After having made a brief introduction and exposition of the Purple Team methodology and listed the phases that constitute it in the first part of this series, in this second part I will go into more detail on how Cyber Threat Intelligence (CTI) integrates in the whole process of adversarial emulation, and therefore, in the Purple Team exercises or programs.
I feel obligated to repeat that (as stated in the first article) many of the content and methodology shown thereafter comes from Scythe and its Purple Team Exercise Framework and closely linked to the entire MITRE doctrine and tools. My goal with this article is to provide a comprehensive view of the topic along with my experience and opinion on some things.
First: understanding the target organization
Whether you are performing CTI as an outside consultant or as part of the organization, it is important to have as much information about the organization as possible.
To do this, the CTI team must conduct an intensive and extensive information gathering exercise, just as an enemy threat agent would. In addition to this, the information must be enriched with that obtained through interviews and inquires with the organization’s personnel.
The goal is to identify the attack surface that conform the people, processes, technologies and systems that are part of the organization’s digital footprint to create a preliminary view of the exposure from the attacker’s perspective, and thus contribute to the discovery of possible attack scenarios to be included in the CTI report.
Threat Modeling (Know thy enemy)
In order to effectively deal with adversarial emulation exercises, it is necessary to know who is targeting our organization. Threats are considered to be those actors who have the intent, opportunity and capability to impact the confidentiality, integrity or availability of the organization.
The following definitions come largely from the SANS Digital Forensics Blog.
- Intent: This is associated with impact as it is the adversary’s willingness to cause an impact. It is closely tied to the industry which the organization belongs to, although different adversaries may have slightly different intentions. For example, most of an insurance company’s adversaries will have the intention to obtain confidential information from its customers, although there might be exceptions. Therefore, the organization cannot change this factor.
- Opportunity: Related to the moment or circumstance in which an actor can cause an impact. For example, an adversary may take advantage of the time gap between the publication of a vulnerability and the mitigation of that vulnerability.
- Capability: Ability of the adversary to achieve its objective and take advantage of the opportunity. It is related to the adversary’s technical capabilities and the resources at its disposal. For example, the ability of an actor to leverage a vulnerability for which there is no published exploit.
Once we have a list of threat actors that meet these characteristics, it will be up to management (chief security officer, CISO or similar), advised by CTI, to decide what priority these threats have in our exercises.
If the organization is inexperienced in these exercises, it is advisable to start with unsophisticated adversaries and increase the sophistication as the SECOPS mature.
Characterize the threat and extract TTPs
Intelligence gathering
Cyber intelligence can be obtained either from open sources or from a vendor, although it can be produced internally. Full in-house produced intelligence (for companies outside of the cybersecurity sector) is only recommended for huge companies where economies of scale can be leveraged.
It is advisable to contrast information from various sources such as ISACs (Information Sharing and Analysis Centers, organizations that are responsible for collecting and distributing cyber intelligence among members of an industry or collective).
A widely used tool for this purpose is MISP (Malware Information Sharing Platform). With MISP, distributed role-based collaboration services can be created so that users with a certain role can upload information to the platform and increase the knowledge base of all members in a normalized and structured way.
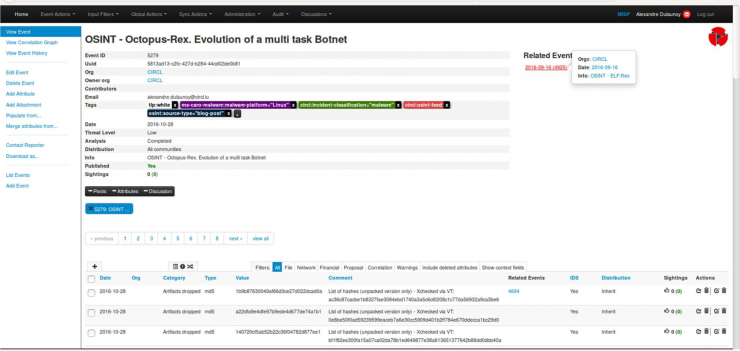
The MITRE ATT&CK platform also deserves an honorable mention. This platform contains an immense volume of intelligence geared towards adversarial emulation of APT groups. Its use will be key in later sections of this article.
Indicators of compromise
Indicators of Compromise or “Indicators of Compromise” (IOCs) refer to a standardized technology that consists of defining the technical characteristics of a threat by means of existing evidence on a compromised computer, i.e., different actions are identified such as files created, registry entries modified, new processes or services, etc. so that they can be used to identify other computers affected by the same threat or prevent them from the same threat.
https://www.incibe-cert.es/blog/indicadores-de-compromiso (translated)
As a way of organizing the Indicators of Compromise of our threat, we will take the Pyramid of Pain, a concept coined in 2013 by David Bianco that is responsible for segregating the information that we can obtain from a threat and prioritizing it from the easiest to obtain but hardest to operationalize information (below) to the most relevant, but at the same time more complicated to obtain (above).
