As you now, the DHS (Department of Homeland Security) along with the ODNI (Office of the Director of National Intelligence) formally accused Russia of meddling in the past US presidential elections with techniques from the burning information warfare and various cyberattacks. Let’s take a (somewhat delayed) look at this.
 It is not the first time that USA launches accusations of this caliber, it did so when it accused China of stealing trade secrets in 2014. An accusation of this kind could involve, officially or unofficially, attacks on Russian IT infrastructures that posed a headache for Putin and his allies. According to statements in the NYT taking this type of action would involve too much risk with elections less than a month away; cyberattacks by a power like Russia against the US electronic voting system could wreak havoc. It should also be noted that the electoral system is still not considered a critical infrastructure of the nation, although it may increase their criticality shortly.
It is not the first time that USA launches accusations of this caliber, it did so when it accused China of stealing trade secrets in 2014. An accusation of this kind could involve, officially or unofficially, attacks on Russian IT infrastructures that posed a headache for Putin and his allies. According to statements in the NYT taking this type of action would involve too much risk with elections less than a month away; cyberattacks by a power like Russia against the US electronic voting system could wreak havoc. It should also be noted that the electoral system is still not considered a critical infrastructure of the nation, although it may increase their criticality shortly.
[Read more…]
(Cyber) III Cold War: Hack the vote?
Abusing corporate webmail for C&C and exfiltration
Let’s assume an organization that has basic security measures: workstations cannot make direct connections to the Internet, only being able to carry out web requests through a proxy server, which is also the only one that can make external DNS queries.
HTTP and DNS traffic generated by this proxy server are properly monitored, and the proxy “breaks” HTTPS, so techniques like the domain fronting can also be detected. Only a few whitelisted websites are accessible. [Read more…]
TLS client fingerprinting with Bro
In this post, we will play with Bro IDS as a client fingerprinting techniques exploration tool.
As is known, during the initial TLS handshake (used, among others, by HTTPS on web browsers), a message called ClientHello is exchanged. In this message, the client specifies the supported cryptographic primitives (the so-called cipher suites).
For example, Firefox 50.1.0 under Linux sends a ClientHello like this, as shown with the Wireshark dissector: [Read more…]
Simple domain fronting PoC with GAE C2 server
In this entry we continue with domain fronting; on this occasion we will explore how to implement a simple PoC of a command and control and exfiltration server on Google App Engine (GAE), and we will see how to do the domain fronting from Windows, with a VBS or PowerShell script, to hide interactions with the C2 server.
The goal
When we have everything ready, we will have a webservice at myc2server.appspot.com which we can use from a compromised Windows machine in the following way; we will have a command and control channel (on the path /e2e7765b71c1, as an authenticator):
[Read more…]
Camouflage at encryption layer: domain fronting
In today’s post we are goint to talk about a somewhat old technique (although programs like Signal have recently started using it) that I have always found to be a really clever hack:
domain fronting.
For example, let’s take the IP address of the frontal that serves www.google.es:
$ host www.google.es www.google.es has address 216.58.210.227
If we take a look at the Common Name (CN) field of the TLS certificate returned by the server: [Read more…]
Malware Trends. December 2016
During this month of December we have observed from the malware laboratory of S2 Grupo various threats that we once again wanted to share with you. In this type of entries we will find known threats, seen in other sources or analyzed directly in our laboratory, but the goal of the post is to know what kind of threats have been active throughout this last month.
