(Editor’s note: this post was originally published in the Spanish version of Security Art Work on 1st July 2019)
Today we publish the first of three articles courtesy of Jorge García on the importance of server hardening. Jorge introduces himself as follows: “Although I am officially a systems administrator and responsible for security in the company where I work, the truth is that my job is also my hobby. I am a big fan of geek computing, defensive security, deploying my own servers and any DIY process that poses new learning challenges as I fend for myself to solve problems. Evolution is my passion.”
All companies, regardless of the field in which they are developed, have, to a greater or lesser extent, an IT infrastructure of servers that store and process corporate information of vital importance to the business. The question that always assails me is: if this information is so important, why does experience tell us that it is so frequent that companies do not keep their servers, applications and equipment updated and properly hardened?
It is well known that a large part of companies do not take computer security seriously. Without going any further this report published three months ago indicates that 7 of the 10 most exploited vulnerabilities during 2018 were between 1 and 6 years old; or this other report that indicates that a large number of companies do not patch their systems quickly. This is because, companies think that they are not targeted by hiding behind the typical “my company is small and has nothing attractive to hackers” thinking, or because they do not have or do not consider it necessary to have staff resources and tools to keep the platform updated. Or at least they don’t do it until it’s too late, and that’s what I’m going to talk about in today’s post. It’s a true story. Let’s go with a little background.
For some time now I have been managing in my spare time, among other things, an online trading infrastructure of a colleague who sells clothes online. The project was born after a conversation with the usual phrase “I need a website to make myself known and sell my products.” He asked me for advice and we were talking about the various options that exist for it. Basically the options were reduced to three:
- Contract the online commerce service to a company that offers you the USE of their application that they manage (what we call software-as-a-service (SaaS) -not to be confused with ñapa-as-a-service (ÑaaS), which is something else-). This approach is what we usually call «the cloud». As you can imagine, they charge you for it.
- Contract the infrastructure from a company that offers you the possibility of deploying your own store in its infrastructure (what we call infrastructure-as-a-service (IaaS)). That is, they give you the option to install and manage your own store in their infrastructure. Since the effort is less on your part, they charge you less than in the previous option.
- Install your own server in your office and deploy the store in it and, therefore, manage it yourself (what we call do-it-yourself (DIY) or on-premise solution). In this scenario you assume the costs of hardware and maintenance.
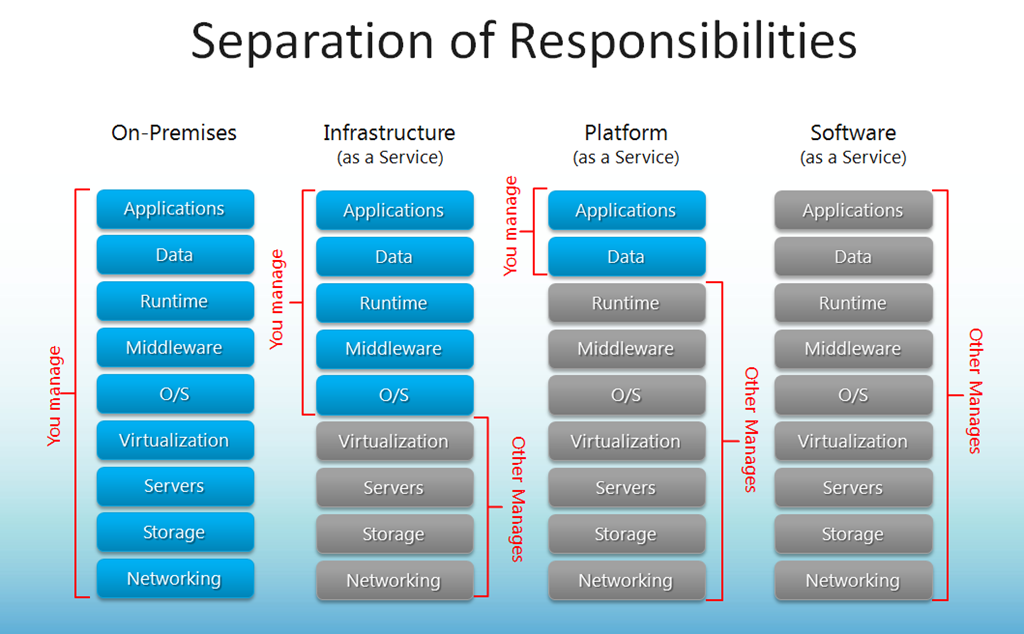
infographic Microsoft Technet
Which is better? Well, each approach is a different business model, although from a security perspective there are very important implications. It is true that for some time now there has been a general tendency for everything to be deployed in the cloud, since this brings with it many advantages, but also some drawbacks. Let’s look at the different options.
