Note: This is a fictional story; the characters and situations are not real. The only real thing is the technological part, which is based on a mixture of work done, experiences of other colleagues and research carried out.
These articles are part of a basic incident response workshop. Therefore, there are things that could be done more efficiently and elegantly… but the idea was to do them in a simple way so that they were easy to understand. And like any good practical workshop, you can follow it step by step: you can download a Remnux virtual machine with everything you need for the workshop here (for VMWare) or here (.ova format)).
Incident Response in less than 15 lines
Ultra-fast summary of incident response:
- Preparation: We prepare ourselves for a possible attack by deploying detection and response measures in the Organization.
- Detection and analysis: We detect possible attacks and analyze them to determine whether or not they are false positives, and in the event of an attack we analyze its severity.
- Containment, eradication and recovery: We contain the spread of the attackers through the system, expel them and return the system to normal operation.
- Post-incident lessons: We analyze the incident in search of measures to improve both the security of the system and the response itself for future incidents.
Preparation
In this case study we have an Organization with an intermediate maturity in its security measures: computers have antivirus, a mail gateway with an antispam/antivirus, a proxy that controls navigation, a firewall that controls incoming and outgoing connections and an intrusion detector that can generate alerts against possible attacks.
On the downside, we know that the updates in general (security patches, antivirus signatures and intrusion detector signatures) leave much to be desired, and that users’ security awareness is … disparate, so to speak.
Detection and analysis: “Something is wrong with my computer”
Many of the security incidents begin with a call from a user complaining that “his computer is slow/ doing something weird/ crashing/ is possessed by Alpha Centauri aliens”. And obviously, the user has never “touched anything/done anything weird/ opened anything/ put any USB with raccoon Dutch porn” on his computer.
In most cases after a more or less extensive research (or after the forceful application of a LART), it is shown that the user has taken some action, so that 95% of the cases users are usually a source of inexhaustible false positives (and of some glorious little battle that cannot be told for the sake of the physical integrity of the author).
However, users are a good source of information when detecting an attack against the Organization. Properly trained, not only are they harder to deceive in a spear-phishing attack but they can also warn us about such attacks, allowing us to respond in some cases in real time (that’s why all the efforts in security awareness are always worthwhile).
In this case we have a call from a standard user: his computer is doing “weird things”, and he swears on his life that “he has not done anything”. As he is not a hyperboss but still a boss of a certain rank, a quick response is necessary, so we quickly head to his computer collecting the necessary equipment to respond to a possible incident: USB memory with triage tools, USB disk for a disk capture and a half-liter coffee.
The user receives us for exactly 20 seconds: enough time to leave the computer on and “go to an urgent meeting”. If necessary, he will see us when he returns. At this point, however, all we need is a basic data capture to determine whether or not we have a security incident.
First of all, a dump of the RAM memory of the computer has to be made, in this case with the DumpIt tool, which has an extremely basic operation.
From the USB Toolbox itself we launched the tool:
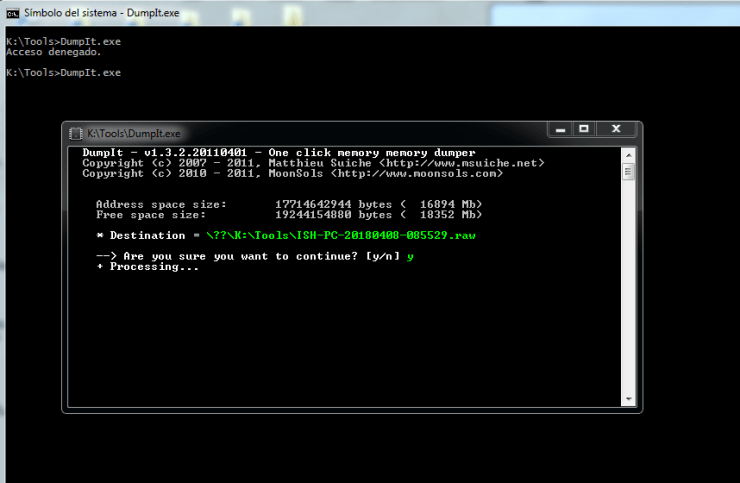
The result is a 2Gb file generated directly on the USB stick itself (remember to alter the hard disk as little as possible in case we have to do a forensic analysis later). While we’re at it, we’re going to collect basic triage information with CYLR (which includes, among other things, the Windows registry, logs and MFT, all at a dizzying speed).