In this way, the IOCs will be presented from bottom to top.
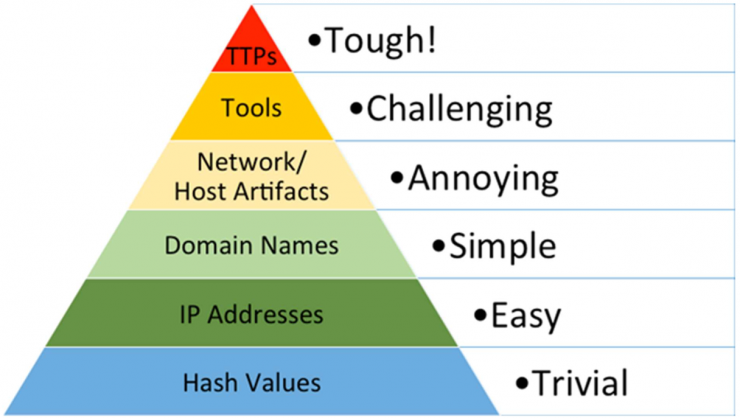
- Hashes: IOCs are useful in the short term but, by definition, if a single bit changes in a file, the hashsum is completely altered. Therefore, it is trivial for an attacker to modify the tools so that hashes are changed every so often or even dynamically (a random string in the source code would suffice).
- IP addresses: This IOC is also very easy to modify. Threat actors often purchase cloud containers to use as a point of attack. This way they can easily replicate the attack from many of these containers. In fact, a common practice is to use these cloud containers as a proxy for their actions so that the real attack machine does not expose its IP and should the container be discovered, carries few damage to their operations.
- Domain names: Although this IOC is more complicated to modify, thousands of different domains are commonly seen using the same techniques as for IP masquerading. Also, threat actors are known for using random domain name generation to create confusion (they only have to register 1 domain but the defenders have to monitor for thousands). In addition, it is also common practice to use dynamic domain name providers such as duckdns or dyndns.
- Host or network artifacts: These are traces left by the attacker in his attack, such as files dropped on the system, commands executed, network packets formed in certain ways, etc. These IOCs are more difficult to modify, although the same actor can have small variations that modify them slightly, such as randomizing file names and paths, obfuscating network traffic or changing HTTP request User Agents, to name a few.
- Tools: This mainly refers to those non-native tools used to get the system compromised both on the attacker’s PC side and on the victim’s side. It is a major challenge for an attacker to modify these tools, so this IOC guarantees better detections. Therefore, attackers try to camouflage the tools as much as possible with the native tools that the organization uses in production (e.g. using powershell commands for enumeration or using WMI as a C2).
- TTPs: Those deserve a whole section…
TTPs (Tactics, Techniques and Procedures)
This is the most difficult intelligence to obtain and at the same time provides the most relevant information for the Blue Team to develop a more effective detection, attribution and response plan.
It is very difficult for a threat actor to modify their TTP because it is a high-level description of their actions, and to modify it they would have to completely change the way they attack.
At the same time, it is complex for the Blue Team to implement defensive measures to detect TTPs, as the use of individual detection sources is not enough; correlation rules and aggregation of alerts from different sources are essential.
At this stage, the CTI team must use the intelligence obtained to build a map of the adversary’s TTPs.
As we mentioned a few lines ago, this will usually be done using what has become the industry standard, the aforementioned MITRE ATT&CK Framework. MITRE has been in charge of creating a common framework to organize actions, procedures or tools according to a division that allows to have a more organized vision of a threat.
It is important to define the different components into which TTPs are divided for MITRE:
- Tactics: Represented as columns of the Matrix, they are the description of the objectives of a high-level action. For example, the Persistence tactic includes those actions that the attacker uses to maintain access to an already compromised system despite resets, password changes and other actions that may jeopardize his access to the victim.
- Techniques: Represented as boxes below the columns, these are more exhaustive descriptions of offensive actions, but without going into particular details regarding the Operating System or type of tool. A technique always belong to a Tactic. For example, the T1053 Scheduled Task/Job Technique consists of creating a scheduled task that recurrently executes malicious code. If this malicious code were a C2 channel, it could be included in the Persistence tactic exemplified above.
