Series entries: First part, Second part, Third part, Fourth part, Fifth part
[Editor’s note: Clicking on many images – those whose detail is not fully visible with the size of the main page – shows an enlarged version]
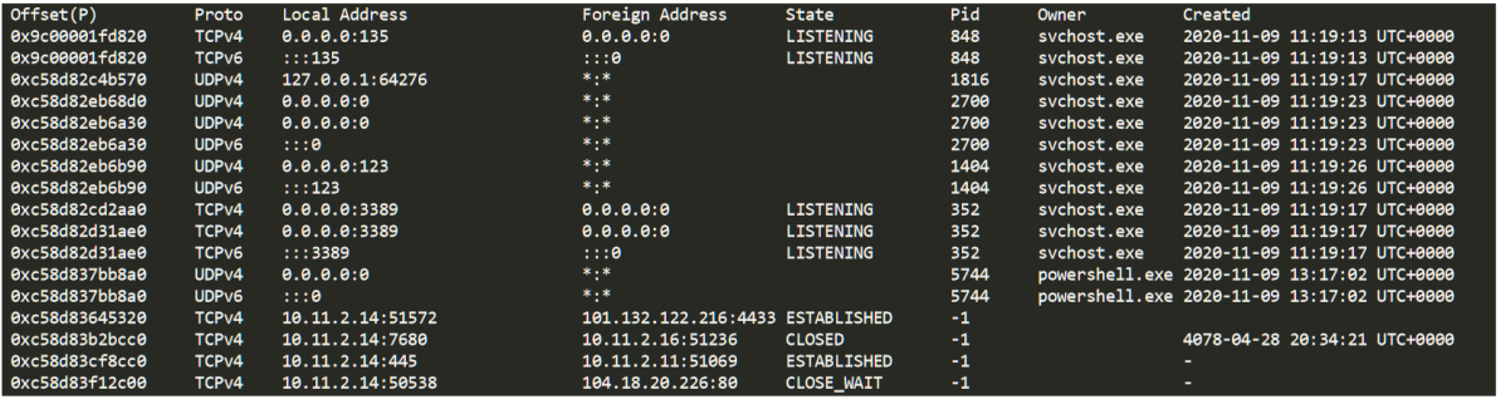
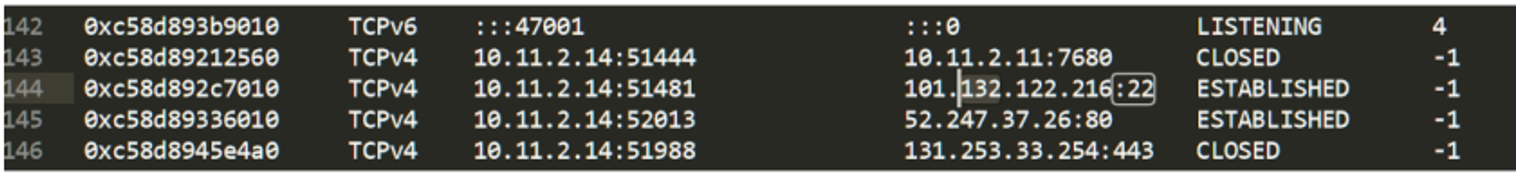
In the previous article we saw how Angela had deduced that the attackers had entered the computer used to connect to the DC from another computer using the PsExec tool. Determined to find the PsExec, Angela begins by converting the MFT extracted by CyLR with mftdump.exe to .csv, and searching for activity around the time she saw the connection on the other computer (about 2:16 p.m. 1:16 p.m. in UTC which is what the MFT shows us).
