Siguiendo con la entrada de ayer Intro al escáner de web Nikto (I) vamos a seguir con la introducción al escáner web de Nikto.
Usando Nikto
Como ejemplo voy a usar Nikto contra un servidor Web que tengo algo desactualizado, recalcando los datos más significativos:
perl nikto.pl -h mipaginaweb.com-Cgidirs -evasion -mutate 1 -mutate 2 -mutate 4
-mutate 5 -T 012345789abcx6 –p 443,80 -Format html -output resultado_nikto1
Al abrir el reporte http generado:
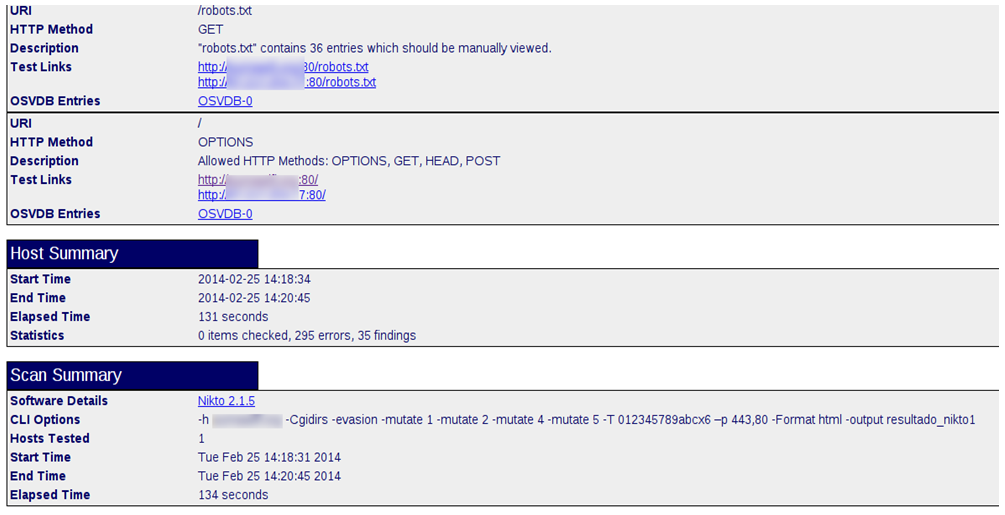
Se puede hacer un escaneo básico:
perl nikto.pl -h mipaginaweb.com –C all
+ Target IP: 8.8.8.8
+ Target Hostname: mipaginaweb.com
+ Target Port: 80
+ Start Time: 2014-02-25 14:44:11 (GMT1)
---------------------------------------------------------------------------
+ Server: lighttpd/1.4.28
+ Cookie SESSc3f36558a0edeba99bfd5493511360b6 created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.3.3-7+squeeze18
+ The anti-clickjacking X-Frame-Options header is not present.
+ OSVDB-3268: /scripts/: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /robots.txt, fields:
0x3050063894
+ OSVDB-3268: /includes/: Directory indexing found.
+ File/dir '/includes/' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ OSVDB-3268: /misc/: Directory indexing found.
+ File/dir '/misc/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ OSVDB-3268: /modules/: Directory indexing found.
+ File/dir '/modules/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ OSVDB-3268: /profiles/: Directory indexing found.
+ File/dir '/profiles/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ File/dir '/scripts/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ OSVDB-3268: /sites/: Directory indexing found.
+ File/dir '/sites/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ OSVDB-3268: /themes/: Directory indexing found.
+ File/dir '/themes/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ File/dir '/cron.php' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ File/dir '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or
redirect HTTP code (200)
+ File/dir '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/install.php' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/update.php' in robots.txt returned a non-forbidden or redirect
HTTP code (302)
+ File/dir '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect
HTTP code (200)
+ File/dir '/?q=admin/' in robots.txt returned a non-forbidden or redirect HTTP
code (302)
+ File/dir '/?q=node/add/' in robots.txt returned a non-forbidden or redirect HTTP
code (302)
+ File/dir '/?q=search/' in robots.txt returned a non-forbidden or redirect HTTP
code (200)
+ File/dir '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP
code (302)
+ File/dir '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP
code (302)
+ File/dir '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP
code (302)
+ "robots.txt" contains 36 entries which should be manually viewed.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3092: /sitemap.xml: This gives a nice listing of the site content.
+ OSVDB-12184: /index.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals
potentially sensitive information via certain HTTP requests that contain
specific QUERY strings.
+ /error_log: PHP error reveals file system path.