Here is a diagram with the information collected this month from the lab:
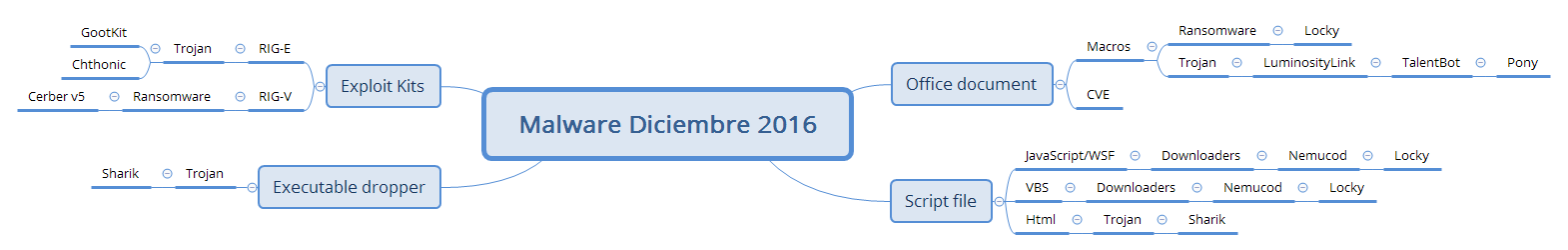
First of all, we would like to highlight the break that Locky has at least given us this month, with a tremendously reduced SPAM compared to the previous two months. This does not mean at all that it has disappeared, rather, many have been arriving at emails with texts of “subject:” such as the following: [Read more…]
The Russian ICC (V): FSB

As we have indicated in previous posts, the FSB (Federal’nya Sluzhba Bezopasnosti) is the main heir of the KGB and the FAPSI; directed by Army General Alexander Bortnikov, whose breadth of responsibilities and power in Russia are undoubtedly marked by Vladimir Putin himself, a former director of the Service who, upon becoming President of the country, greatly strengthened the capabilities of the FSB -and its budget- as well as the presence of former Service members in the whole of Russian society. The FSB not only works in areas directly associated with intelligence and counterintelligence, but also reaches aspects such as social or electronic surveillance.
Regarding the cyber domain, the FSB has a wide range of technical and regulatory powers: although it is a service dedicated to internal intelligence, it has authorization for external intelligence actions, theoretically coordinated with the SVR. Among others, he is responsible for the security of information at the federal level, something similar to a police force to use or at least to the Information Services -with the corresponding name in each case- of a police force. In this area it has the attributions – and obviously, capacities – SIGINT operative for the interception of communications in the State: since 1995, it has the legally constituted right to monitor telephone lines, open mails and monitor Internet traffic ([1]). The FSB operates the system called SORM for this purpose, to which Russian Internet service providers must facilitate the work by deploying capabilities that they must also pay out of pocket. This system is operated by an FSB group initially designated UKIB (Computer & Information Security Directorate), Directorate R, heir to the KGB and focused especially on the fight against cybercrime and terrorism. The successor of this Directorate is the Information Security Center (CIS) of the FSB, framed in the Counterintelligence Directorate (SKR), the Second Directorate of the FSB and also identified as the Military Unit (VCH) 64829 or the Center number 18. SORM, which we will speak about in other posts as an example of “collaboration” of companies with the Russian intelligence services, deals, like the FSB mainly does, with the interception of data in the “Russian Internet”, where CIS is responsible for surveillance and counterintelligence, also working closely with Directorate K of the Russian Ministry of the Interior, responsible for combating cybercrime ([2]).
A priori, these CIS surveillance and counterintelligence capacities should be focused on Russia, without directly impacting the outside of the country; however, even though the FSB and within it the CIS are focused on inner intelligence, its actions may be directed against that focus but against Russian interests outside its borders, including elements considered to be disturbing according to Russian criteria (this may include attack on terrorist objectives … or simply political) and even with police powers of investigation and prosecution of such elements.
The Center for Electronic Communications Surveillance (TsRRSS), identified as FSB unit 71330 and focused on ELINT, has electronic spying and cyberespionage capabilities (communications interception, decryption …). This Center (number 16) is hypothetically the main offensive capability of the FSB, including operations outside Russia, as opposed to groups such as the CIS, described above and focused especially on defensive and surveillance tasks. Its internal structure is classified, and its responsibilities include the operation and processing of electronic communications.
The Center for Special Communications and Information Protection (TsBISS) provides the FSB with protection against cyberattacks or third party intrusions. From this Center, there have been peculiar (or interesting) initiatives such as the request to prohibit services such as GMail, Hotmail or Skype in Russia, as their use may constitute a threat to national security. A comment by the Center’s director in 2011 which caused a great stir at the time in social networks but that, much more interesting than the relative turmoil on the privacy and freedom of the users, was the moment in which it was published, marked by facts as transcendent as Arab spring or the Russian legislative elections.