[Note: we want to make this case study VERY practical. Therefore, you can download both the RAM dump and the triage from here].
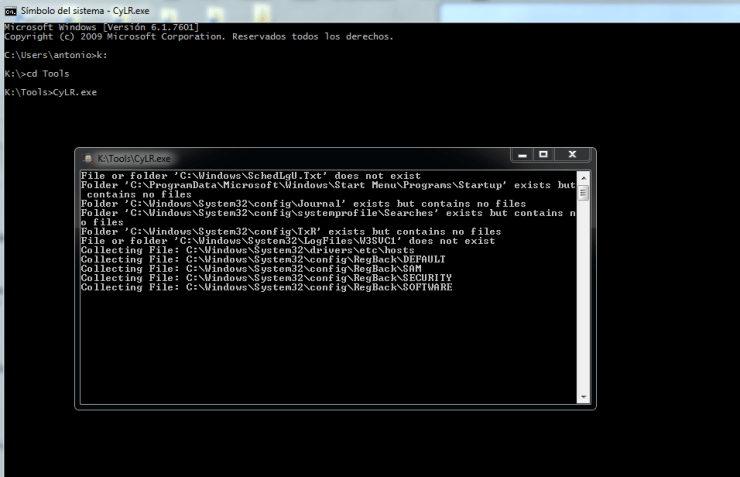
Once the triage information is collected (which should take you <10min on a modern computer), we can go back to our computer to review the data. Memory analysis is usually the technique that offers the best results, so we used Volatility and made two lists of processes with pslist and pstree (tip: in these analyses it is usually necessary to re-check the output of many commands, so it is very useful to redirect the output to a text file):
# volatility --profile Win7SP1x64 -f win7_labodfir.raw pslist > pslist.txt # volatility --profile Win7SP1x64 -f win7_labodfir.raw pstree > pstree.txt Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xfffffa8018da7040 System 4 0 93 590 ------ 0 2018-04-07 08:36:49 UTC+0000 0xfffffa80194ee340 smss.exe 260 4 2 29 ------ 0 2018-04-07 08:36:49 UTC+0000 0xfffffa801a29a060 smss.exe 340 260 0 -------- 0 0 2018-04-07 08:36:52 UTC+0000 2018-04-07 08:36:55 UTC+0000 0xfffffa801a29c2f0 csrss.exe 348 340 9 580 0 0 2018-04-07 08:36:52 UTC+0000 0xfffffa801a5a9900 smss.exe 380 260 0 -------- 1 0 2018-04-07 08:36:55 UTC+0000 2018-04-07 08:36:55 UTC+0000 0xfffffa801a5acb10 wininit.exe 388 340 3 78 0 0 2018-04-07 08:36:55 UTC+0000 0xfffffa801a5b3b10 csrss.exe 400 380 9 325 1 0 2018-04-07 08:36:55 UTC+0000 0xfffffa801a5dcb10 winlogon.exe 436 380 3 112 1 0 2018-04-07 08:36:55 UTC+0000 0xfffffa801a66db10 services.exe 496 388 9 232 0 0 2018-04-07 08:36:56 UTC+0000 0xfffffa801a67eb10 lsass.exe 504 388 7 579 0 0 2018-04-07 08:36:56 UTC+0000 0xfffffa801a684b10 lsm.exe 512 388 10 148 0 0 2018-04-07 08:36:56 UTC+0000 0xfffffa801a532b10 svchost.exe 620 496 11 361 0 0 2018-04-07 08:36:58 UTC+0000 0xfffffa801aa90060 svchost.exe 684 496 9 322 0 0 2018-04-07 08:36:58 UTC+0000 0xfffffa801aac1870 svchost.exe 740 496 23 523 0 0 2018-04-07 08:36:58 UTC+0000 0xfffffa801ab49b10 svchost.exe 832 496 19 450 0 0 2018-04-07 08:36:58 UTC+0000 0xfffffa801ab5f630 svchost.exe 864 496 20 788 0 0 2018-04-07 08:36:59 UTC+0000 0xfffffa801ab8cb10 svchost.exe 912 496 35 1018 0 0 2018-04-07 