+ OSVDB-3092: /error_log: This might be interesting...
+ OSVDB-3268: /files/: Directory indexing found.
+ OSVDB-3092: /files/: This might be interesting...
+ OSVDB-3268: /imagenes/: Directory indexing found.
+ OSVDB-3092: /imagenes/: This might be interesting...
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3268: /logs/: Directory indexing found.
+ OSVDB-3092: /logs/: This might be interesting...
+ OSVDB-3092: /misc/: This might be interesting...
+ OSVDB-3092: /scripts/: This might be interesting... possibly a system shell
found.
+ OSVDB-3093: /modules/fckeditor/fckeditor/editor/dialog/fck_image.html:
FCKeditor could allow files to be updated or edited by remote attackers.
+ OSVDB-3093: /modules/fckeditor/fckeditor/editor/dialog/fck_flash.html:
FCKeditor could allow files to be updated or edited by remote attackers.
+ OSVDB-3093: /modules/fckeditor/fckeditor/editor/dialog/fck_link.html:
FCKeditor could allow files to be updated or edited by remote attackers.
+ OSVDB-3092: /UPGRADE.txt: Default file found.
+ OSVDB-3092: /install.php: Drupal install.php file found.
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3092: /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found.
+ OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found.
+ OSVDB-3093: /modules/fckeditor/fckeditor/editor/filemanager/browser/default/
frmupload.html: FCKeditor could allow files to be updated or edited by remote
attackers.
+ OSVDB-3093: /modules/fckeditor/fckeditor/license.txt: FCKeditor license
file found.
+ OSVDB-3093: /modules/fckeditor/fckeditor/fckconfig.js: FCKeditor JavaScript
file found.
+ OSVDB-3093:
/modules/fckeditor/fckeditor/editor/filemanager/browser/default/browser.html:
FCKeditor
could allow files to be updated or edited by remote attackers.
+ 6544 items checked: 0 error(s) and 62 item(s) reported on remote host
+ End Time: 2014-02-25 15:14:39 (GMT1) (1828 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
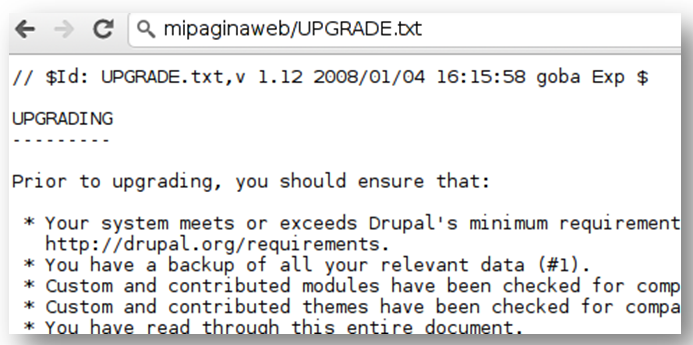
+ OSVDB-3092: /UPGRADE.txt: Default file found.
Simplemente visualizando este fichero vemos que se trata de una web hecha en Drupal
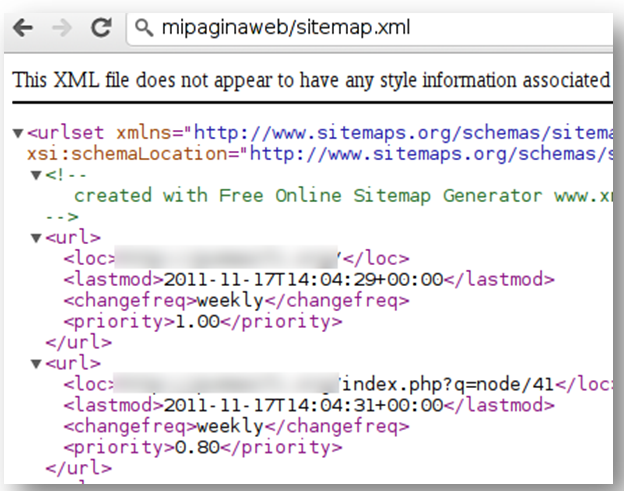
+ OSVDB-3092: /sitemap.xml: This gives a nice listing of the site content.
