Recently an old acquaintance has returned to his old ways. This is the Ransomware “Locky”, which about a year ago was very active through #Malspam campaigns (Spam Mail with the purpose of installing malware in the victim’s system) mostly with scripting files such as “.js “,” .wsf “or” .vbe “. Since then it has continued to maintain activity, although to a lesser extent.
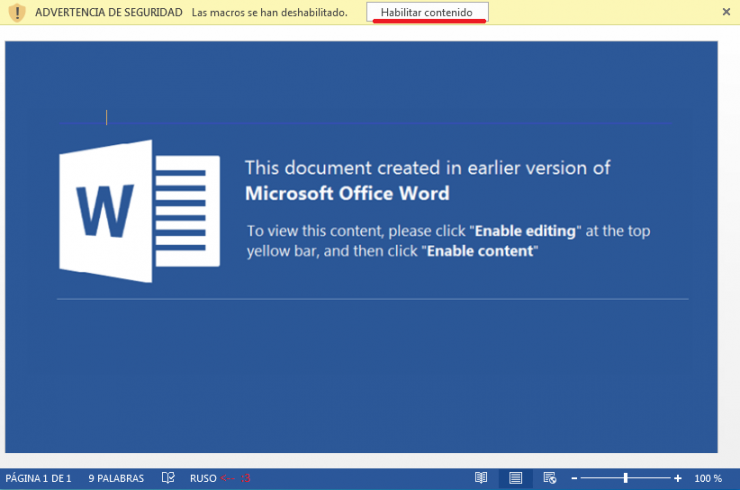
Recently they have started a new campaign in which they use .doc (MSOffice Word) files with macros, like the following:
Droppers from Locky Ransomware with extra anti-Sandboxing
Malware Trends. December 2016
During this month of December we have observed from the malware laboratory of S2 Grupo various threats that we once again wanted to share with you. In this type of entries we will find known threats, seen in other sources or analyzed directly in our laboratory, but the goal of the post is to know what kind of threats have been active throughout this last month.
Here is a diagram with the information collected this month from the lab:
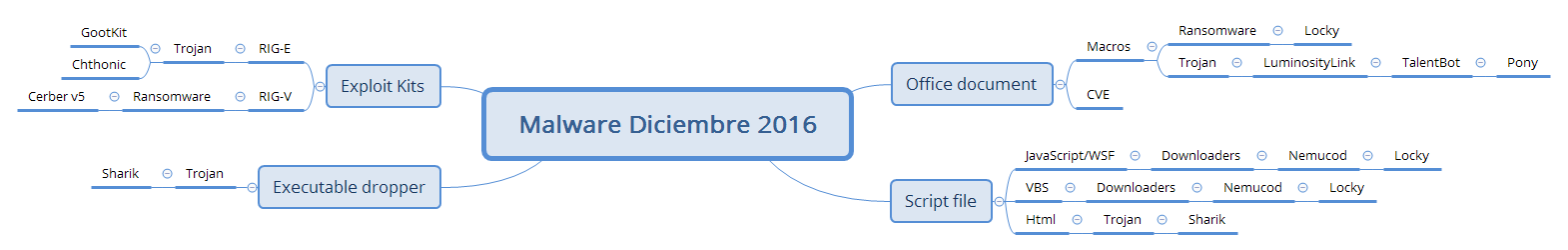
First of all, we would like to highlight the break that Locky has at least given us this month, with a tremendously reduced SPAM compared to the previous two months. This does not mean at all that it has disappeared, rather, many have been arriving at emails with texts of “subject:” such as the following: [Read more…]