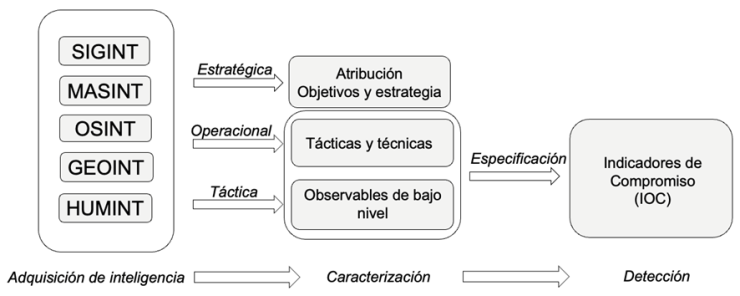
Maritime transport is a fundamental pillar of the global economy and, like any system adopting new connectivity technologies, it is subject to cybersecurity risks. In the article “New cybersecurity requirements in shipbuilding: implications in the engineering process and designs of new ships“, we commented on the increasing connectivity of new ships, as well as the low maturity of cybersecurity in this area and the common problems encountered in their systems. These characteristics, together with the increase in cyber-attacks, are driving the creation of mandatory standards and certifications for new ships. However, the problems are not just procedural. Let us look at one of the most important technical aspects, maritime communication protocols.
To recap the previous post, the common issues in the maritime domain lie in factors such as reliance on network isolation and physical security, coupled with long system lifetimes and a focus on availability. These characteristics are reflected in the way ships are designed and operated, from general aspects such as architectures to specific aspects such as communication standards. In this article, we analyse the most commonly used maritime protocols today in terms of their security and the risk of being affected by some of the most common types of cyber-attack.
Maritime network protocols are the communication standards that define the rules, syntax and procedures for internal communication between ship systems and ship-to-ship communication. As in other fields, international associations such as NMEA (National Marine Electronic Association) have worked to establish standards that are used by all manufacturers.
read more