.
The SPF record would be as follows:
TXT @ v=spf1 a mx ip4:IP ~all
Where:
- v: used version of spf.
- mx: authorize the machines with the IP of the MX records.
- Ip: the ip of the vps where GoPhish is.
- ~all: disavows machines that do not fit explicitly authorized.
Then we add an A record, these records link a domain with the physical IP address of a computer that hosts the services of that domain.
It would be as follows:
A @ IP
To finish, we have the MX record which is the one that defines which is the email server for the domain.
For example, it could be:
MX @ smtp.nuestrodominio.com
Once finished with the records, another important step is to check that when our landing page is accessed, the IP address does not appear, but that of the domain name. And since ‘a picture is worth a thousand words’, here is what it would look like:
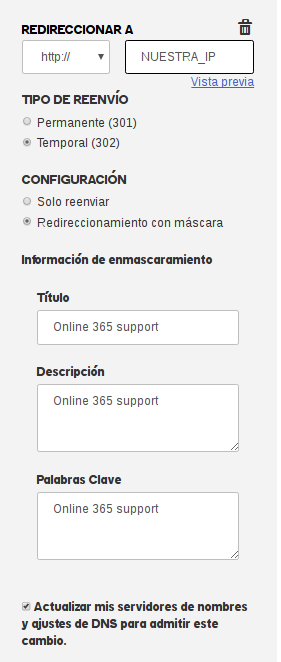
With this we terminate all DNS settings, and our next step will be the configuration and installation of a free software mail server, in this case Postfix.
From our terminal we write:
[RedTeam] > ~: sudo apt-get install postfix
Once installed it will be necessary to make some modifications in the configuration file found in /etc/postfic/main.cf, it will be important to make changes in the parameters:
- myhostname: here we specify the name FQDN (fully qualified domain name).
- mydomain: here we will have to specify the domain name
- mynetworks: here we define which networks or hosts can send mail through our Postfix.
- mydestination: specifies the domains that the team will use to deliver the mail locally, this line can be commented on.
For the changes to take effect we will have to restart the service with:
[RedTeam] > ~: sudo service postfix restart
With all these changes we have made we still need to change something else, this time in Gophish.
When creating a sending profile, we must take into account that the Host field has to be modified (by default it comes as localhost: 25), we will have to modify it by the name that we have put in the MX record.
This small detail is quite important, because if we leave it by default in the mail headers, ‘localhost’ will appear and it will subtract points from our mail.
Now that we have everything modified, how do we check the level of spam in our mail? Well, very easy, there are various on-line tools that allow us to obtain an indicator of this.
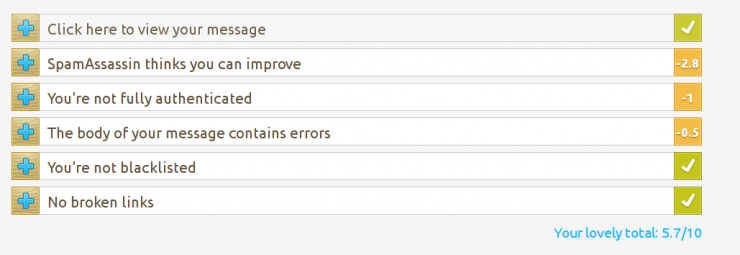
One of the ones I liked the most was https://www.mail-tester.com/ which allows us to analyze up to 3 emails a day for free. We can register an account to get 20 analyses or, if we do not want to give data, use different IP addresses.

And in addition, we can see in detail where we have failed, and in this way we can adjust the settings of postfix, Gophish and our email template in order to improve the score:
We would like to finish by thanking Alberto Sáez and Pablo Arias for the help they have given in collecting all this information to improve the phishing campaigns.
References
https://es.godaddy.com/help/administrar-dn
