The world of cybersecurity is becoming increasingly complex and challenging. With each new threat, from harmful capabilities such as malware or 0 days, to changes in infrastructure, having moved from on-premise to hybrid or full-cloud environments, there is an urgent need for schemes and methodologies to help address these adversities. We not only seek to minimize the impact of any threat, but also to achieve a level of detection and neutralization with which we feel confident, although this can often give a false sense of security.
Today we find various schemes that help us understand and contextualize the modus operandi of hostile actors. From the widely recognized MITRE to the Malware Behavior Catalogue (MBC), through Microsoft Attack Kill Chain and Lockheed Cyber Kill Chain, these tools offer us a guide to understand and confront the tactics, techniques and procedures (TTPs) used by adversaries. Within this scenario MITRE ATT&CK is the most recognized scheme. Its matrix breaks down the different techniques, tactics and procedures (TTPs) used by hostile actors.
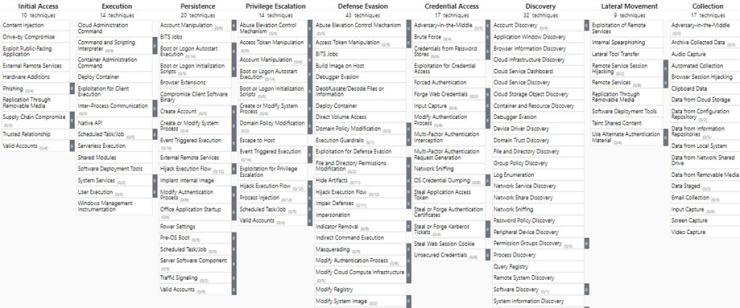
In the case of tactics, the phases that an attacker can follow to execute an offensive operation against any organization are presented. This, in addition to serving as a starting point for security analysts, makes it possible to understand and neutralize the impact as quickly as possible. However, we are currently observing how multiple security tool or service providers are using this matrix as a competition, where the one that covers the most boxes in the matrix, takes the “grand prize” or is “the best”.
This approach has led to a situation where, as experts warn, the use of ATT&CK is getting out of control. For example, a vendor may claim to cover 100% of the T1055 – Process Injection technique. This suggests that their detection capabilities not only cover basic techniques, such as the use of WinAPIs to inject code like VirtualAlloc, VirtualProtect or CreateThread, but go further, covering more customized mechanisms that avoid the use of WinAPIs, such as the use of pointers to functions that execute shellcode (((VOID()()()) pBadJuJu)(); ), or the use of undocumented APIs or other of the many variants of process injection. The same happens with the rest of techniques, such as T1027 – obfuscating file or information, since there are hundreds of mechanisms and tools that can be found with a simple google or github search.
However, there are some other techniques that either do not even appear in the matrix, or the procedure is not clearly addressed, as is the case, for example, of the Ghostly Hollowing, API Unhooking, Halo’s gate or Bypassing AzureAD and CA techniques. These techniques show that, although the providers indicate that they cover 100% of ATT&CK, it is not enough to guarantee the security of the organizations, thus creating a false sense of security. Think about the challenges that malware analysts and Threat Hunters have to face. Adversaries use incredible ways to evade defenses, or exfiltrate information, so even if ATT&CK has documented X technique, it is often almost impossible for a detection engineer to develop sufficient mechanisms to identify malicious activity. For example, some real cases we have seen is when GHOST BLIZZARD exfiltrates information via IMAP to a mail service of a UAE front company or to a mailbox of some Ukrainian ministry when its victim is Ukrainian. In the end, these are complex and specific scenarios that security schemes are not able to cover, so it is necessary to provide teams with more capabilities based on other knowledge bases.
Imagine for a moment that a vendor claims to cover 100% of a cybersecurity technique. Would that mean that their detection and neutralization capabilities are impeccable, leaving us, as security analysts, out of a job?…. The reality is that we are faced with hundreds of alerts with an alarming percentage of false positives and security teams overwhelmed by the avalanche of alerts without context and lacking the visibility to understand them.
With all this information, it is important to highlight the value of schemes like ATT&CK, which do an exceptional job of gathering information on the tactics, techniques and procedures of hostile actors. This information is invaluable for modeling threats, understanding the campaign objectives of cyber attackers, clustering similar activities, and developing detection and neutralization strategies by understanding the objectives of TTPs, but at the end of the day it is a repository of information that is part of the resources needed to address threats.
So, yes, as cybersecurity experts, we strongly encourage and recommend the use of these schemes, but always with the caution of maintaining a balanced perspective. It is crucial to remember that these schemes are tools to guide the analyst, not the holy grail of cybersecurity.
