Threat detection is largely based on indicators of compromise. These indicators are observables that we identify during the management of an incident or during an investigation, that we receive from third parties in the form of intelligence feeds, that we download from platforms such as MISP, that we share among working groups… in short, we discover them or they discover them. But where do these indicators come from? In one way or another, indicators, a fundamental part of the characterisation of a threat (actor, operation…), come from intelligence analysis. In this article, we will discuss the path from intelligence gathering to the generation of indicators of compromise to detect a threat. This path is summarised in the figure below:
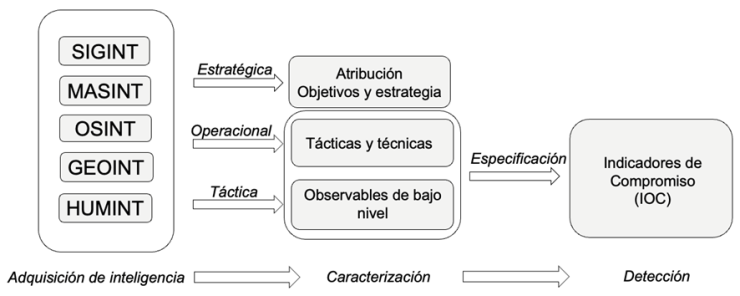
We all know that the various intelligence disciplines play a fundamental role in detecting threats in cyberspace. In this cyber domain, each of these disciplines (simplified SIGINT, MASINT, HUMINT, OSINT and GEOINT) has a specific weight and value, and forms the basis of what we call cyber intelligence. For example, the role of signals intelligence tends to be much more important than that of geospatial intelligence, and human sources contribute much less intelligence than signals, but much more value if well managed.
All collection disciplines can produce intelligence at three levels. At the highest, strategic level, we find intelligence related to aspects such as the attribution of a hostile operation, an actor’s objectives or the strategy defined to achieve them. Although obviously very relevant to the characterisation of a threat, this information is not directly observable and is therefore difficult to translate into actionable intelligence.
Below strategic intelligence is operational intelligence, where we identify the tactics and techniques of hostile actors, and finally, at the lowest level, tactical intelligence, which allows us to identify low-level observables associated with a threat: IP addresses, hashes… almost everything we would normally find in an MISP. The intelligence generated at both levels can then be transformed into actionable intelligence, intelligence that allows agile and efficient decision making (we will not go into the quality of intelligence at either level, which is a very long discussion for another post).
From this actionable intelligence, both from tactics and techniques (operational intelligence) and from low-level observations (tactical intelligence), we specify indicators of engagement that allow us to detect threats. These indicators can be either behavioural (those specifying tactics and techniques) or low-level (atomic or computational). Clearly, behavioural indicators add much more value to detection than low-level indicators. They have a longer lifetime and are more difficult for the adversary to modify, so the detection capability they provide is much more valuable.
Using indicators of compromise in our security infrastructure and sharing them with third parties enables agile threat detection. Although ideally we should be working with behavioural indicators, in practice most of the IOCs we find in sharing platforms such as MISP are low-level indicators, mainly IP, domains, mutexes…
Let’s take an example that goes all the way. The analysis of a malicious code gives us the hash of the executable and a command and control IP address to which it connects to receive commands. In this case, we generate tactical intelligence from technical source intelligence (MASINT in our classification), which we specify in a straightforward way in the form of indicators of compromise. We can use both low-level indicators in our security systems, for example, both the hash and the IP in our XDR and also the IP in the perimeter security systems. With these flags in place, we can already detect the presence of this malicious code in our organisation (and even block its activity). However, if the same code changes its hash or uses a different IP for command and control – trivial changes to the hostile actor – we will not be able to detect it. In addition, technical intelligence analysis can generate operational intelligence and provide us with a behavioural indicator: for example, a sequence of HTTPS command and control requests at a certain interval or with a certain pattern, regardless of the destination to which the traffic is being sent. If we are able to specify this behaviour, for example in our SIEM, we will be able to detect the activity of the malicious code even if its command-and-control IP or hash changes. This way, if the hostile actor wants to remain undetected, we force them to further modify their code to behave differently, which is obviously more expensive than changing an IP or hash.
Indicators of compromise can be loaded into an organisation’s security appliances and provide immediate results. We talked about the types of indicators and their usefulness in a post on Security Art Work three years ago. More importantly, we talked about the problem of working mainly with low-level indicators and not with behavioural indicators. Simply put, as long as we continue to work with these low-level indicators (again, almost anything we can find in a MISP: hashes, IP, domain names…), advanced threat detection is complex; it always is, but if we are not able to specify and share operational intelligence, it will be even more difficult.