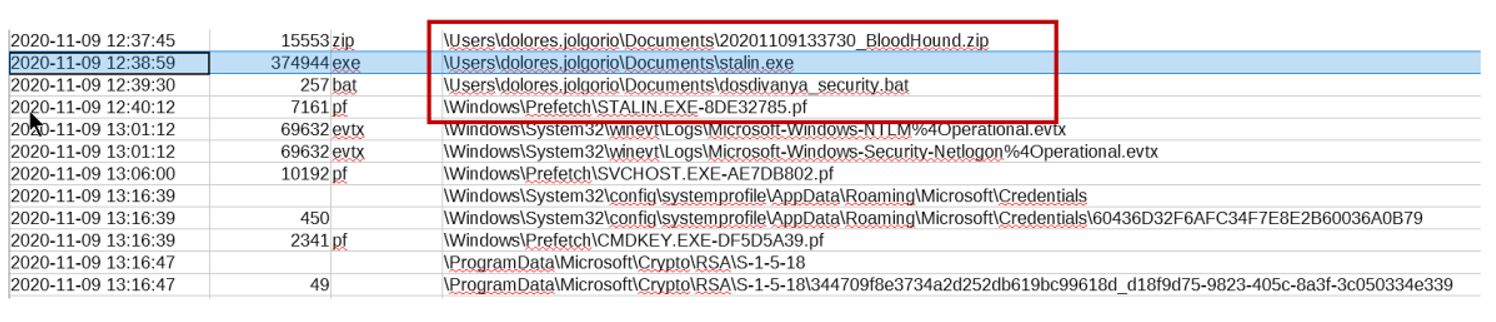
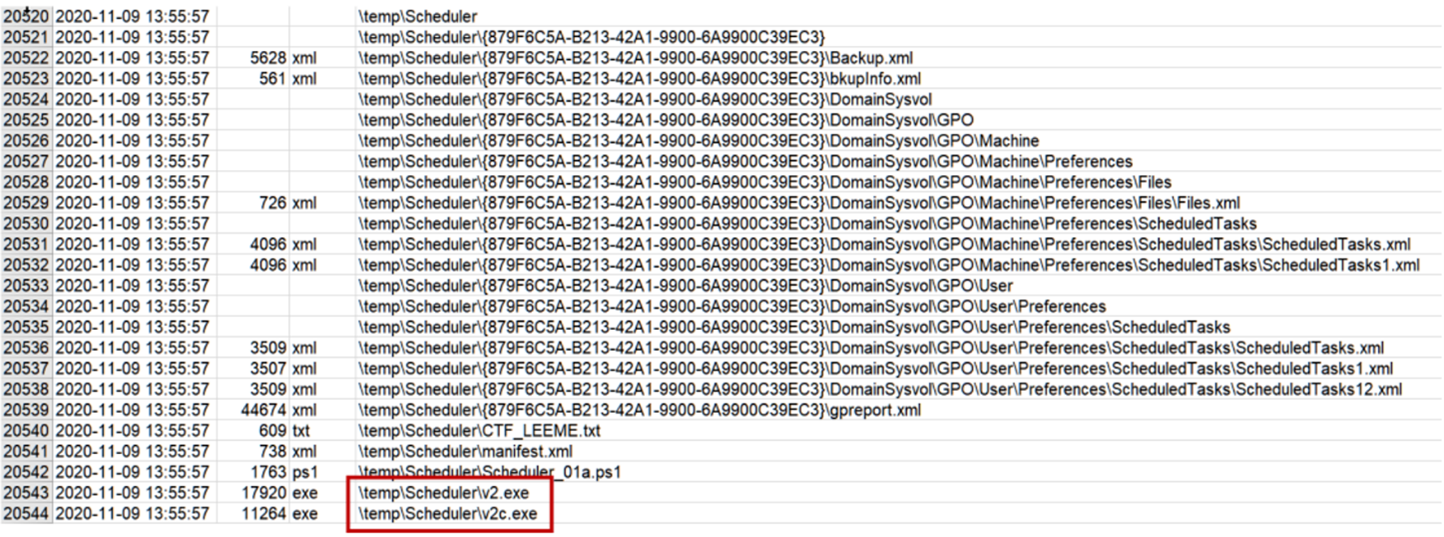
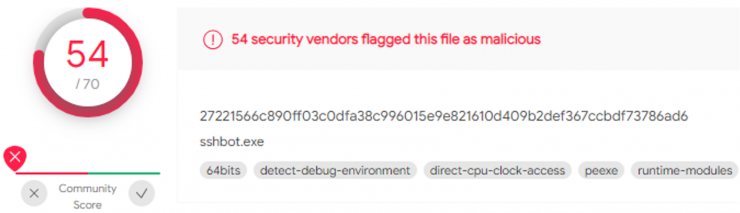
There is no clear target, but that stalin.exe Prefetch looks suspicious (remember that Prefetches are created the first time the software is run, with a delay of a few seconds).
[Read more…]