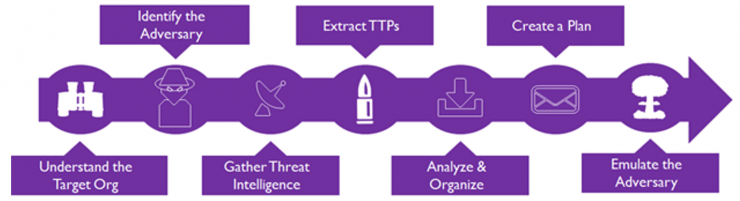
As you can already guess from previous spoilers, in this third part of the series (see part one and part two), after having made clear the role that Threat Intelligence plays in the Purple Team methodology, we will go a bit more into details about the phases of preparation, execution and lessons learned in an exercise.
Disclaimer: As I mentioned in the first episode, I do not intend to set in stone anything in this article, but rather to give my point of view and provide an overview of a subject for which there is not much documentation, and what I found, is scattered in multiple sources.
After having developed an implementation plan based on the mapping of threats on the MITRE ATT&CK MATRIX, it is time to put all the use cases into practice. To do so, we will use Vectr.io, an open source web platform developed by Security Risk Advisors.
This tool is responsible for centralizing all the coordination tasks of the Red and Blue teams. But far from being a tool just for coordinating exercises, it is also prepared to be used as a sort of logbook of all operations executed in various exercises and their outcome over time, so that the evolution of the organization’s security posture can be tracked.
With an abstract description such as the above, it may be difficult to imagine how all of this is accomplished. Therefore, the aim of this post is to opt for a more practical approach.
For the sake of brevity, we will not detail all the functionalities of this tool but will show the possibilities it offers and how these can help us with our goal. It will then be up to you to explore the more advanced functions and evaluate whether they are useful for your particular use case.
[Read more…]