Another interesting group in the cyber environment within the FSB is the Communications Security Center (CBS FSB, Vch 43753), which is part of the Eighth Service Directorate and is responsible for the logical protection of government communications through product accreditation and certification of safety standards, a kind of equivalent to the Certification Office of the Spanish CNI. Also in this sense, TSLSZ (translated approximately as Center for Licensing, Certification and Protection of State Secrets) is the branch of the FSB in charge of enabling organizations to handle classified information, in this case something similar to the attributions of The National Security Office in the CNI.
Finally, as a group with no offensive capabilities, cyber training activities within the FSB are the responsibility of the Institute of Cryptography, Telecommunications and Information Technology (IKSI), in the Service Academy, which trains specialists in cybersecurity not only for the FSB but also for other Russian Services… or for industry.
To try to summarize this structure, a summary table of the main groups or centers directly related to SIGINT or CNO dependent on the FSB is shown below:
| Center | ID | Unit | Function |
|---|---|---|---|
| Center for Information Security | FSB CIS | 64829 | SORM. Search and surveillance |
| Center for Electronic Surveillance of Communications | FSB TSRRSS | 71330 | Attacking capacity/td> |
| Centre for the Security of Information and Special Communications | TsBISS | N/A | Defense against foreign intrusions |
| Communications Security Center | FSB CBS | 43753 | Accreditation of products and services |
| Center for Licensing, Certification and Protection of State Secrets | FSB TSLSZ | N/A | Security clearance |
| Institute of Cryptography, Telecommunications and Computer Science | IKSI | N/A | Training |
Referencias
[1] Roland Heickerö. Industrial Espionage and Theft of Information. In Proceedings of the 14th European Conference on Cyber Warfare and Security. Nasser Abouzakhar (Ed.). University of Hertfordshire. Julio, 2015.
[2] Taia Global. Russian Federal Security Service (FSB) Internet Operations Against Ukraine. Taia Global, 2015.
The good news from Yahoo
 Yahoo has just acknowledged the theft of information relating to more than 1 billion customer account … in 2013. Yes, 3 years ago.
Yahoo has just acknowledged the theft of information relating to more than 1 billion customer account … in 2013. Yes, 3 years ago.
Faced with this situation, different interpretations can be found: either because of the analysis of the incident they suffered in 2014, which they reported in September they have extended the forensic analysis of what happened backwards and have discovered that in 2013 they had suffered the largest information theft ever suffered by a single company, or they already knew it and have decided to report it now before the news leaked out through another source. I can even think of a third possibility (and maybe even one of you could think a fourth): that it was a malicious leak now that Verizon is formalizing a bid for Yahoo.
[Read more…]
The Russian ICC (IV): A bit of history: FAPSI
 When talking about Russia in the area of cybersecurity or, more specifically, information warfare, we must by force mention the FAPSI (Federal Agency of Government Communication and Information), operative between 1991 and 2003 and considered the Russian equivalent to the US NSA (Roland Heickerö, Emerging Cyber Threats and Russian Views on Information Warfare and Information Operations. FOI. Swedish Defense Research Agency, March, 2010.), which inherited the attributions and capabilities of the 8th (encrypted) and the 16th (Decryption and interception) General Directorates of the KGB. Among its functions there was the figure (cryptology and cryptanalysis), the interception of communications and even the incident response capabilities as a CERT. In 2003 this powerful agency was dissolved by the Russian government, possibly because of corruption, although it also shows that an agency with more than 50,000 people was becoming a great uncontrollable monster, as it was with the KGB at the time. After transforming the Special Information and Communications Service, an agency heir to the FAPSI that lasted only five months, its attributions were distributed among the four large Russian services, the GRU and the KGB derivatives: SVR, FSB and FSO. Each of these services has different attributions, although they obviously share capabilities, information, tactics or interests … or compete among them. In fact, in his Putin’s Hydra: Inside Russia’s Intelligence Services, and European Council on Foreign Relations, May 2016, Mark Galeotti presents us with a curious graphic summary of the roles of the Russian intelligence community, from which we then select only the main services – at least in our cyber sphere:
