The tendency to “be permanently connected” places at our disposal a series of tools with which to “make our lives more comfortable” but this, in turn, exposes us to multiple threats that may negatively affect us as individuals or in our organizations. It is possible to think that this question is too internalized by those who dedicate themselves directly or indirectly to the world of security. However, the reality leads us to discover that the number of anecdotes and news related to security incidents continues to grow and, in many cases, the protagonists are precisely those who dedicate themselves to security.
In today’s post we put the focus on the impact that the information collected and published through the Strava tool has caused.
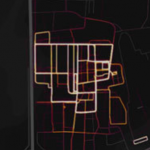 A brief summary for those who have not followed the news: Strava is a tool aimed primarily at athletes that allows you to position and record the journey of a user such as a runner or cyclist. This has allowed knowing the position of bases and secret operations centers of the defense services because the soldiers used this application and the information of their routes was incorporated into a world map available to all users.
A brief summary for those who have not followed the news: Strava is a tool aimed primarily at athletes that allows you to position and record the journey of a user such as a runner or cyclist. This has allowed knowing the position of bases and secret operations centers of the defense services because the soldiers used this application and the information of their routes was incorporated into a world map available to all users.
Analyzing the case with a bit of perspective we can think that a leak of information in Runtastic, Wikiloc, etc. could bring to light very similar information. In fact, five years have passed since we opened the debate on the repercussions of registering all our steps on the Internet (see Tom Thumb and the digital crumbs (I) (II)) and by then a large majority believed it was convenient to reduce and control this habit.
May what happened serve to encourage reflection and take into account the following aspects:
- Personal vs. professional devices: even if a proper separation is made between the personal and professional use of the devices, it is necessary to assess the possibility that the use of our personal device can reveal sensitive information. For example, in regard to the location of secret bases, it has little relevance if the source of information was the corporate device or the users’ personal one.
- Secure configuration: many tools include options to safeguard the privacy of our information. Before using the applications with the default configuration, it is advisable to check and confirm that the security options are properly adjusted. In the case of Strava, establishing a comfortable privacy radius is recommended, with respect to where we live, in order to keep our place of residence anonymous.
- Multiple sources of information: we can think a priori that the data collected through an application such as Strava are not “so sensitive” for a conventional user. However, we must not lose sight of the fact that this information, which can be gathered from other services (social networks, applications to order taxis, food at home, etc.), allows us to generate a very detailed personal profile that we would prefer to safeguard.
- Information leaks: there is no 100% secure system, so even following the best practices there is always the possibility that there might be a leak of information. Given this situation, if we deal with particularly sensitive information, it is better to pay attention to the risks and evaluate the possible consequences and repercussions derived from a potential leakage of information. As we have read in various news, soldiers were urged to use the application to increase their motivation and desire to excel. In this case, the “cons” far outweighed the advantages it brought. In view of what happened, surely those responsible for security would have preferred that the soldiers checked the training series with the classic hand chrono instead of with the tracking tools.
The previously referred recommendations are directed mainly to the user, but of course the organizations are going to have to update their regulations and security protocols to deal with said threats. It would not be surprising that when the time has come it will be familiar to find informative posters reminding us that the use of tools that use geo-positioning is forbidden. 
It is clear that for many organizations restricting the use of these sport applications is not a priority. However, it can be a topic to consider in the short term by those companies that deal with very sensitive information, such as those whose facilities have been designated critical infrastructure.
We hope that this reading has been interesting to you and that if you are users of these types of applications, it will help you to make a more secure use of them.
Regards.
[About Samuel Segarra]
Related links:
- https://www.theregister.co.uk/2018/01/29/strava_military_base_locations/
- http://www.elmundo.es/papel/historias/2018/01/30/5a6f6834e5fdea2b1c8b4617.html – Image 1 extracted from the news.
- https://elpais.com/internacional/2018/01/29/estados_unidos/1517182703_981640.html
- https://www.elconfidencial.com/tecnologia/2018-01-29/rutas-running-zarzuela-strava-fallo-seguridad_1513406/
