Continuing this series of posts related to the cloud, it’s time to talk about how to face the world of possibilities that the cloud offers. This article aims to shed some light on such a huge task and to show different aspects to be taken into account. It is an interesting path, with multiple options, which can bring enormous value both to the business and to our quality of life, as long as it is approached from an objective, realistic and critical point of view. We should not be reticent to change, but neither should we apply change for change’s sake.
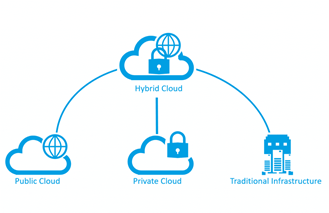
Leaving philosophical mantras aside, saying that the cloud is the panacea makes as little sense as saying that the cloud does not bring value to the business.
As always, and sorry for the insistence, it will depend on each organization and its needs. What is fundamental, within the analysis of the business case and in calculating the return on investment of the implementation of these new technological paradigms, is that the consequences, needs and capabilities of security are considered. Both in the process of migration to the cloud, as well as in the face of any technological change.
Having said this, and getting to the point, there is no doubt that migrating to the cloud has a significant cost. Whether this cost is greater or lesser will depend on how you compare, but it can be said that it is not a “cheap” decision. If we do the simple exercise of comparing a physical server to a cloud server, the difference is fairly clear. However, putting everything into context, and above all, emphasizing security, there are many other costs to be assessed.
[Read more…]