When it comes to an attack on an internal network, we all think that the output of the data could be through that same network. For example, if a potential attacker were to infect a device with the intention of stealing information, he would require an exit through the network itself to send the information to an external server.
The question we could ask ourselves is: is there a second way in which the stolen information could be sent? To which the answer is yes, but with nuances. Let us consider the following scenario: an attacker manages to connect a device that communicates by radio frequency to a computer in the internal network. What could this involve?
There is a Spanish prototype, the RPK2, which answers this question. This USB is passed off as a printer to the computer it is connected to. Subsequently, it will start communicating with a receiver that will be manipulated by the attacker. Since the receiver device communicates by radio frequency, it should be located a few meters away from the malicious USB, in order to maintain continuous communication.
By sending commands to RPK2, the attacker can request it to steal different types of data such as, for example, the operating system version, users logged on to the computer or even try to steal credentials stored in the clear.
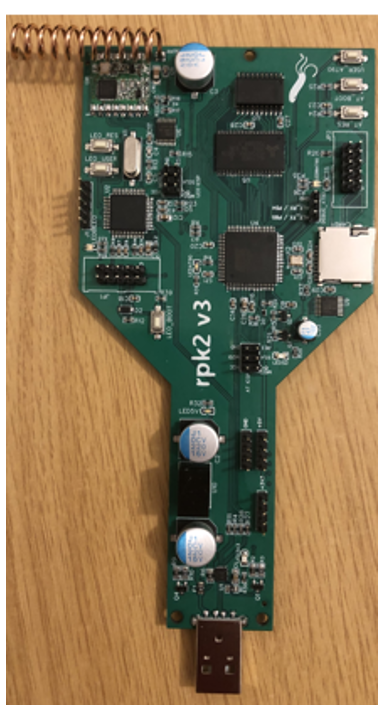
A possible improvement to this attack would be to insert a SIM card into the device that receives information from the USB. This time, the attacker would connect the USB to any available computer and then hide somewhere nearby the receiver connected to a battery and with a SIM card.
This variant would allow the attacker to carry out the attack over the Internet by connecting to the receiving device via the Internet. Therefore, the attack could be carried out from any place with internet access, without the need to be close to both devices.
As a second entry vector to an internal network using radio frequency, we could rely on LoRa technology. This acronym stands for long range. This open source technology together with LoRaWAN is designed to wirelessly connect battery-powered devices to the Internet.
Let’s say an attacker creates a device that, via LoRa, connects a Command and Control to the company’s internal network. A possible device using such technology, connected to a RaspberryPi, could connect to both Wi-Fi and the network via Ethernet.
This attack, like the previous one, requires the attacker to be close to the LoRa device, although it could use amplifiers to replicate the signal and perform the attack at a greater distance.
Unlike RPK2, it would not only be possible to steal information from a single computer. The scalability of this attack is greater, since it has access to the network. In addition, connections to the attacker’s infrastructure are not made from the attacker’s own infrastructure, but via LoRa technology.
In conclusion, although radio frequency is a technology that could be used as a vector for attacking an infrastructure, it is not very likely to be used by an attacker, nor is it very agile. It is a vector that can provide entry vectors to infrastructures that may be properly protected but, as we have seen, the attacker will need to be close to the devices and the delay time in sending and receiving the information will be longer than over the Internet. As a possible additional protection, there should be strong physical security, so as to be able to know if an attacker tries to enter one of these devices to connect it and carry out the attack.
