In recent years we have witnessed the release of a large number of C2s in different languages: Covenant in .NET, Merlin and Sliver in Go or Mythic in Python are some examples. All of them are added to the more classic tools established in previous years (Cobalt, Empire, …) creating a large ecosystem where sometimes it is difficult to choose between them all.
In September 2022, Havoc, a C2 written in multiple languages (C++, Golang, C and ASM) was published on github and has since achieved great notoriety in the world of offensive cybersecurity thanks to its modularity and efficiency, and has become one of the go-to free C2s.
In this post we will take a look at its installation process, as well as its operation and capabilities.
Installation
The installation of Havoc is simple and can be found in the documentation of the tool, the first thing we are going to do is to clone the repository:
We install the necessary dependencies:
To configure the teamserver we have to install a couple of dependencies for Go:
We mount the server (this step may take some time):
Once this is done we can run the server by loading a basic profile:
Finally, we are going to mount the client in the same way as we have done with the server (this will also take some time):
Now we can launch the client and connect to the teamserver:
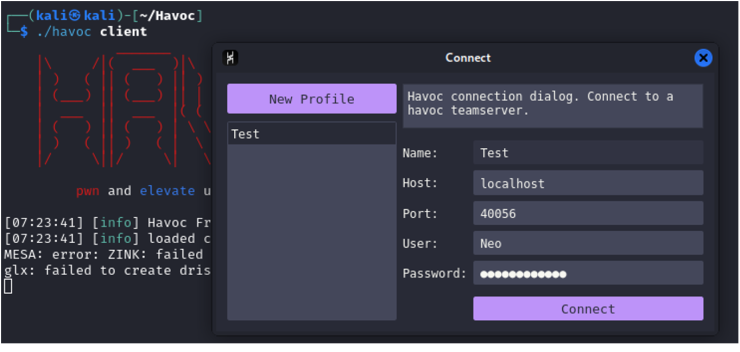
By default we have two users (Neo and 5pider), we can add more or modify them by updating the profile we have uploaded.
Listeners
Now that we are connected to our C2 we can create a listener to which all the information will arrive and with which our payload will communicate later.

The listener options are simple, with the possibility of creating it in different modes: Https, Http, SMB or using another external C2 as communication.

Agents
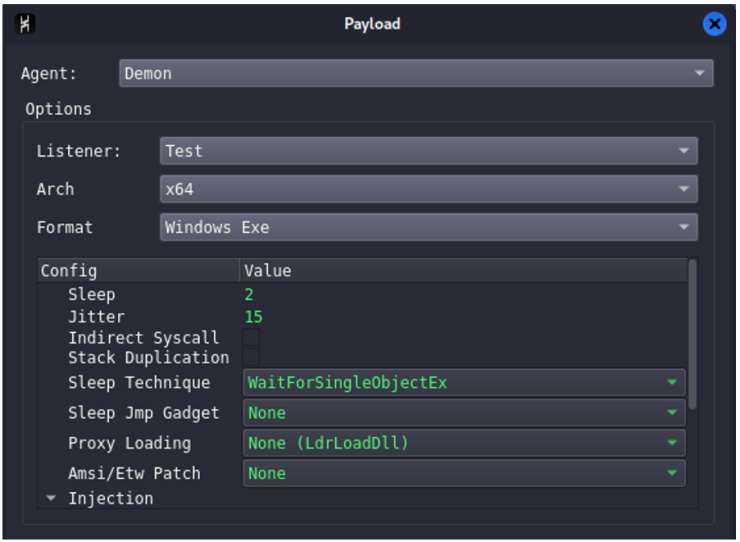
When creating payloads we find a great amount of options to adjust the agent to what we are looking for and to our way of working.
The first three options are used to choose the listener with which it will communicate, the architecture for which we are preparing the payload and its format (choose between .exe, .dll, shellcode or server .dll).
It is also possible to configure the time between requests (Sleep and Jitter) as well as to use indirect system calls or stack duplication to avoid detection; in turn we have different techniques to carry out the timeouts and to encrypt these techniques.