08:36:59 UTC+0000 0xfffffa801abc1b10 audiodg.exe 996 740 6 136 0 0 2018-04-07 08:36:59 UTC+0000 0xfffffa801ac1ab10 svchost.exe 984 496 15 383 0 0 2018-04-07 08:36:59 UTC+0000 0xfffffa8019c7fb10 spoolsv.exe 1188 496 15 355 0 0 2018-04-07 08:37:00 UTC+0000 0xfffffa8019c88450 taskhost.exe 1196 496 10 282 1 0 2018-04-07 08:37:00 UTC+0000 0xfffffa8019cac600 svchost.exe 1256 496 18 319 0 0 2018-04-07 08:37:00 UTC+0000 0xfffffa801acc6870 svchost.exe 1360 496 10 148 0 0 2018-04-07 08:37:00 UTC+0000 0xfffffa801ad1bb10 Sysmon.exe 1448 496 12 572 0 0 2018-04-07 08:37:00 UTC+0000 0xfffffa8018e61060 vmtoolsd.exe 1524 496 8 295 0 0 2018-04-07 08:37:00 UTC+0000 0xfffffa801a0cf060 unsecapp.exe 1792 620 4 66 0 0 2018-04-07 08:37:02 UTC+0000 0xfffffa801a59a060 WmiPrvSE.exe 1916 620 13 329 0 0 2018-04-07 08:37:03 UTC+0000 0xfffffa801a5de060 dllhost.exe 1932 496 0 -------- 0 0 2018-04-07 08:37:03 UTC+0000 2018-04-07 08:40:14 UTC+0000 0xfffffa801a646060 TPAutoConnSvc. 2000 496 10 141 0 0 2018-04-07 08:37:03 UTC+0000 0xfffffa801a69b060 sppsvc.exe 1312 496 6 153 0 0 2018-04-07 08:37:03 UTC+0000 0xfffffa8018e67600 TPAutoConnect. 648 2000 5 122 1 0 2018-04-07 08:37:06 UTC+0000 0xfffffa8019c33b10 conhost.exe 1080 400 1 34 1 0 2018-04-07 08:37:06 UTC+0000 0xfffffa801a776060 dllhost.exe 2088 496 15 199 0 0 2018-04-07 08:37:09 UTC+0000 0xfffffa801a6e2060 WUDFHost.exe 2232 832 8 192 0 0 2018-04-07 08:37:11 UTC+0000 0xfffffa801a8628f0 msdtc.exe 2296 496 14 154 0 0 2018-04-07 08:37:11 UTC+0000 0xfffffa801ac0d060 VSSVC.exe 2448 496 0 -------- 0 0 2018-04-07 08:37:14 UTC+0000 2018-04-07 08:40:14 UTC+0000 0xfffffa80192ab060 userinit.exe 2504 436 0 -------- 1 0 2018-04-07 08:37:14 UTC+0000 2018-04-07 08:37:45 UTC+0000 0xfffffa8019c52b10 dwm.exe 2512 832 5 126 1 0 2018-04-07 08:37:14 UTC+0000 0xfffffa801a790060 explorer.exe 2536 2504 41 1158 1 0 2018-04-07 08:37:14 UTC+0000 0xfffffa801922e620 vmtoolsd.exe 2616 2536 6 186 1 0 2018-04-07 08:37:17 UTC+0000 0xfffffa801916f720 cmd.exe 2820 2536 1 20 1 0 2018-04-07 08:37:22 UTC+0000 0xfffffa8019182060 conhost.exe 2828 400 2 63 1 0 2018-04-07 08:37:22 UTC+0000 0xfffffa801913cb10 SearchIndexer. 