Option1: SaaS
The SaaS approach is one of the most comfortable for the customer. An example is the e-commerce solution offered by 1&1 Ionos, where you are provided with a user of a CMS application and you use it as it is.
In my case, my colleague would be given some keys to log into the store (remember, from another) and upload her products. Nothing else. There is no need to worry about updating the application or the server (we do have to check that someone else updates them) and there is no notion of what is underneath (if it is a Windows or Linux server, if it is a physical or virtual machine, etc.). In this approach, all that loses relevance in exchange for paying a monthly amount of money, generally fixed and relatively high.
On a security level, in my opinion, it poses some difficulties. Using another company’s application carries with it total confidence that the company providing the solution will keep the application and the system updated, but we cannot verify that. I personally don’t like it for this reason. In addition, they are usually shared servers where other applications that coexist in it can be vulnerable and the computer is more easily compromised. If we enter into legal issues, the company must ensure compliance with the GPDR if your business is going to store the personal data of EU customers, which usually happens, but not always.
As advantages, being solutions provided by large companies, these usually have very effective containment mechanisms for DDoS or brute force attacks, in addition to ensuring that the server will be active 24 × 7 because they have multiple datacenters where the store can be replicated. Another obvious advantage is that it does not require investment in initial nor maintenance hardware.
Option 2: IaaS
This approach is an intermediate solution for customers who want to have control over the operating system and application, but do not have the infrastructure to host the store on their own premises. An example of this are the services offered by Microsoft Azure, where you can install a store on a server that you manage, but it is hosted on the Azure infrastructure.It is not as economically expensive as a SaaS option, but it requires fairly advanced technical knowledge for server operating system installation and application configuration, as well as update management. We can say that you “outsource” the hardware and the costs of electricity and maintenance. For example, you don’t have to change a hard drive if it stops working or worry about the network falling out or a power failure.
Option 3: DIY
This option is the most traditional, where a physical or virtual server is available on our property and we deploy the store on it. It has the advantage that we control absolutely everything, from hardware to software, power supply, etc. You can also complement it with a firewall and with an IDS, all under your control.
It has the disadvantage that it requires a strong initial investment in hardware, especially for certain types of services that may require high-performance SSDs or a large amount of storage. It is a model that is usually profitable if you have a certain number of services to deploy (several web portals with several applications and databases, for example) and virtualization technologies such as Proxmox or VMware are used.
In the case at hand, after assessing the three options we decided that, since I already have a proprietary server with some services published on the Internet, we would take an intermediate path. From my perspective, it would be the DIY option, since I am the one who deploys the application on the server I already have, and I am in charge of updating and maintaining the operating system and the application. From my colleague’s perspective, this is the SaaS option, since I provide her with the credentials and she manages the content of the store, but she does not have permissions to manage it beyond the logistics of the business. In other words, we’ve taken the role of being her “supplier”.
What’s the relevance of this? It’s time to talk about responsability. From my perspective, I have a responsibility to ensure that both the application and the operating system are up to date and available. This is certainly a security challenge. It is one thing to offer my own services at my own risk, and quite another to offer them to third parties, but at my own the risk. To ensure that everything goes well, we must maximize the security of the server and apply as many measures as possible to reduce the vulnerable area. We will talk about this in the next parts of this article. Stay tuned!
