In the world of cybersecurity there is a widely known vulnerability known as Path Traversal, which can affect web servers, including Nginx servers. This represents a significant threat to the integrity and security of information.
What does it consist of?
This vulnerability allows an attacker to access and read files outside the designated root directory. Therefore, an attacker could manipulate file requests to reach resources that should not be accessible.
How is such a vulnerability exploited? This is achieved by manipulating directory paths in HTTP request URLs.
The following image shows an example of how the server’s passwd file would be accessed via the web. The “..” symbols indicate the number of directories between the files shown on the web and the location of the server’s root folder.
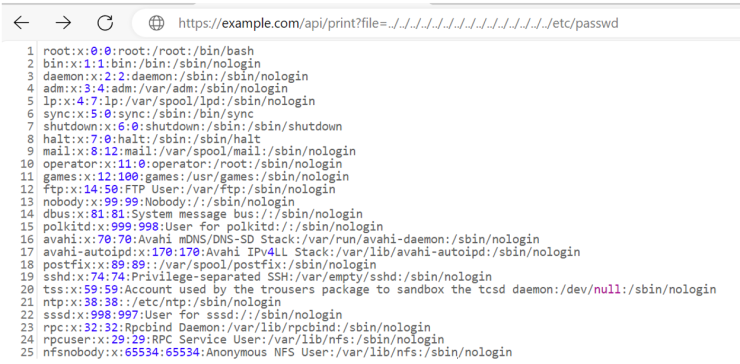
Impact on Nginx Servers
On Nginx servers, regardless of the version installed, the vulnerability can be caused by several reasons: an incorrect configuration of the “location” directive, a lack of input data validation or the presence of inappropriate permissions.
We will explain the case in which the vulnerability is caused by an incorrect configuration of the “location” directive. This defines how the server will respond to requests that match a certain URI pattern. That is, it allows you to configure how Nginx will handle requests for specific resources on the web server.
For example, to specify the location of the images, you would define a location directive “/images/” where you would specify in which path on the server they are located, while the URI would only be indicated as follows:
- https://example.com/images/nombre_de_la_imagen.jpg
In the following image you can see how it would look like:

Unauthorized file access can lead to unauthorized access to sensitive information, such as the history of executed commands, users, passwords, etc.
In addition, depending on the access configuration, it could pose a risk to the integrity of information as an attacker could attempt to modify critical files, causing interruption of services, unrecoverable data loss or manipulation of information for malicious purposes.
Mitigation and prevention
Several factors must be taken into account when configuring a web server:
- Maintain a secure configuration: the specifications and documentation of the software being installed must be taken into account.
- Regular software updates: regardless of the technology used, try to keep updates up to date as much as possible.
- Input filtering and validation: it is recommended to implement input data filtering and validation measures to prevent attackers from manipulating HTTP requests and accessing unauthorized resources.
- Regular security audits: it is necessary to know how an attacker’s activity could impact a company, so simulating a real scenario is the most effective way to maintain information security.
- Staff education and awareness: employees must be knowledgeable and trained to identify possible attacks when they happen, as they are the first target for an attacker.