2864 496 13 841 0 0 2018-04-07 08:37:23 UTC+0000 0xfffffa80194d5650 SearchProtocol 2968 2864 0 -------- 0 0 2018-04-07 08:37:26 UTC+0000 2018-04-07 08:41:37 UTC+0000 0xfffffa8019748b10 SearchFilterHo 2992 2864 0 -------- 0 0 2018-04-07 08:37:26 UTC+0000 2018-04-07 08:40:26 UTC+0000 0xfffffa801a5b9360 svchost.exe 1944 496 14 225 0 0 2018-04-07 08:38:21 UTC+0000 0xfffffa801a17bb10 wmpnetwk.exe 1744 496 9 209 0 0 2018-04-07 08:38:22 UTC+0000 0xfffffa8019c45b10 mscorsvw.exe 2476 496 6 87 0 1 2018-04-07 08:39:03 UTC+0000 0xfffffa801a819b10 mscorsvw.exe 2788 496 6 78 0 0 2018-04-07 08:39:03 UTC+0000 0xfffffa801a81a600 svchost.exe 2908 496 13 361 0 0 2018-04-07 08:39:03 UTC+0000 0xfffffa801a745320 TrustedInstall 1980 496 4 120 0 0 2018-04-07 08:39:51 UTC+0000 0xfffffa801a831b10 PING.EXE 1940 2820 0 -------- 1 0 2018-04-07 08:40:01 UTC+0000 2018-04-07 08:40:03 UTC+0000 0xfffffa801a8d7b10 OSPPSVC.EXE 1136 496 6 128 0 0 2018-04-07 08:42:08 UTC+0000 0xfffffa801ab2cb10 python.exe 3020 2536 0 -------- 1 0 2018-04-07 08:42:14 UTC+0000 2018-04-07 08:47:34 UTC+0000 0xfffffa801ab35350 conhost.exe 1760 400 0 -------- 1 0 2018-04-07 08:42:15 UTC+0000 2018-04-07 08:47:34 UTC+0000 0xfffffa801aa38b10 explorer.exe 1132 620 0 -------- 1 0 2018-04-07 08:44:09 UTC+0000 2018-04-07 08:45:10 UTC+0000 0xfffffa801a9c8600 vfggggg.exe 3208 1132 0 -------- 1 0 2018-04-07 08:44:09 UTC+0000 2018-04-07 08:44:38 UTC+0000 0xfffffa801a9c6b10 vfggggg.exe 2072 3208 23 396 1 1 2018-04-07 08:44:25 UTC+0000 0xfffffa801aec0b10 WmiPrvSE.exe 3632 620 13 333 0 1 2018-04-07 08:44:42 UTC+0000 0xfffffa801b55e060 WmiApSrv.exe 3476 496 5 112 0 0 2018-04-07 08:44:50 UTC+0000 0xfffffa801ae88060 WmiPrvSE.exe 3080 620 7 211 0 1 2018-04-07 08:44:55 UTC+0000 0xfffffa801afbc060 SearchProtocol 2952 2864 7 284 0 0 2018-04-07 08:45:39 UTC+0000 0xfffffa801a91f550 SearchFilterHo 2676 2864 5 104 0 0 2018-04-07 08:45:39 UTC+0000
The vfggggg.exe almost damages our vision of how malicious it looks. This time, it seems that the creators of the malware have not invest any effort on obfuscation techniques. It is curious that the parent is explorer.exe (usually it is a cmd.exe or a Powershell.exe, or we can trace the parents to a browser or email client).
