
In the dynamic and ever-changing cybersecurity environment, staying ahead of threats is more crucial than ever.
At S2 Grupo, in collaboration with the National Cryptologic Center (CCN), we have developed and continuously improved CARMEN, an innovative tool designed to protect organizations against the most sophisticated threats.
What is CARMEN?
CARMEN (Center for Log Analysis and Data Mining) is a comprehensive threat detection and response solution specifically designed to address the evolution of Advanced Persistent Threats (APTs). This tool is fundamental for Threat Hunting processes, allowing security teams to proactively identify and neutralize risks.
CARMEN’s main objective is to generate intelligence from network traffic and user activities within the organization, filtering and prioritizing critical information. In this way, it helps prevent security breaches and mitigate the impact of cyber-attacks. With CARMEN, organizations achieve full visibility of their infrastructure, facilitating both early threat detection and an agile and effective response.
Advantages of CARMEN
- Real-time identification: Detects attacks instantly, providing a clear and detailed view of suspicious activity within the infrastructure.
- Proactive defense: Provides advanced capabilities to address a wide range of cyber threats, deeply analyzing intrusion and persistence stages.
- Machine learning: Employs advanced algorithms to identify patterns and anomalous behavior, increasing detection accuracy and effectiveness.
- Immediate response: Allows to act quickly at any sign of attack, minimizing damage and reducing the time of exposure to risks.
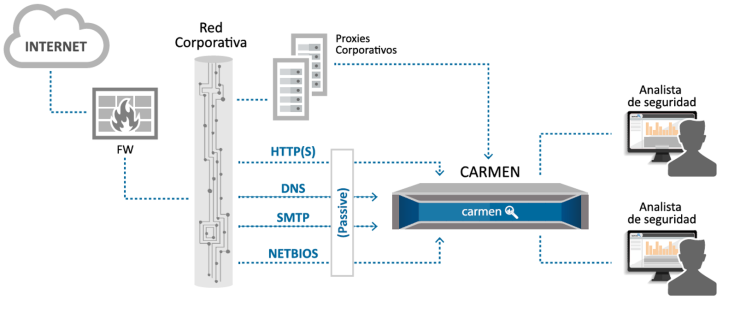
Traffic analysis with CARMEN
CARMEN stands out for its ability to acquire, process and analyze network traffic in both Information Technology (IT) and Operational Technology (OT) environments to detect anomalies or misuse.
The analysis is performed passively (by sniffing and protocol dissection) or by receiving logs, normalizing and storing the data for further analysis.
Types of traffic analyzed by CARMEN:
In IT environments:
- HTTP/HTTPS: Secure data transfer protocols on the web.
- DNS: Domain name resolution.
- SMTP: Sending and receiving e-mails.
- ICMP: Network diagnostics and control.
- NetFlow: Traffic pattern monitoring.
The integration of CARMEN with the CLAUDIA agent allows the former to capture and process user traffic and events in Windows, offering an even more detailed analysis of what is happening in the organization.
In OT environments:
- MODBUS: Communication in SCADA systems.
- PROFINET: Real time industrial automation.
- MQTT: Light messaging in IoT.
- ICCP: Communication between control centers in electrical networks.
- IEC 104: Telecontrol in automation systems.
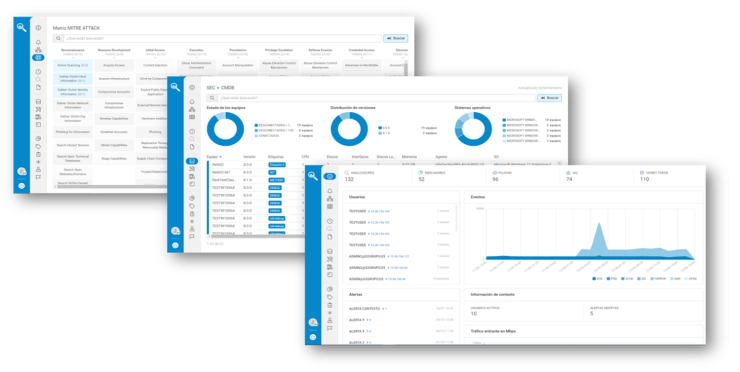
Upcoming enhancements: CARMEN 8.0
We are excited about the imminent release of CARMEN 8.0, scheduled for later this year. This new version will bring significant enhancements:
- New visual design: A more modern and attractive interface that optimizes the user experience.
- Unification of events: Event monitoring on a single screen for more efficient tracking.
- MITRE ATT&CK Matrix: Improved threat understanding and responsiveness.
- DQL search engine: Complex and detailed queries for faster incident detection.
Why choose CARMEN?
Although it may seem that my opinion is not completely objective as I am part of the team behind CARMEN, the reality is that this tool is essential for any organization looking to strengthen its cybersecurity. Particularly suitable for those that manage large volumes of information or have a high exposure to cyber-attacks due to their sector, criticality or size, CARMEN stands out for its ability to detect and respond effectively to the most sophisticated threats. This makes it one of the most robust and comprehensive solutions available on the market to protect the digital security of organizations.

Speak Your Mind