Podemos visualizar el sitemap, y hacernos con un mapa de la web:
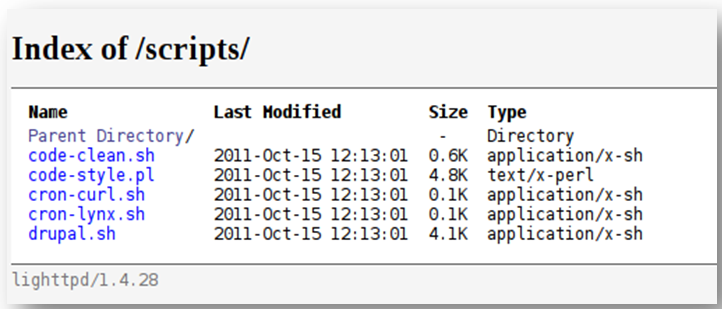
+ OSVDB-3092: /scripts/: This might be interesting… possibly a system shell found.
Nikto nos avisa de un directorio llamado scripts:
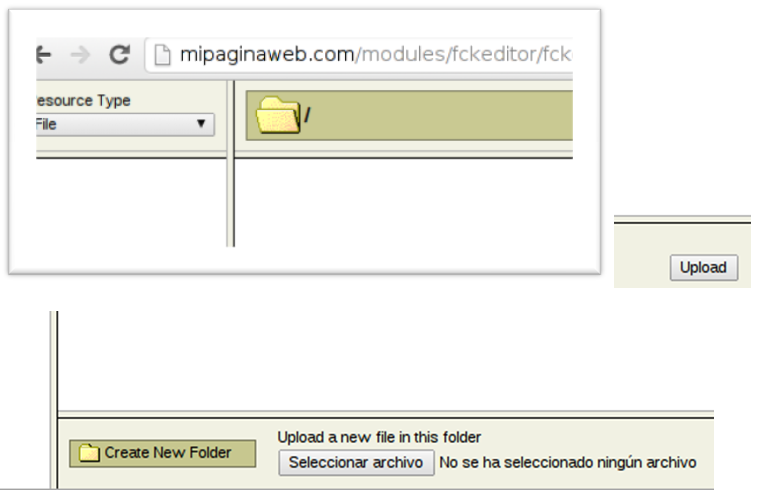
/modules/fckeditor/fckeditor/editor/filemanager/browser/default/browser.html
Y el uso de fckeditor que nos da la posibilidad de subir algo al servidor web:
Si miramos los log del servidor web vemos los rastros del escaneo:
root@debianWebserver:/var/log/lighttpd# cat error.log
2014-02-25 14:22:16: (connections.c.1718) SSL (error): 5 -1 104 Connection
reset by peer
2014-02-25 14:22:17: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:22:27: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:22:34: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:22:35: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:22:49: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:22:59: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:23:06: (request.c.1129) GET/HEAD with content-length -> 400
2014-02-25 14:23:07: (request.c.1129) GET/HEAD with content-length -> 400
[…]
cat /var/log/syslog
Feb 25 14:39:01 debianWebserver /USR/SBIN/CRON[15064]: (root) CMD ( [ -x /usr/
lib/php5/maxlifetime ] && [ -d /var/lib/php5 ] && find /var/lib/php5/ -type f$
Feb 25 14:42:40 debianWebserversuhosin[15060]: ALERT - ASCII-NUL chars not
allowed within request variables - dropped variable 'content_dir' (attacker '31.$
Feb 25 14:42:41 debianWebserversuhosin[15060]: ALERT - ASCII-NUL chars not
allowed within request variables - dropped variable 'content_dir' (attacker '31.$
Feb 25 14:45:40 debianWebserversuhosin[15060]: ALERT - ASCII-NUL chars not
allowed within request variables - dropped variable 'G_JGALL[inc_path]' (attacke$
Feb 25 14:45:46 debianWebserversuhosin[15060]: ALERT - tried to register forbidden
variable '_REQUEST' through GET variables (attacker '31.4.15.213', file $
Feb 25 14:45:46 debianWebserversuhosin[15060]: ALERT - tried to register forbidden
variable '_REQUEST[option]' through GET variables (attacker '31.4.15.213$
[…]
/usr/lib/php5/maxlifetime ] && [ -d /var/lib/php5 ] && find /var/lib/php5/ -type f$
Feb 25 15:17:01 debianWebserver /USR/SBIN/CRON[15092]: (root) CMD ( cd /
&& run-parts --report /etc/cron.hourly)
Las opciones son variadas, incluso Nikto se puede implementar con Nessus.

Juan, excelente tutorial para comprender con ejemplos simples el poder de Nikto.
Saludos
Hola Juan, excelentes ejemplos para complementar tu anterior artículo.
Gracias.
Perfect tutorial, sencillo, preciso, practico… buen trabajo.