The second most profitable option is usually to recognize network connections with netscan:
# volatility --profile Win7SP1x64 -f win7_labodfir.raw netscan > netscan.txt Volatility Foundation Volatility Framework 2.5 Offset(P) Proto Local Address Foreign Address State Pid Owner Created 0x7deda8c0 UDPv4 0.0.0.0:3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e030010 UDPv4 0.0.0.0:64476 *:* 864 svchost.exe 2018-04-07 08:38:26 UTC+0000 0x7e030010 UDPv6 :::64476 *:* 864 svchost.exe 2018-04-07 08:38:26 UTC+0000 0x7e043730 UDPv4 0.0.0.0:5355 *:* 984 svchost.exe 2018-04-07 08:38:20 UTC+0000 0x7e06bb30 UDPv4 0.0.0.0:3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e06bb30 UDPv6 :::3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e089b30 UDPv4 0.0.0.0:5355 *:* 984 svchost.exe 2018-04-07 08:38:20 UTC+0000 0x7e089b30 UDPv6 :::5355 *:* 984 svchost.exe 2018-04-07 08:38:20 UTC+0000 0x7e143010 UDPv4 0.0.0.0:3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e0a93b0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 684 svchost.exe 0x7e0ac680 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 684 svchost.exe 0x7e0ac680 TCPv6 :::135 :::0 LISTENING 684 svchost.exe 0x7e0af5c0 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 388 wininit.exe 0x7e0b6820 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 388 wininit.exe 0x7e0b6820 TCPv6 :::49152 :::0 LISTENING 388 wininit.exe 0x7e144c80 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 740 svchost.exe 0x7e145010 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 740 svchost.exe 0x7e145010 TCPv6 :::49153 :::0 LISTENING 740 svchost.exe 0x7e0afb10 TCPv6 -:0 6800:a91a:80fa:ffff:6800:a91a:80fa:ffff:0 CLOSED 1 ??=???? 0x7e435010 UDPv4 192.168.25.128:138 *:* 4 System 2018-04-07 08:38:19 UTC+0000 0x7e497ec0 UDPv4 192.168.25.128:137 *:* 4 System 2018-04-07 08:38:19 UTC+0000 0x7e5bdec0 UDPv4 0.0.0.0:3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e5bdec0 UDPv6 :::3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e5be010 UDPv4 0.0.0.0:64475 *:* 864 svchost.exe 2018-04-07 08:38:26 UTC+0000 0x7e5c1e00 UDPv4 0.0.0.0:3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e5c1e00 UDPv6 :::3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e74bd40 UDPv4 0.0.0.0:54789 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e752010 UDPv4 0.0.0.0:54790 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e752010 UDPv6 :::54790 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7d4d00 UDPv4 0.0.0.0:3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e7d5340 UDPv4 0.0.0.0:54791 *:* 864 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7d69b0 UDPv4 0.0.0.0:54792 *:* 864 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7d69b0 UDPv6 :::54792 *:* 864 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7d8010 UDPv6 ::1:54794 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7ec330 UDPv6 fe80::fc4b:861d:db18:9601:54793 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7eca00 UDPv4 192.168.25.128:54795 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7edd00 UDPv4 127.0.0.1:54796 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7ee010 UDPv6 fe80::fc4b:861d:db18:9601:1900 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7ee870 UDPv6 ::1:1900 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7f0010 UDPv4 192.168.25.128:1900 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7f0950 UDPv4 127.0.0.1:1900 *:* 1944 svchost.exe 2018-04-07 08:38:22 UTC+0000 0x7e7f5520 UDPv4 0.0.0.0:3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e7f5520 UDPv6 :::3702 *:* 864 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7e44c700 TCPv4 192.168.25.128:139 0.0.0.0:0 LISTENING 4 System 0x7e7e5010 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 496 services.exe 0x7e7e5010 TCPv6 :::49155 :::0 LISTENING 496 services.exe 0x7e8a4010 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 496 services.exe 0x7ead2360 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System 0x7ead2360 TCPv6 :::445 :::0 LISTENING 4 System 0x7ee61630 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 912 svchost.exe 0x7ee63a80 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 912 svchost.exe 0x7ee63a80 TCPv6 :::49154 :::0 LISTENING 912 svchost.exe 0x7f372c40 TCPv4 0.0.0.0:5357 0.0.0.0:0 LISTENING 4 System 0x7f372c40 TCPv6 :::5357 :::0 LISTENING 4 System 0x7ee767a0 TCPv6 -:0 4870:da18:80fa:ffff:4870:da18:80fa:ffff:0 CLOSED 101 3 0x7f566840 TCPv4 192.168.25.128:49219 91.192.100.59:30030 SYN_SENT -1 0x7fb3bec0 UDPv4 0.0.0.0:0 *:* 984 svchost.exe 2018-04-07 08:38:17 UTC+0000 0x7fb3bec0 UDPv6 :::0 *:* 984 svchost.exe 2018-04-07 08:38:17 UTC+0000 0x7fc0a1e0 UDPv4 0.0.0.0:3702 *:* 1944 svchost.exe 2018-04-07 08:39:03 UTC+0000 0x7fc98a50 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 504 lsass.exe 0x7fc98a50 TCPv6 :::49156 :::0 LISTENING 504 lsass.exe 0x7fc9f940 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 504 lsass.exe
We get a rather suspicious IP/port combination: 91.192.100.59:30030. Since port 30030 is not particularly well known, here we might have a lead to continue our investigation.