When talking about Russia in the area of cybersecurity or, more specifically, information warfare, we must by force mention the FAPSI (Federal Agency of Government Communication and Information), operative between 1991 and 2003 and considered the Russian equivalent to the US NSA (Roland Heickerö, Emerging Cyber Threats and Russian Views on Information Warfare and Information Operations. FOI. Swedish Defense Research Agency, March, 2010.), which inherited the attributions and capabilities of the 8th (encrypted) and the 16th (Decryption and interception) General Directorates of the KGB. Among its functions there was the figure (cryptology and cryptanalysis), the interception of communications and even the incident response capabilities as a CERT. In 2003 this powerful agency was dissolved by the Russian government, possibly because of corruption, although it also shows that an agency with more than 50,000 people was becoming a great uncontrollable monster, as it was with the KGB at the time. After transforming the Special Information and Communications Service, an agency heir to the FAPSI that lasted only five months, its attributions were distributed among the four large Russian services, the GRU and the KGB derivatives: SVR, FSB and FSO. Each of these services has different attributions, although they obviously share capabilities, information, tactics or interests … or compete among them. In fact, in his Putin’s Hydra: Inside Russia’s Intelligence Services, and European Council on Foreign Relations, May 2016, Mark Galeotti presents us with a curious graphic summary of the roles of the Russian intelligence community, from which we then select only the main services – at least in our cyber sphere:
[Read more…]
The Russian ICC (III): the Community
Undoubtedly, many people mentally associate intelligence or Russian secret services – to be exact, Soviet – to the KGB (Komitet gosudárstvennoy bezopásnosti, Committee for State Security). Unfortunately for the followers of Bond, the KGB, the Soviet-Russian secret service par excellence, was dismantled at the beginning of the 1990s by Mikhail Gorbachev, probably because he had become a powerful monster in terms of attributions, skills and knowledge, but, especially for its alleged involvement in the failed coup d’état of August 1991. Its power was distributed mainly among three different agencies: FSB (Federal Security Service), SVR (Foreign Intelligence Service) and FSO (Federal Protection Service), who joined the historical rival of the KGB, the GRU (General Intelligence Directorate), the Russian military intelligence service that survived the fall of the USSR (perhaps because of the support for the Soviet president during the coup, unlike the KGB). SIGINT attributions focused on an agency called FAPSI, equivalent to the US NSA, dismantled in 2003 and whose power, as in the KGB, was distributed among the different Russian services.
 After the dismantling of the FAPSI, the four services listed above make up the bulk of the Russian intelligence community from the cyber point of view-at least the official one, as we will see in this series of posts. An excellent description of this intelligence community, as far as information security, SIGINT or CNO is concerned, can be found in chapter fifteen of the second edition of Jeffrey Car’s Inside Cyber Warfare: Mapping the Cyber Underworld (ed. O’Reilly, 2011).
After the dismantling of the FAPSI, the four services listed above make up the bulk of the Russian intelligence community from the cyber point of view-at least the official one, as we will see in this series of posts. An excellent description of this intelligence community, as far as information security, SIGINT or CNO is concerned, can be found in chapter fifteen of the second edition of Jeffrey Car’s Inside Cyber Warfare: Mapping the Cyber Underworld (ed. O’Reilly, 2011).
To get an idea of the potential of Russian services it is necessary to talk about their budget. According to open sources (such as Julian Cooper’s The Funding of the Power Agencies of the Russian State. The Journal of Power Institutions in Post-Soviet Societies, Issue 6. 2007, or The Funding of the Power Agencies of the Russian State: An Update, 2005 to 2014 and Beyond. The Journal of Power Institutions in Post-Soviet Societies. Issue 16, 2014), in 2013 the budget for what the Russians call “Security Services” – a concept that includes the FSO, FSB (except the Border Service) and SVR – exceeded 4 billion euros. The distribution by service is classified, and obviously the budget of the GRU is included in the one corresponding to the Russian Ministry of Defense, with which it is completely unknown. This money joins the more than 300,000 people who work – again, classified data – in the different intelligence services.
To be able to compare these data with other services, here’s a curiosity: the budget corresponding to the CNI is estimated at about 240 million euros, seventeen times less than the Russian one, and its number of employees at about 2,500 people. Of course, comparisons are odious…