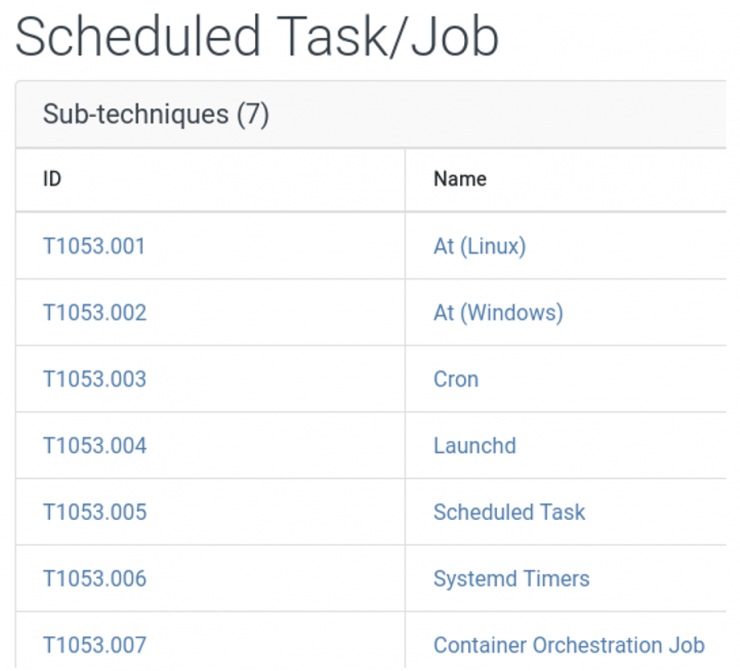
- Sub-techniques: These are represented as drop-down menus within each tactic and give a technical description of different variants of the technique. To continue with the previous example, the sub-techniques of the Scheduled Task/Job technique would be different variants of this action depending on the victim operating system or the type of scheduled task to be used (see image).
- Procedures: These are not listed in the matrix because they are too numerous. They are the specific steps, commands, tools and their use for a particular case. In our case, it could be an example of a procedure to use Powershell to create the scheduled task as you can see in this article.
Analyze and Organize
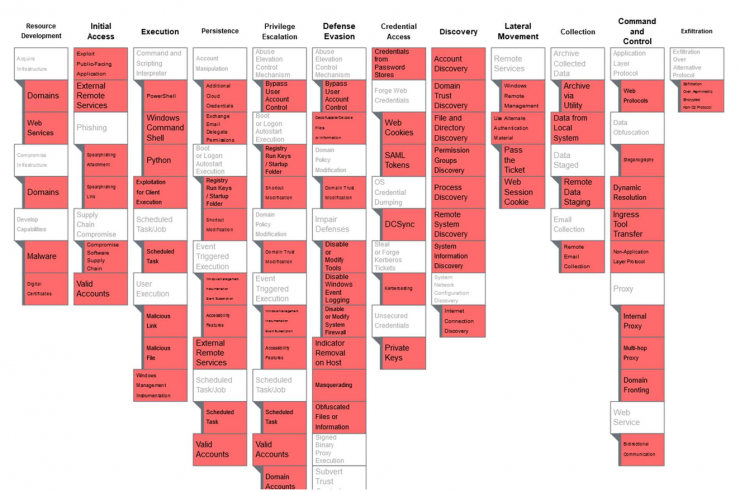
Creating an adversarial profile is a very good way to establish a high-level plan for Red Team tasks during exercise execution. MITRE has developed the ATT&CK Navigator tool, an open source web application in which the TTPs of a threat can be graphically represented. MITRE also has a collection of threat groups and software with their associated TTPs that can be mapped into the MITRE ATT&CK Navigator.
An example showing the TTPs related to the APT29 group in ATT&CK Navigator can be seen below.
Tabletop exercise
Exercise sponsors and technical managers should review the TTPs offered by the CTI team and do a tabletop exercise to choose which of those TTPs will be emulated during the Purple Team exercise.
The TTPs chosen should be currenty in use by the threat actors. In the case of continuous Purple Team operations, new TTPs will be added at each iteration as intelligence is updated.
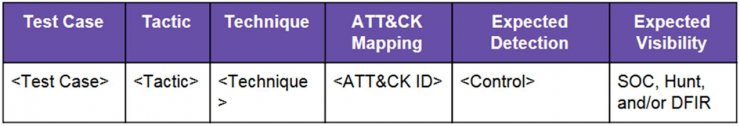
Here all TTPs to emulate will be listed (the TTPs to be emulated are often referred to as Test Cases in the adversarial emulation domain) and it must be assessed which controls and teams will have visibility of it, as well as if detection, blocking or logging is expected.
A matrix similar to the following should be designed to show the expected results and serve as a base line for the execution plan as well as to evaluate the success of the exercise in the Lessons Learned phase.
To be continued…
For the execution of exercises of a certain size, it is necessary to have a tool that provides a platform for exercise management and follow-up.
To be consistent with the topic we are dealing with, the tool we choose has to have the ability to integrate both the coordination of Red and Blue team activities to include at the same time the emulation actions and their respective detection measures.
For this purpose, in the next chapter of the series (III), the free tool Vectr.io will be used. With it, we will see how to coordinate all the elements of the exercise and, in addition, to have a knowledge base for the future in order to study the evolution of the organization’s security posture, but that is another story…