The third option of interest is to make a list of the open files that are still resident in memory with filescan:
# volatility --profile Win7SP1x64 -f win7_labodfir.raw filescan > filescan.txt
Since we have a suspicious file name, we can search for it:
# fgrep vfggggg.exe filescan.txt 0x000000007e272a90 14 0 R--r-d \Device\HarddiskVolume1\Users\antonio\AppData\Roaming\vfggggg.exe
We verify that the file is located in a user folder, a very common location for newly landed malware on a computer. Let’s extract it from memory with dumpfiles:
# mkdir dump # volatility --profile Win7SP1x64 -f win7_labodfir.raw dumpfiles -Q 0x000000007e272a90 -u -n -D dump
We obtain basic information from the file using file and exiftool:
# file file.None.0xfffffa801ae09e30.vfggggg.exe.img file.None.0xfffffa801ae09e30.vfggggg.exe.img: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows # exiftool file.None.0xfffffa801ae09e30.vfggggg.exe.img ExifTool Version Number : 9.46 File Name : file.None.0xfffffa801ae09e30.vfggggg.exe.img Directory : . File Size : 4.0 kB File Modification Date/Time : 2018:04:07 14:52:57-04:00 File Access Date/Time : 2018:04:07 14:53:34-04:00 File Inode Change Date/Time : 2018:04:07 14:52:57-04:00 File Permissions : rw-r--r-- File Type : Win32 EXE MIME Type : application/octet-stream Machine Type : Intel 386 or later, and compatibles Time Stamp : 2017:06:24 06:53:40-04:00 PE Type : PE32 Linker Version : 8.0 Code Size : 371712 Initialized Data Size : 580096 Uninitialized Data Size : 0 Entry Point : 0xf000a OS Version : 4.0 Image Version : 0.0 Subsystem Version : 4.0 Subsystem : Windows GUI Warning : Error processing PE data dictionary
The file seems to be our culprit (an unrecognized PE32 executable in user space is like a smoking gun next to a corpse), but in this case the size does not match: 4Kb, which indicates that it could not be extracted correctly from the memory.
We continue to explore the available evidence, in this case the MFT (Master File Table) collected by CYLR, which will give us a good clue of the files that were operational at the time of infection. Our goal is to find the way in which the malware reached the system, usually one of these three: mail, browsing or USB.
The MFT is raw extracted thanks to the magic of CYLR, but we need to convert it to a readable format, so we use the mftdump.exe tool to parse it and convert it into a 71Mb file with 175K entries.