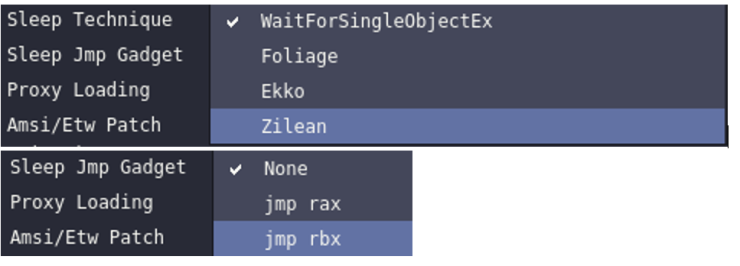
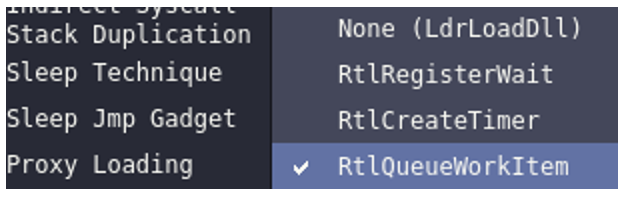
On the other hand, we have Proxy Loading, which will also help us to achieve a higher evasion rate in our payload.
Lastly, there are all the injection options:
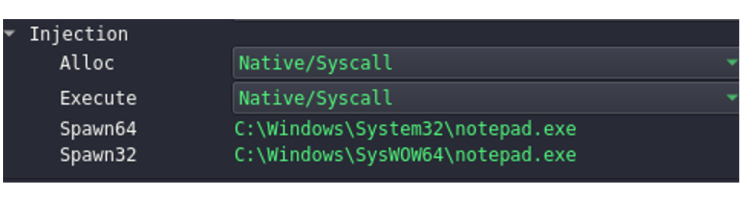
Within Alloc and Execute we can choose between Native/Syscall or Win32, so that it uses the method that we consider convenient. If we select the first option, the payload will use NtAllocateVirtualMemory and NtCreateThreadEx, on the other hand, if we choose Win32 it will use VirtualAllocEx and CreateRemoteThread.
In the two Spawns we will choose the injection target.
As we can see, Havoc agents are highly customizable and this is where this C2 stands out, which, as we mentioned at the beginning, has grown in popularity due to this modularity.
It is important to note that the default payloads, despite the different options available, do not have a high degree of antivirus and EDR evasion. However, thanks to the customization mentioned above, it is possible to use them in conjunction with more advanced techniques, thus achieving a much lower detection rate.
The agent has typical commands of a C2, as well as other interesting and more particular, some examples of what kind of actions we can do with our agent can be: “shell/powershell” to execute commands in cmd or powershell, “download/upload” if we want to download or upload files, “screenshot” takes a screenshot, “shellcode” and “dll” allow the use of injection techniques, on the other hand, we can play with tokens with the command “token”.
Finally, we have the “config” command that among other things can be useful to define in which hours our agent will be working using “config workinghours”, as well as a date where this agent will stop working with “config killdate”.
Extentions
In addition to all the above Havoc also has integrated a section with some extensions made by the community and ready for installation.
Some of them are very interesting. With “havoc-privkit” we can integrate “privkit”, a privilege escalation vulnerability detection tool, into our C2. On the other hand, extensions like “havoc-bloodhound” help us save time by facilitating the process of adding the necessary files to Bloodhound.
Other
To finish this tour of the tool it is worth mentioning other features such as a chat window where different C2 users can communicate with each other.
We also have a Loot tab where some of the data that we extract with our payload (screenshots, downloads, …) will be collected.
Conclusions
As we can see, Havoc is a versatile and customizable tool, easy to install and use, that has many options and makes use of current techniques.
It also stands out visually compared to other established tools on the market, such as Cobalt Strike.
Although it no longer has such a low detection level as some time ago, it is possible to configure it as much as we want (or know how), being able to reach considerably high evasion rates.