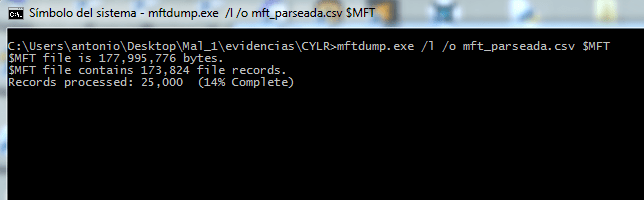
Since we are only interested in today, we can only extract the files modified during the day:
# fgrep 2018-04-07 mft_parseada.csv > mft_malware.csv # wc mft_malware.csv 457 18333 145101 mft_malware.csv
The operation leaves us 457 events, something much more manageable and that we can open without fear in a LibreOffice Calc for its examination. It does not cost much to locate the vfggggg.exe and check the files that are around it:
25645 0 0 0 Purchase Order 03EDG.doc PURCHA~1.DOC 2018-04-07 08:42:00 2018-04-07 08:42:29 2018-04-07 08:42:29 2018-04-07 08:42:29 16508 0 1 0 Content.Word CONTEN~1.WOR 2018-04-07 08:42:07 2018-04-07 08:45:39 2018-04-07 08:45:39 2018-04-07 08:45:39 25612 0 1 0 Content.Outlook CONTEN~1.OUT 2018-04-07 08:42:29 2018-04-07 08:42:29 2018-04-07 08:42:29 2018-04-07 08:42:29 89905 0 0 0 test 02.exe TEST02~1.EXE 2018-04-07 08:43:53 2018-04-07 08:43:53 2018-04-07 08:43:54 2018-04-07 08:43:54 952832 89897 0 0 0 vfggggg.exe 2018-04-07 08:44:02 2018-04-07 08:44:02 2018-04-07 08:43:54 2018-04-07 08:43:54 952832
The file “Purchase Order 03EDG.doc” has every chance of being the vector of infection. We can see that there are residues of the existence of both Word and Outlook, so the infection chain seems quite basic: the user has received an email in Outlook with a malicious attachment and opened it directly with Word.
We have already located the files we want to recover from the user’s hard drive, but before moving on, we will ensure the operation by removing the heavy artillery with the Volatility strings command (which is done in two stages because we have to extract all the useful chains from the memory dump beforehand):
$ strings -a -td win7_labodfir.raw > strings_win7.txt $ strings -a -td -el win7_labodfir.raw >> strings_win7.txt $ volatility --profile Win7SP1x64 -f win7_labodfir.raw strings -s strings_win7.txt > strings_vol.txt
We scan the Netscan IP address and confirm that it is related to our malware:
# fgrep 91.192.100.59 strings_vol.txt 71148752 [FREE MEMORY:-1] "10:45:08,6998260","vfggggg.exe","2072","TCP Reconnect","192.168.25.128:49179 -> 91.192.100.59:30030","SUCCESS","Length: 0, seqnum: 0, connid: 0","0","C:\Users\antonio\AppData\Roaming\vfggggg.exe" 441241253 [FREE MEMORY:-1] "10:45:40,6802302","vfggggg.exe","2072","TCP Reconnect","192.168.25.128:49186 -> 91.192.100.59:30030","SUCCESS","Length: 0, seqnum: 0, connid: 0","0","C:\Users\antonio\AppData\Roaming\vfggggg.exe"
We investigate other traces of TCP connections in memory with “TCP Send”, “TCP Receive” and “TCP Reconnect”:
# egrep "TCP Send|TCP Reveive|TCP Reconnect" strings_vol.txt
We find several links of interest:
1536769087 [2676:00962c3f] 10:42:21,1402019,Network,TCP Send,OUTLOOK.EXE,1128,208.97.132.208:143 438082728 [2676:014baca8] 10:43:53,3557447,Network,TCP Send,powershell.exe,3456,185.83.215.16:443 1161326462 [2952:00299f7e] 10:43:47,6837408,Network,TCP Send,mshta.exe,1236,185.83.215.16:443 519710651 [FREE MEMORY:-1] 10:43:45,8308037,Network,TCP Send,WINWORD.EXE,3744,185.83.215.16:443 519710839 [FREE MEMORY:-1] 10:43:46,3235312,Network,TCP Send,WINWORD.EXE,3744,178.255.83.1:80
Apparently, we do have an Outlook in play, as well as some very suspicious connections of both Word and Powershell. We could go over the content of the strings_vol.txt more, but we already have all the related clues, so we can proceed to recover the suspicious files from the user’s computer: “Purchase Order 03EDG.doc” and “vfggggg.exe”, in addition to the user’s .pst (which stores his mail).
We start the computer with a Linux live CD, mount the disk and locate the files that interest us (for now, it does not seem necessary to make a complete forensic copy of the hard drive). The analysis of malicious files, in the following article…
